Overview
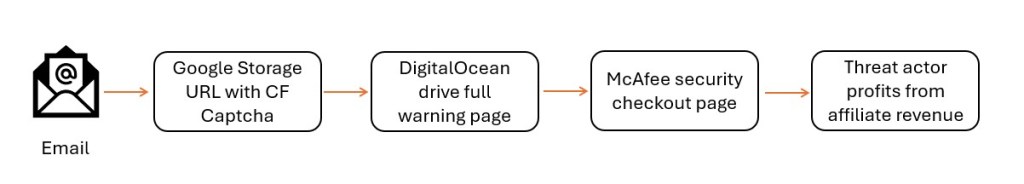
While actively hunting for phishing site, I came across multiple web pages impersonating PNB MetLife Insurance and presenting themselves as official policy premium payment gateways. This activity highlights how scammers deliberately target reputed and widely trusted brands to exploit existing customer trust and increase the likelihood of successful financial fraud. Although the pages claim to offer legitimate premium payment and policy servicing options, analysis of the underlying HTML and JavaScript shows that no real payment processing or backend validation is involved at any stage.
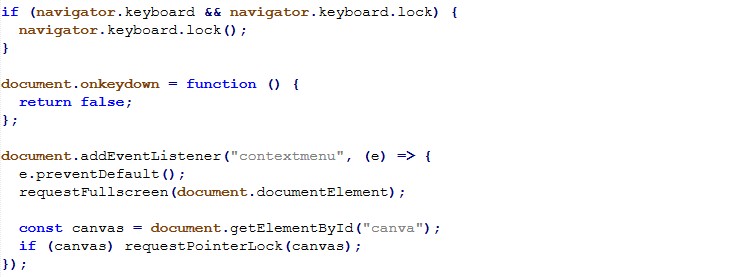
The pages are optimized for mobile devices, both in layout and interaction design. This strongly suggests that victims are likely being lured via SMS messages, although delivery via email, social media platforms, or messaging apps cannot be ruled out.
Fake PNB MetLife Payment Gateway – Initial Landing Page
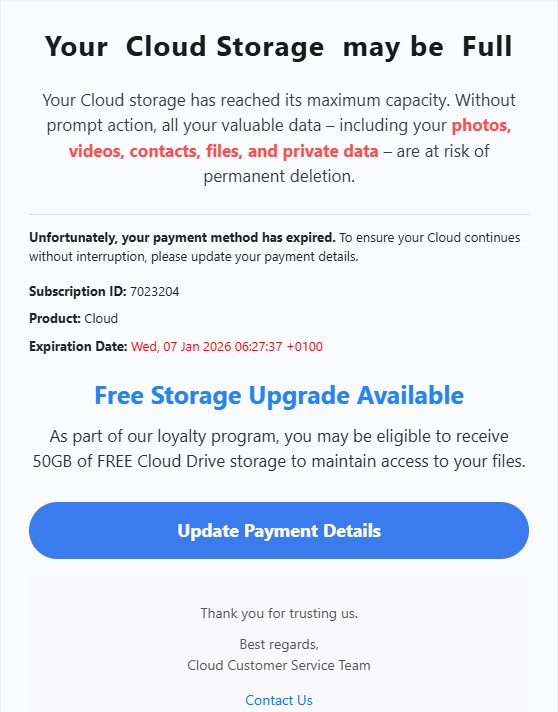
The first template presents a mobile-friendly page branded as “PNB MetLife Payment Gateway”. It immediately prompts users to enter their name, policy number and mobile number, claiming these details are required to proceed with premium payment.
What is immediately noticeable is that the page does not validate any of the entered information. Any arbitrary values are accepted, and the user is allowed to proceed to the next step without verification.
hxxps://pnb-metlife-g-shiv-1aad8zgyup.edgeone.app/
Stealthy Data Exfiltration via Telegram Bots
Once the user submits the first form, the entered details are silently exfiltrated using the Telegram Bot API. Instead of communicating with a legitimate payment backend, the page sends captured information directly to Telegram, where it can be monitored in real time by the attacker.
