Overview
This blog documents a large-scale parasite SEO (search engine poisoning) campaign identified across dozens of domains hosted on Cloudflare Pages.
The campaign relies on a reused malicious HTML template that impersonates Amazon style product pages, injects gambling related SEO spam, and abuses canonical, Open Graph, and structured data fields to hijack the reputation of unrelated legitimate websites.
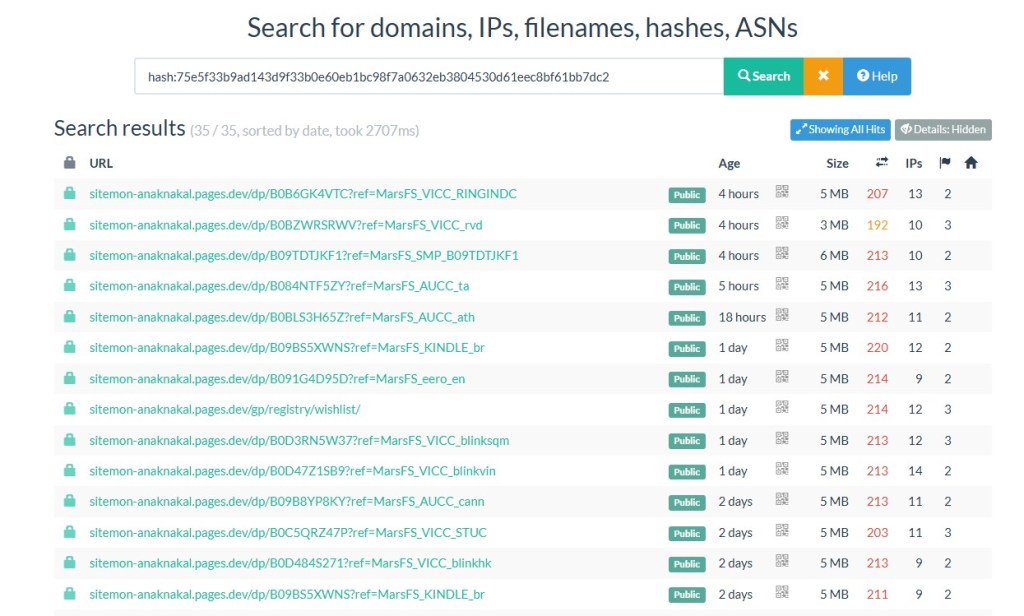
Analysis using urlscan hash searches confirms that the same page template is deployed at scale, with only the embedded “legitimate” URL changing between deployments. This behavior indicates an automated SEO spam operation, not isolated compromise.
Notably, the template also embeds a legitimate Amazon sign-in URL, further reinforcing the illusion of authenticity and increasing the phishing risk surface.
No direct credential harvesting or malware delivery was observed. Nevertheless, the activity is malicious by intent, designed to manipulate search rankings and mislead both users and search engines.
