Hash: d26a7e67cda125f11270af0a820f6644cf920ed70fd5b166e82757dabb6d1ee0
Download sample link: Here
File type: PDF
VirusTotal score: 27/54

PDF Document Preview
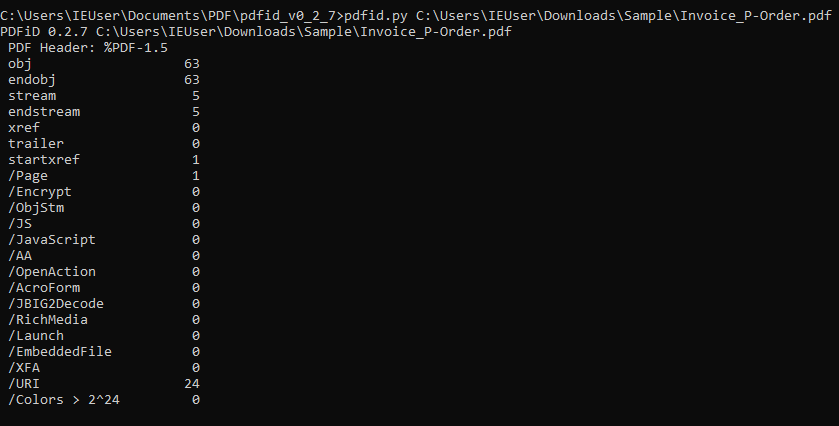
I have used PDFiD tool to analyse the header of pdf file. Observed file contains 24 URL’s.
Next step is to extract URL’s from the document. I will use two tools here to perform this, pdf-parser and PDFStreamDumper.
I am using pdf-parser tool to extract only the list of URL’s from this document. for that I am navigating to the pdf-parser folder and executing command. pdf-parser is python script.
pdf-parser.py -k /URI <.pdf file>

There are these 5 URLs extracted from the pdf document.
(http://www.diamondcreationslb . com/doc/rdd.htm)
(http://ruseuropharm . ru/tobi/index.php)
(http://tcil-bd . com/tin-count/zigi/index.php)
(http://tcil-bd . com/wp-includes/IXR/alen/index.php)
(http://tcil-bd . com/dfp/index.php)
PDFStreamDumper is very handy tool with GUI. This loads all objects in PDF file and show in Text, Hex format. Opening malicious pdf file in PDFStreamDumper, I can see URL’s under objects. To get all the URL’s I will have to go through all objects from the left panel one by one.
E.g.

URL Verification
http://www.diamondcreationslb . com/doc/rdd.htm
Report : Phishing

http://ruseuropharm . ru/tobi/index.php
Report: Phishing
Status: 404

http://tcil-bd . com/tin-count/zigi/index.php
Report: Phishing
Status: 404

http://tcil-bd . com/wp-includes/IXR/alen/index.php
Report: Phishing
Status: 404

http://tcil-bd . com/dfp/index.php
Report: Phishing
Status: 404

Summary:
- PDF File has URL’s embedded.
- All URLs are phishing.