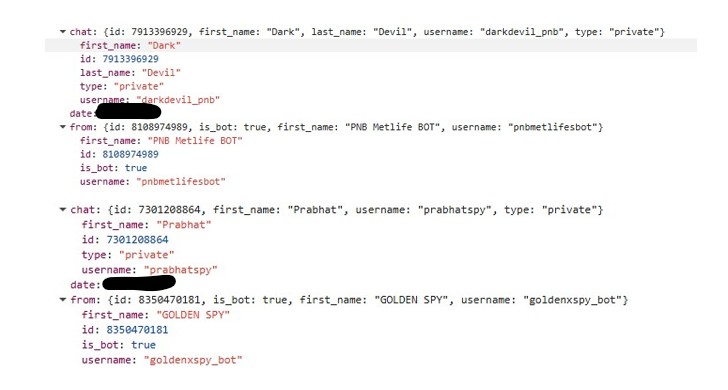
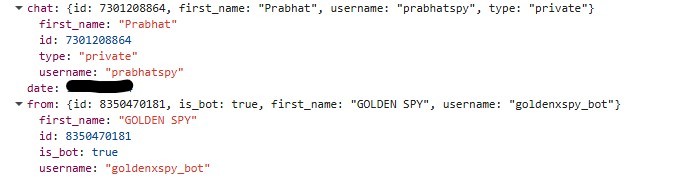
The stolen data includes the victim’s name, policy number, and mobile number. Hardcoded Telegram bot tokens and chat IDs are embedded directly in the page’s JavaScript, leaving no ambiguity about the intent of the page.
During investigation, multiple Telegram bots and operator accounts were observed across related samples. Bots such as pnbmetlifesbot and goldenxspy_bot are used to collect victim data, while operator accounts including darkdevil_pnb and prabhatspy appear to receive and monitor these submissions.
Payment Amount Collection and Transition to UPI Flow
After the initial data theft, victims are taken to a second page asking them to enter the payment amount. Again, there is no backend validation or policy lookup. Any amount can be entered, and once submitted, this value is also sent to Telegram.
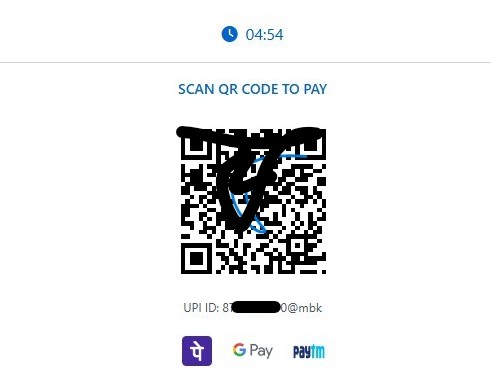
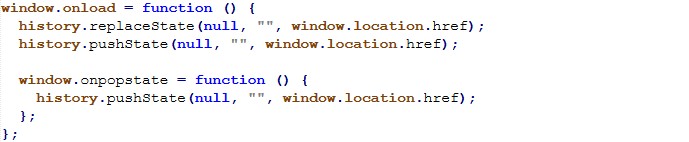
Immediately after this step, the page transitions into a UPI-based payment flow. The form disappears, and the victim is shown a QR code along with a countdown timer, creating urgency and psychological pressure.
QR Code Based UPI Payment Redirection
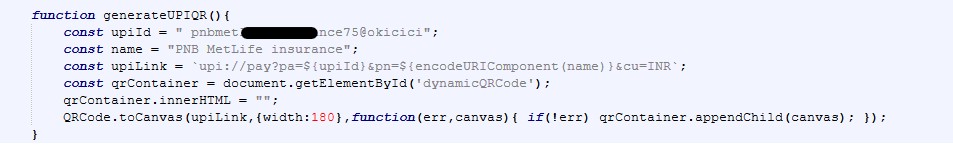
Once the victim submits the payment amount, the page dynamically switches to a QR based UPI payment flow. At this stage, no real payment gateway is involved. Instead, the JavaScript generates a UPI payment URI, renders it as a QR code, and pushes the victim toward completing the transaction inside a legitimate UPI app.
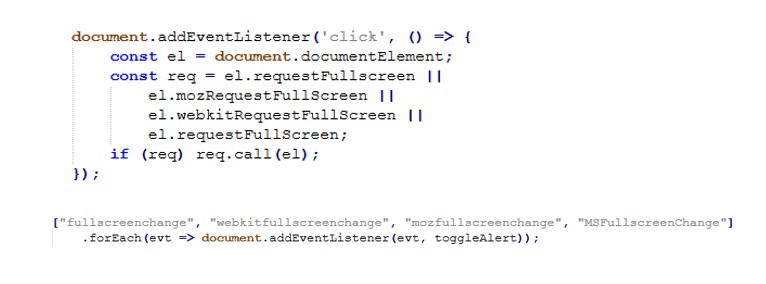
The following JavaScript snippet, extracted from the page, shows how the attacker generates the UPI QR code on the client side:
This code constructs a upi://pay URI and renders it as a QR code directly in the browser. Notably, the amount parameter is omitted or set to zero, forcing the victim to manually enter the amount in their UPI app.
