Introduction
“Cloud Storage Full” phishing emails have been circulating for years, exploiting a simple but effective fear, the risk of losing personal data. While the lure itself hasn’t changed much, the way these scams make money has evolved significantly.
Earlier versions of this scam typically pushed users toward fake login pages or outright fraudulent payment forms. What’s increasingly being observed now is a more subtle and harder to detect approach manipulating users into paying for legitimate products through deceptive redirection and affiliate abuse.
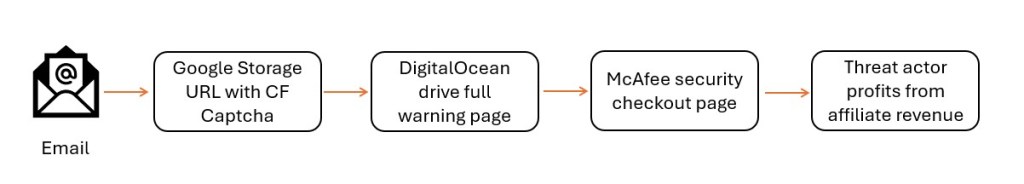
This blog walks through a recent phishing email that abuses trusted infrastructure end to end, starting from a scareware email, moving through Google Cloud hosted landing pages and fake Cloudflare verification, and ultimately landing on a legitimate McAfee checkout page. It also ties this activity to a previously observed TotalDrive “storage full” scam, showing this is not an isolated incident but part of a broader trend.
The Phishing Email
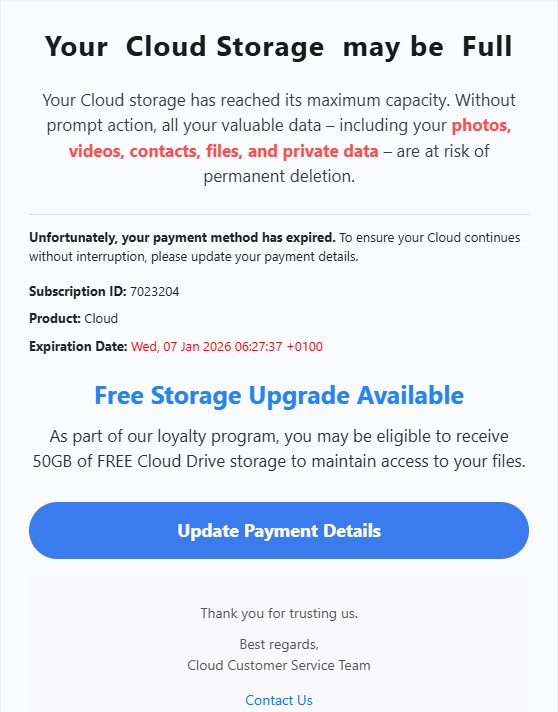
The email claims that the recipient’s cloud account has been blocked and warns that photos and videos will be removed unless immediate action is taken. The wording is deliberately alarming and designed to create panic rather than clarity.
There is no mention of a real cloud provider, no account identifiers, and no prior context. Instead, the message relies entirely on urgency payment failure, account suspension, and imminent data loss to push the recipient toward clicking the embedded link.
Email Header Observations
The email was delivered via Mailgun, a widely used email service provider that is often abused for large scale phishing and affiliate scams.
Redirect Chain Analysis
Google Cloud Storage as the First Landing Page
Clicking the link in the email redirects the user to a page hosted on Google Cloud Storage.
Using a trusted Google domain helps attackers bypass URL reputation checks and lowers user suspicion.
