I have been recently receiving phishing emails impersonating as Indian Cyber Crime Coordination Centre (I4C). Upon investigating, multiple users had reported these scams on twitter/X and reddit.
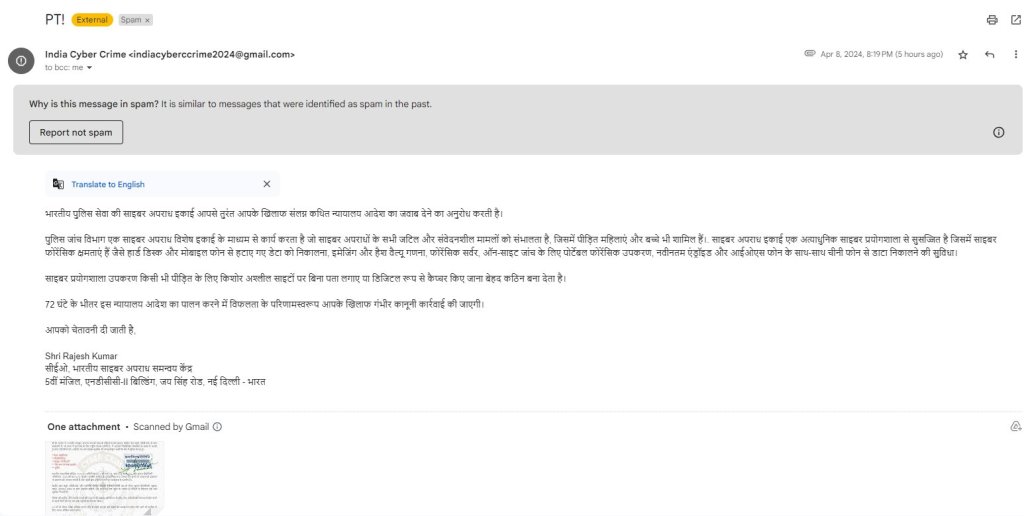
1st phishing email received on April 8, 2024:
Its also been tweeted by @Cyberdost which is an X account for Cyber-safety and Cybersecurity awareness handle maintained by Ministry of Home Affairs, Government of India
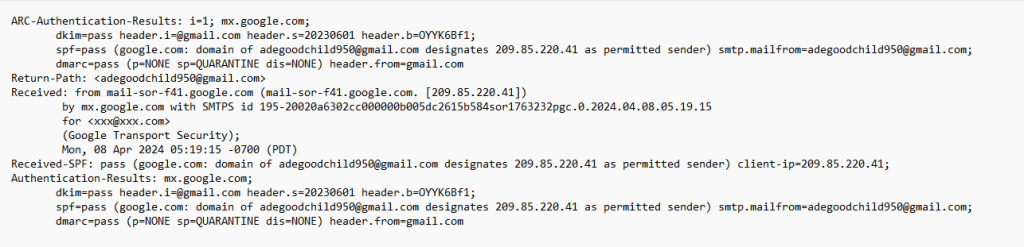
I tried to dig in and checked email header. This email has been received from id: adegoodchild950@gmail.com
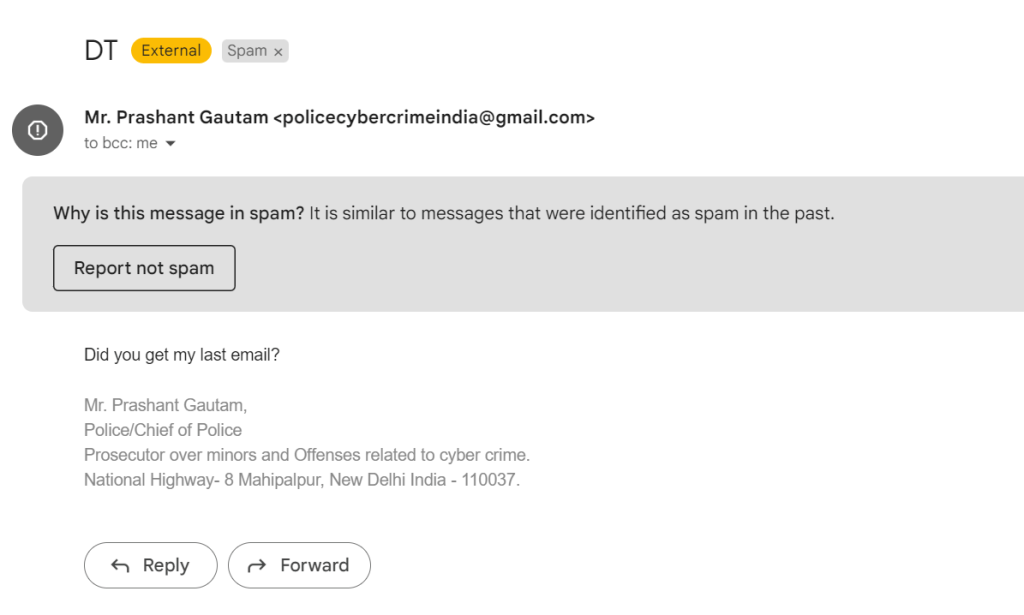
2nd phishing email received on: May 18, 2024