Campaign Overview
The campaign combines multiple well-known SEO abuse techniques:
- Fake Amazon product page URL structures
- Free static hosting infrastructure (primarily Cloudflare Pages)
- Gambling keyword injection (e.g., slot gacor, JUDOLBET88)
- Canonical and Open Graph metadata pointing to unrelated trusted websites
- Hidden backlink farms to inflate SEO signals
- Embedded legitimate links to trusted services (Amazon sign-in)
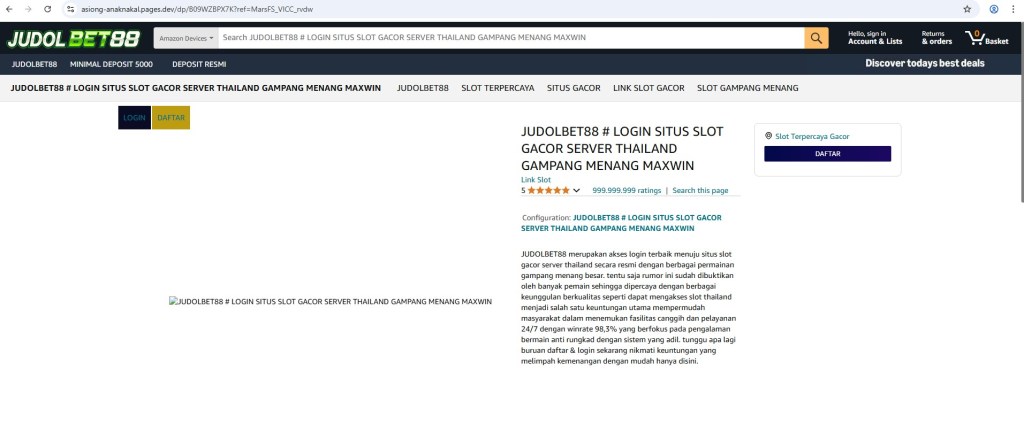
Amazon Product Page Impersonation
A representative example observed in this campaign:
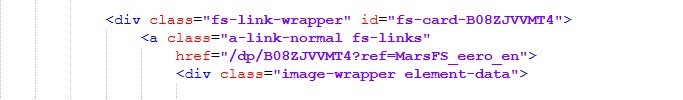
/dp/B08ZJVVMT4?ref=MarsFS_eero_en
Key indicators:
- /dp/<ASIN> is specific to Amazon product URLs
- ref= parameters mimic Amazon referral tracking
- No legitimate product details, pricing, or checkout functionality exists
These URLs are crafted solely to exploit search engine familiarity and trust, not to serve users.
Embedded Amazon Sign-In Link (Risk Amplifier)
One critical finding in the analyzed html(landing page) template is the presence of a real Amazon sign-in URL:
hxxps://www.amazon.com.au/ap/signin?openid.return_to\u003dhttps%3A%2F%2Fwww.amazon.com.au%2FAmazon-dual-band-Wi-Fi-router-Charcoal%2Fproduct-reviews%2FB0DG4WZZPV%3Fie%3DUTF8\u0026openid.identity\u003dhttp%3A%2F%2Fspecs.openid.net%2Fauth%2F2.0%2Fidentifier_select\u0026openid.assoc_handle\u003dauflex\u0026openid.mode\u003dcheckid_setup\u0026marketPlaceId\u003dA39IBJ37TRP1C6\u0026language\u003den\u0026openid.claimed_id\u003dhttp%3A%2F%2Fspecs.openid.net%2Fauth%2F2.0%2Fidentifier_select\u0026openid.ns\u003dhttp%3A%2F%2Fspecs.openid.net%2Fauth%2F2.0
Although the link itself points to a legitimate Amazon domain, its inclusion serves several malicious purposes:
- Trust reinforcement – Users who notice an Amazon login link may assume the page itself is legitimate.
- Phishing pre-conditioning – The page trains users to expect Amazon authentication, lowering suspicion if future variants introduce credential-harvesting overlays or fake login forms.
- Search engine deception – Legitimate outbound links to trusted brands can reduce automated suspicion and increase perceived legitimacy.
Infrastructure Abuse: Cloudflare Pages
A significant portion of the identified pages are hosted on pages.dev, indicating widespread abuse of Cloudflare Pages.
Why attackers favor this platform:
Attackers increasingly favor this platform because it offers free and frictionless deployment, allowing malicious infrastructure to be spun up with minimal effort or cost. The ability to rapidly propagate and clone sites enables large-scale campaigns using identical templates across numerous URLs. Built-in HTTPS support lends a false sense of legitimacy to victims while reducing setup overhead for attackers. Finally, takedown at scale is challenging without direct provider intervention, making the infrastructure resilient and attractive for sustained phishing and social-engineering operations.
The presence of identical HTML hashes across multiple pages.dev sites strongly suggests automated mass deployment.
