Hi Visitor, I got this sample of malware shared on VirusBay.
Sample below:
SHA256: 630efa1e2dc642799b867363bb36d1953884480ac29942a1ab20243a8a9620ad
Signature: Microsoft Visual C# v7.0/ Basic .Net and its a Windows forms application.

Upon execution, this file drops below two files at location C:\Users\<UserProfile>\AppData\Local\Temp\
Dropped files:
C:\Users\<UserProfile>\AppData\Local\Temp\FB_2C02.tmp.exe
C:\Users\<UserProfile>\AppData\Local\Temp\cc3a68ce1dad95ce662e1c51568e3a.exe (Application Server)



Upon execution of this file, it take a screenshot of current screen and save at C:\Users\<UserProfile>\AppData\Local\Temp location.
Also it adds below file to startup programs.
- cc3a68ce1dad95ce662e1c51568e3a.exe (Application Server)
- And main malware sample file.

FB_2C02.tmp.exe:
SHA256: A02CF7E4D01C3E04C0C6F723A541289A12C5D87ECC47F6B675D84A6B1B0A23B3
File description: Gomorrah
Signature: Microsoft Visual C# v7.0/ Basic .Net and its a Windows forms application.
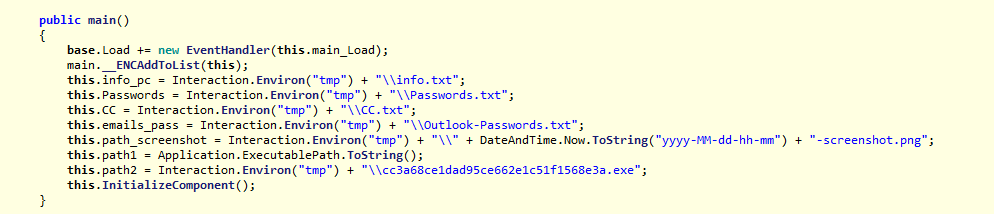
I used ILSpy decompiler to decompile FB_2C02.tmp.exe. I could see the functions written to achive below purpose.
Purpose:
- Steal browser saved user account information.

I used google chrome on which VM i was doing analysis. I could see this file has created a Passwords.txt file at C:\Users\<UserProfile>\AppData\Local\Temp\Passwords.txt


Decomplied code of executable which grab google chrome url, username and password.

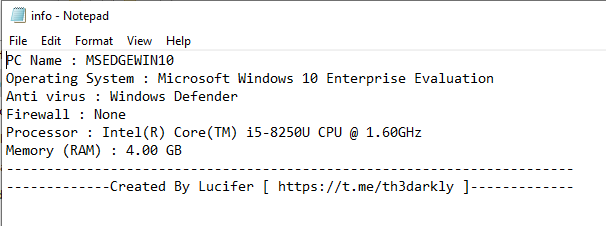
2. System Information.
This file also located at C:\Users\<UserProfile>\AppData\Local\Temp
3. Outlook Password.
This file also located at C:\Users\<UserProfile>\AppData\Local\Temp. As I wasnt using outlook, the file was empty.

4. Credit Card information
This file CC.txt which stores information about CC also located at C:\Users\<UserProfile>\AppData\Local\Temp.
It was empty too.
Below code grab CC information from the browser.

Just not from Google chrome but from all below,
- Amigo
- Brave
- Kometa
- Orbitium
- Totch
- Yandex
It uploads all collected to the remote location. Though I am not able to see it is connecting to remote server anymore because when I ran this, got run time exceptions.
But it gets connected to below URL as its mentioned on VirusTotal detection.

Summary:
Malware upload below information to remote server.
- Web account passwords from web browsers.
- Credit card information from web browser.
- Outlook passwords.
- Client machine information.
Thank you.

[…] Article Link: https://malwr-analysis.com/2020/03/28/password-stealer-trojan-malware-analysis/ […]
LikeLike
Nice write-up! In the info.txt file that this malware drops, it says: ‘Created By Lucifer [ https://t.me/th3darkly ]’
Looks like it might be this: https://sinister.ly/Thread-Lucifer-v-1-2-HTTP-Botnet-New-Version-2019-Stealer-Grabber
LikeLiked by 1 person
Yes it seems like this. Thanks for your comment Andrew 🙂
LikeLike