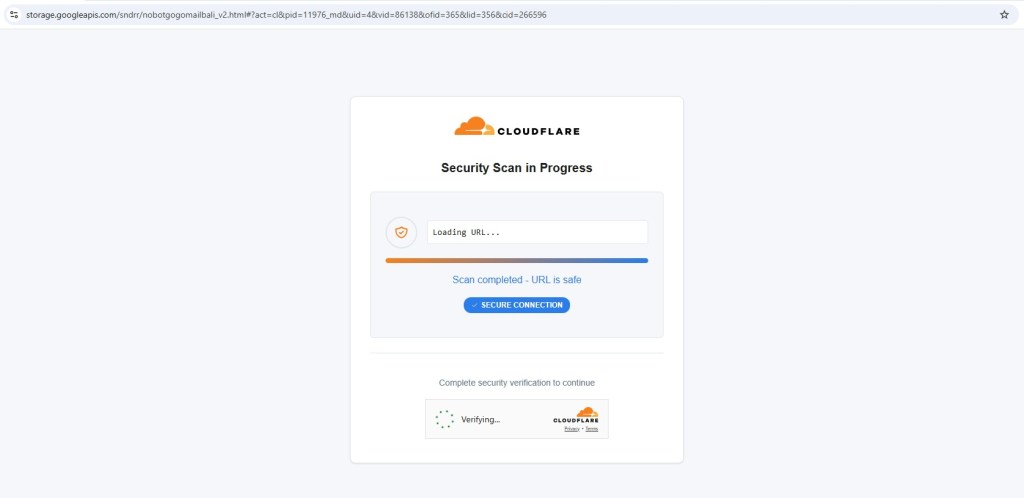
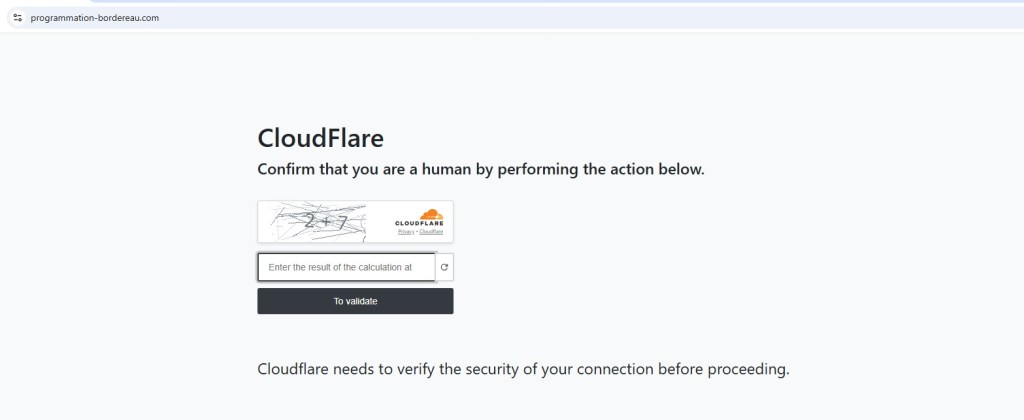
Fake Cloudflare CAPTCHA Gate
Before reaching the final destination, the user is presented with a Cloudflare CAPTCHA and security check. The page displays fake scan progress and reassuring messages indicating the URL is safe.
This step serves multiple purposes. It filters automated scanners, delays analysis, and reinforces the illusion of legitimacy. This behavior closely matches what is commonly seen in Traffic Distribution Systems (TDS) used by modern phishing operations.
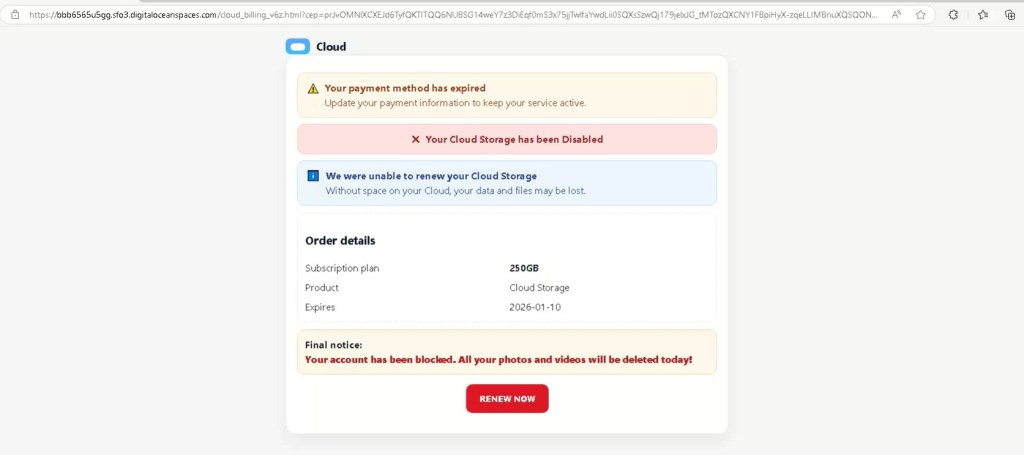
Intermediate Landing Page: Fake “Cloud Billing” Portal (DigitalOcean Spaces)
After clicking the link in the email, the redirection chain leads to an intermediate page hosted on DigitalOcean Spaces:
hxxps://bbb6565u5gg.sfo3.digitaloceanspaces.com/cloud_billing_v6z.html
This page presents itself as a cloud billing or subscription status portal, using generic “Cloud” branding rather than naming any real provider.
The page includes fabricated subscription details such as a storage plan size and an expiration date, creating the illusion of a real account state. None of this information is personalized or verifiable it exists purely to reinforce the scareware narrative introduced in the email.
From a technical perspective, hosting this page on DigitalOcean Spaces provides the same advantages seen elsewhere in this campaign, trusted infrastructure, HTTPS by default, and low friction for rapid deployment and rotation.