Reputation Hijacking via Metadata Manipulation
One of the most critical behaviors in this campaign is the deliberate misuse of trusted third-party websites via metadata fields:
- canonical
- og:url
- Structured data (Organization url)
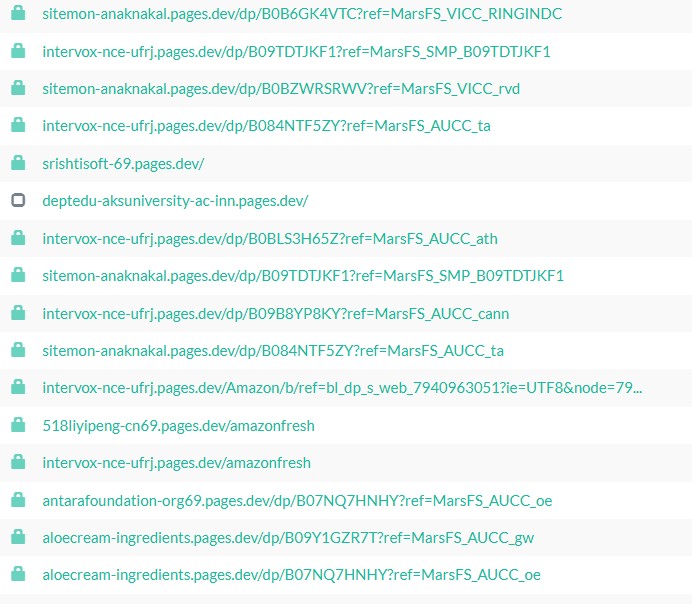
In each deployment, these fields are set to different legitimate, unrelated websites, including:
- Government portals
- Educational institutions
- Corporate websites
- NGOs and public services
Why this technique is effective
Search engines treat canonical and structured data fields as strong trust signals. By embedding legitimate URLs, attackers attempt to:
- Launder authority into spam pages
- Artificially boost ranking
- Associate gambling content with reputable entities
- Pollute search results tied to trusted sites
The rotation of abused legitimate URLs across deployments confirms this is intentional and systematic, not accidental misconfiguration.
Template Reuse at Scale (urlscan Evidence)
Using urlscan hash-based searching, numerous sites were identified that share the same HTML fingerprint, indicating widespread reuse of a single template. These pages exhibit an identical DOM structure, contain the same hidden link blocks, and reuse identical SEO spam content across deployments. The only meaningful difference between each instance is the abused “legitimate” URL embedded into the template, highlighting automated cloning and large-scale propagation of the campaign.
This strongly confirms the presence of centralized template generation, with a single source producing identical page structures across multiple deployments. The consistent reuse further indicates automated deployment mechanisms, enabling rapid and large-scale rollout of these pages. Together, these patterns point to clear campaign level coordination, rather than isolated or opportunistic activity.
Such behavior is typical of industrial SEO poisoning operations.
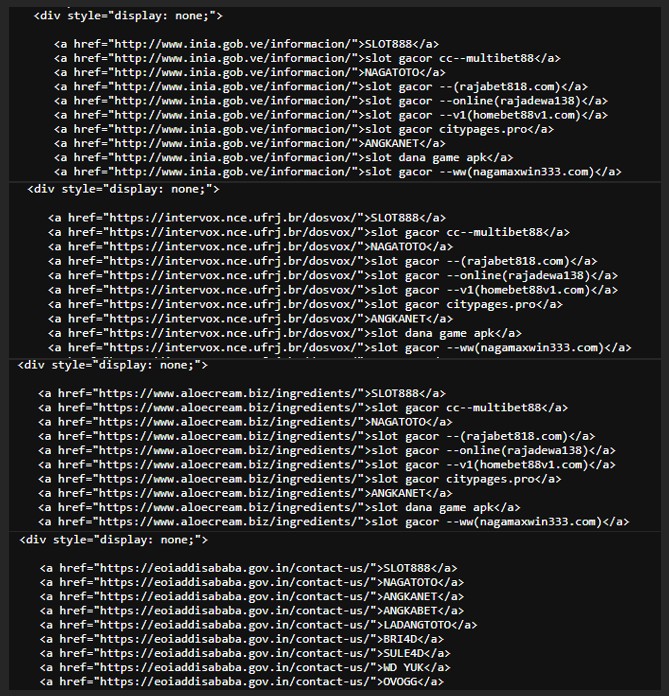
Hidden Link Farm Injection
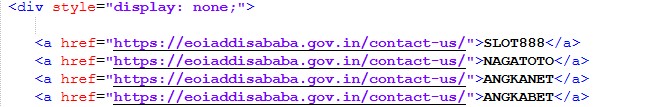
Each page contains a hidden HTML section (display:none) populated with:
- Dozens of gambling-related anchor texts
- Links pointing to the selected legitimate website for that deployment
Hidden link farms are a strong indicator of malicious SEO activity, designed to manipulate backlink metrics without user visibility.