Received another email impersonating as “Mr. Prashant Gautam policecybercrimeindia@gmail.com“
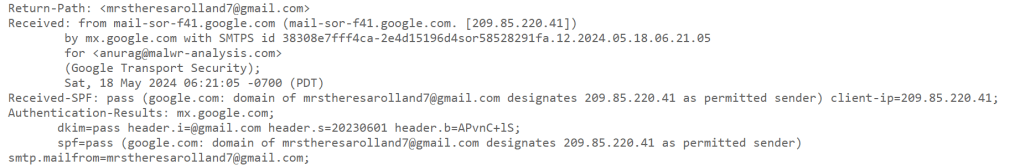
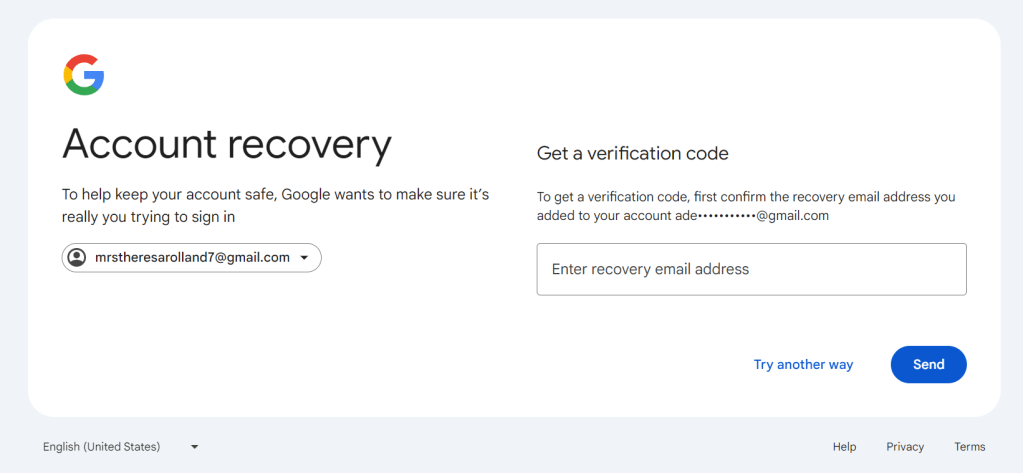
Certainly this is phishing email and I checked email header of this email and this was sent by mrstheresarolland7@gmail.com
To check whether both emails have been sent by same person or group:
I put login email as mrstheresarolland7@gmail.com on Gmail and clicked on forgot password. It gave me Account recovery option sending verification code on alternative email id.
The recovery email id is matching to earlier email sender ids first three letters adegoodchild950@gmail.com. Though this could be a coincidence.