Clipboard Abuse and Forced App Redirection
In addition to QR based payments, the page also includes direct buttons for PhonePe and Paytm. Clicking these buttons triggers JavaScript that silently copies the attacker controlled UPI ID to the clipboard and then redirects the victim to a payment app deep link.
The following snippet highlights this behavior:
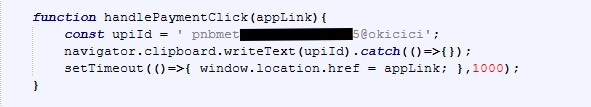
This technique ensures that even if the victim does not scan the QR code, the UPI ID is already copied and ready to be pasted inside the payment app. Redirecting users into real UPI applications significantly lowers suspicion and increases the likelihood of successful fraud.
Second Phishing Template – Premium Update and Bank/Card Harvesting
In addition to the basic payment-only template, a more advanced variant was also observed. This second template follows a slightly different flow and is significantly more dangerous, as it escalates from payment fraud to full banking and card data theft.
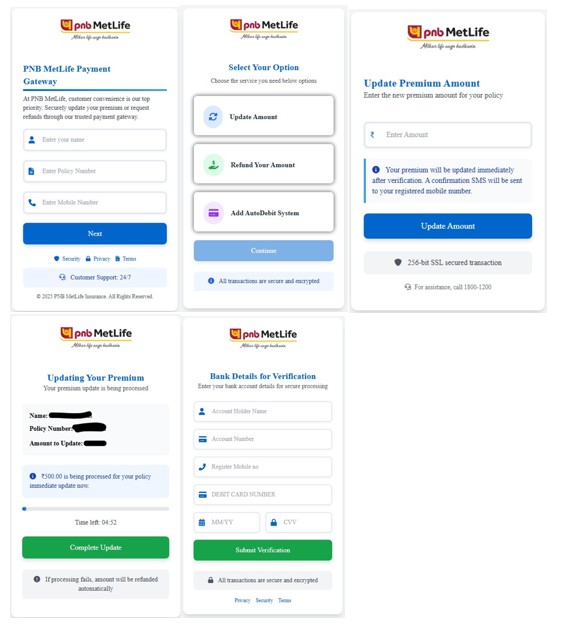
The landing page again impersonates PNB MetLife and asks for name, policy number, and mobile number. After this, the victim is presented with multiple options such as Update Amount, Refund Your Amount, and Add AutoDebit System, creating the illusion of legitimate policy servicing.
hxxps://pnb-metlife-web-india-2025-pvt-xi0ogr8l7-2fhp3fxm5e.edgeone.app/
When the victim selects “Update Amount,” they are taken to a page prompting them to enter a new premium amount. After submitting the amount, the page displays a confirmation screen showing the entered policy number and amount, along with a button labeled “Complete Update.”
Bank and Card Details Harvesting
The next stage is where the attack becomes significantly more severe. The victim is presented with a Bank Details for Verification page.
The page claims this information is required for secure verification. Once submitted, all entered banking and card details are exfiltrated to Telegram using the goldenxspy_bot, with the data delivered to the Telegram user prabhatspy.
This confirms that the second template is not just payment fraud but a full scale financial credential harvesting operation.
Abuse of Free Hosting Platforms
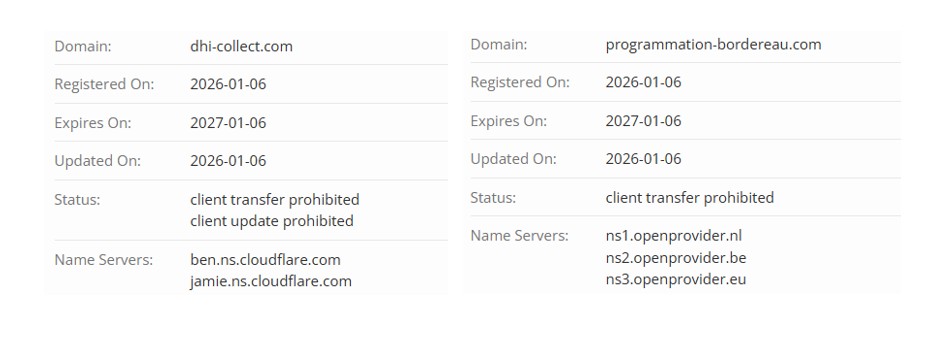
Multiple variants of these phishing templates were observed hosted on EdgeOne Pages, which provides free hosting. This allows attackers to deploy and rotate phishing pages rapidly with minimal effort.