Hidden Gambling Keyword
SLOT888, NAGATOTO, ANGKANET, ANGKABET, LADANGTOTO, BRI4D, SULE4D, WD YUK, OVOGG, GASING77, BROMO777, AGEN88, HQTOTO805, INFINI88, LAWU88, KENZO88, RAPI88, BETON88, KUDA4D, RAJA4D, LOTUS88, GIGA88, SULE88, TAMBANG88, MINION88, DEWA99, DEWA333, DEWATOTO, RAJA PAITO, RAJAJUDI, RAJAJP, RAJADEWA55, PADUKARAJA, WEBINI33, HYPE168, BOLA88, DEVIL666, 91DEWA, RAJA111, ROG777, TOTO77, TOP1TOTO, IBC4D, KIPASWIN, VANTASLOT, MANGJP, SAVEFROM IG, YANDEX EU, DAUN77, RAJAKOI, BIMABET, IDCASH, REDMITOTO, MEGA228, MEGAWIN228, INDOLOTTERY88, AMERIKATOTO, AMERIKA TOTO, BOLA GACOR, DADU ONLINE, DEWA666, WDBOS, SURYA123, RAYA123, JARWO123, MANCINGDUIT, MANCING DUIT, PANGKALANTOTO, NAGASAON, KAOS TOGEL, WOLES TOGEL, VESPA TOGEL, PINTU TOGEL, NADIMTOGEL, OMUTOGEL, DAYAK77, ALEXISTOGEL77, SASARANJITU, EUROTOGEL, JEBOLTOGEL, GENGTOTO, FENDI188, BIGWIN, MEGAWIN, MAHAZEUS, HARTA500, RTP JOSTOTO, ARYA88, NANASTOTO, DEPOBOS, JEJUSLOT, TARIKWDKU88, IDN SLOT, IDN POKER, SLOT88, SLOT88 RESMI, SLOT ONLINE, SLOT GACOR, SLOT THAILAND, SITUS TOGEL, TOTO TOGEL, TOTO SLOT, TOTO 4D, TOGEL ONLINE, TOGEL 4D, LUNA TOGEL, SITUS RAFFI AHMAD, SITUS TOTO 4D, SITUS TOGEL 4D, SITUS TOTO TOGEL, SITUS TOGEL TERBESAR, SITUS TOGEL RESMI, SITUS TOGEL TERPERCAYA, SLOT DEPO 10k, SLOT DEPO 10000, DEPO 10 BONUS 10, DEPO 20 BONUS 20, PADI777, SGP777, MPO100, MPO222, MPO007, MPOCASH, MPONUSA, MPO888, MPO77, MPOGACOR, LOS303, POS4D, OLLO4D, GAJAH77, DOLAR168, STARBET77, PANDAWA138, ZET77, KINGBET88, PERI909, ALADIN88, LIGA303, SITOOLS88, MPOJUTA, HAKIM77, SPBO, JET777, MINO4D, KOKO333, BATMAN123, MAXPRO88, MAMI188 LOGIN, TANAH4D, BAGONG88, IMPIAN888, SLOTONLINE, TEKTOK4D, MPO69, SLOTRESMI, PARTNER4D, MANJA88, PASUKAN99, TOOLS367, DAYANG4D, DEWABET138, HORMAT88, BUMI33, ROYALBET, ROYAL51, PAIRBET, WALET789, SULTAN99, MENARA88, SUBUR89, JOKER555, ZONA138, SARANATOGEL, SLOTGOPAY, 888WIN, SLOTQQ, SUPERSPIN555, QQZEUS, SOLO4D, 4DTOGEL, 88ASIA, SUPERWD, OLO4D, 4DASIA, QQ88, PINTU4D, QQ888, BETTOGEL, CAPIT4D, BOLASIAR, BADAI4D, ASIA118, MBO777, BIG365, ASOKA88, JURAGAN69, SUHU189, SUHU69, SUHUTOTO, KLIKSLOT, OLX888, PREMANSLOT, SAKTI123, RATUMACAU, KANTORBOLA, MT777, JP777, MPO99, ASIA4D, DEWA4D, STAR777, MPO4D, 75WBET, 56KBET, 55KBET, 55BET, 33BET, 777LIVE, 777BET, PC777, INA777, GM777, DEWAGACOR, HOKI88, HOKI188, PAY4D, ASIABET88, SKY777, JP88, 