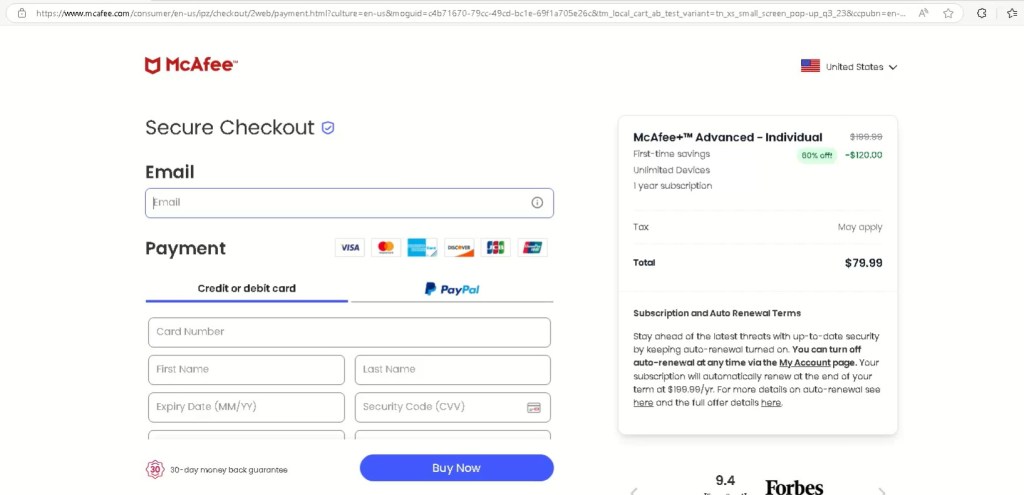
Transition to Monetization: Redirect to McAfee via Affiliate Link
Clicking “Renew Now”does not collect credentials or payment details on this page. Instead, it immediately redirects the user to a legitimate McAfee checkout page offering McAfee+ Advanced – Individual.
At first glance, everything appears legitimate, HTTPS, real branding, and a genuine payment flow. However, a closer look at the URL reveals multiple affiliate tracking parameters, including values such as affid, cjevent, and PID.
These parameters confirm that the redirect is intentional and monetized. Each completed purchase likely generates affiliate commission for the attacker. No card skimming occurs the victim enters payment details directly on McAfee’s site but the purchase itself was induced through deception.
A Familiar Pattern: The TotalDrive “Storage Full” Scam
This technique isn’t new.
A similar “storage full” phishing flow was previously documented by me on X, where victims were redirected to secure[.]totaldrive[.]com after interacting with fake iCloud warnings.
What These Campaigns Have in Common
Across both the McAfee and TotalDrive scams, the same elements appear repeatedly. Users are confronted with fake cloud warnings, routed through trusted platforms, reassured by fake security checks, and ultimately pushed toward legitimate checkout pages. At no point are credentials stolen instead, users are manipulated into making payments they never intended to make.
Attack Flow
This campaign abuses legitimate services at every stage, email delivery platforms, cloud hosting, security branding, and affiliate marketing systems. The abuse lies not in any single component, but in how they are chained together to mislead the user.
Email Infrastructure
Sending IP – 193.24.209.200
Email Service Provider – Mailgun (legitimate ESP abused for phishing)
Observed Header Indicators
- X-Mailgun-Tag: post
- X-Mailgun-Track-Clicks: false
Sender Domain Pattern – *.xenravo.biz.ua
Phishing And Staging URLs
Google Cloud Storage
hxxps://storage.googleapis.com/sndrr/nobotgogomailbali_v2.html
DigitalOcean Spaces – Fake Cloud Billing Page
hxxps://bbb6565u5gg.sfo3.digitaloceanspaces.com/cloud_billing_v6z.html
Redirect And Tracking Indicators
Affiliate / Tracking Parameters Observed
affid
cjevent
PID
SID
csrc=cj
clickid
lptoken
These parameters confirm affiliate-based monetization rather than credential harvesting.
Final Monetization Endpoint
McAfee Checkout
hxxps://www.mcafee/.com/en-us/ipz/feyncart/2web/payment.html?culture=en-us&moguid=c4b71670-79cc-49cd-bc1e-69f1a705e26c&tm_local_cart_ab_test_variant=tn_xs_small_screen_pop-up_q3_23&ccpubn=en-us:direct:aff:mai&SID=882390700&cjevent=113666eaebd511f0836900670a82b820&affid=1494&csrc=cj&csrcl2=The+Affiliati+Network%2C+LLC&ccoe=direct&ccoel2=am&ccstype=partnerlinks_113666eaebd511f0836900670a82b820&CID=242012&PID=101616859