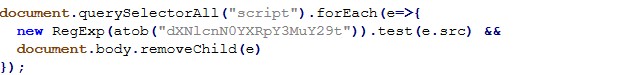
Across different deployments, the visual structure and JavaScript logic remain largely the same, while UPI IDs, mobile numbers, and Telegram bots change.
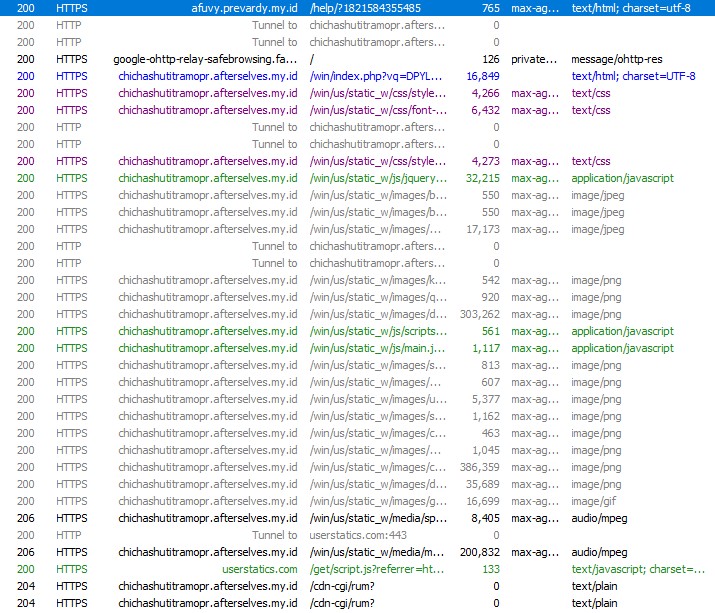
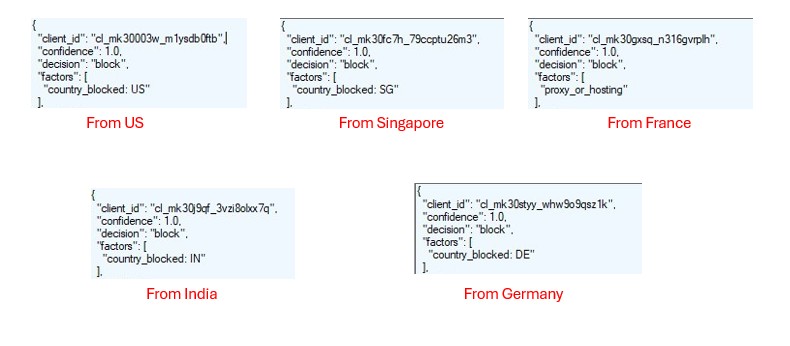
URLScan analysis shows multiple deployments of the same phishing kit, with identical client-side JavaScript logic and minor configuration changes such as UPI IDs, Telegram bots, and subdomain names.
https://urlscan.io/result/019bdbf6-dc98-7159-8a8b-45f4d97fe002/
https://urlscan.io/result/019bdabf-41f2-7613-81c0-1e99f27b3557/
https://urlscan.io/result/019bd9b5-431e-75b1-836b-ee5d50faaff0/
https://urlscan.io/result/019bd953-decb-72ae-aa3c-0693fdeac605/
https://urlscan.io/result/019bd950-f84f-718c-8b5e-b04f152e8898/
https://urlscan.io/result/019bd94d-3881-75ac-87ef-db3a317c8ff9/
https://urlscan.io/result/019bd5bb-d242-72bf-9f2f-52d5cab3894c/
https://urlscan.io/result/019b20cf-96e3-734b-bdb8-ef9aed13d27d/
https://urlscan.io/result/019b20cd-704f-763e-b7a7-67bccda9bda7/
User Advisory
Awareness and verification remain the most effective defenses against payment based phishing and fraud.