188BET, GACOR4D, SLOT303, SLOT77, DEWI78, UNYIL4D, JOSTOTO, ASIASLOT, SLOT99, BOS4D, AGEN188, AHA4D, STARSLOT, CUANSLOT, SITUS4D, PASARBARIS, WIN888, WIN777, BET77, BET88, IDNSLOT, 999BET, TOPSLOT, JUARASLOT, AGEN168, SLOT121, RAJA777, 77SLOT, PGSOFT, 88SLOT, ADA777, NEKO77, DRAGON77, INDOWIN, HOKI303, GACOR303, BET188, SLOTCUAN, AGENSLOT, RTPSLOT, VIRAL4D, JP4D, 100TOGEL, GBO138, DOSENTOTO, PARITOTO, JUDOLBET, GACOR888, HAHA303, KOKO288, AIRBET, ASIA303, TOKOWIN99, VIOBET, PRAGMATIC77, VIRAL99, GENG88, GOKIL303, GRAND77, SENIOR4D, XXTOTO, MILD88, DEWAASIA, BOSS88, INDOMASTER88, WADAH4D, CUAN368, BOLAPELANGI, FAIRTOTO, BINTANGMPO, AKARSLOT, SBOTOP, PITASLOT, KAISAR88, JAZZ188, ASIAPLAY, KAPTEN33, CRAZYRICH88, MESSIPOKER, SALDO4D, SURAT4D, REDWIN69, HOMEBET88, PG TOTO, DANA TOTO, MPO SLOT, NEXUS SLOT, SLOT TOGEL, SLOT MAXWIN, SLOT 777, gacor303, slot303, SLOT DEPO 10K, SLOT HOKI, HOKI SLOT, SLOT GACOR 5000, TOGEL HK, JUDOLBET88, SLOT BRI, SLOT BCA, PRAGMATIC PLAY, JAYASLOT, LINK GACOR, HONDA4D, SARANGSBOBET, ALEXIS4D, LEVIS4D, PULAU88, GGPLAY88, INI SLOT 88, PLAYKING88, JAM GACOR DAN POLA OLYMPUS, JAM GACOR MAXWIN, JAM GACOR SLOT MAHJONG WAYS 1, JAM GACOR SUGAR MAXWIN, JAM JACKPOT SLOT, OLX123, IWANTOTO, SLOT88JP, GACOR88, RATUBET, RAJABET, JUDI4D, BANDARTOTO, SLOTASIAN, DANAGACOR, TOTO888, TOTO303, TOTO777, JUARABET, ASUAGACOR, 4DTOTO, DANA888, PGSLOT, JUDI2D, AGEN2D, EMAS4D, RACUNSLOT, MASTER77, GACOR168, SLOTASIA88, JUDITOTO, FAFABET, GACOR999, BET89, SLOT22
The presence of hundreds of gambling keywords hidden from users but visible to crawlers is one of the strongest static indicators of malicious SEO activity, even in the absence of malware or credential harvesting code.
Indicators of Compromise (IOCs)
Domains
- *.pages.dev
Behavioral Patterns
- /dp/B0
- pages.dev/dp/
- Canonical: unrelated trusted domain
- Embedded legitimate sign-in URL
This campaign represents a coordinated parasite SEO operation that combines brand impersonation, reputation hijacking, and infrastructure abuse.
While no direct credential theft was observed, the inclusion of a legitimate Amazon sign-in link significantly increases the phishing risk potential, indicating a design that is deceptive by intent and easily extensible into active scams.