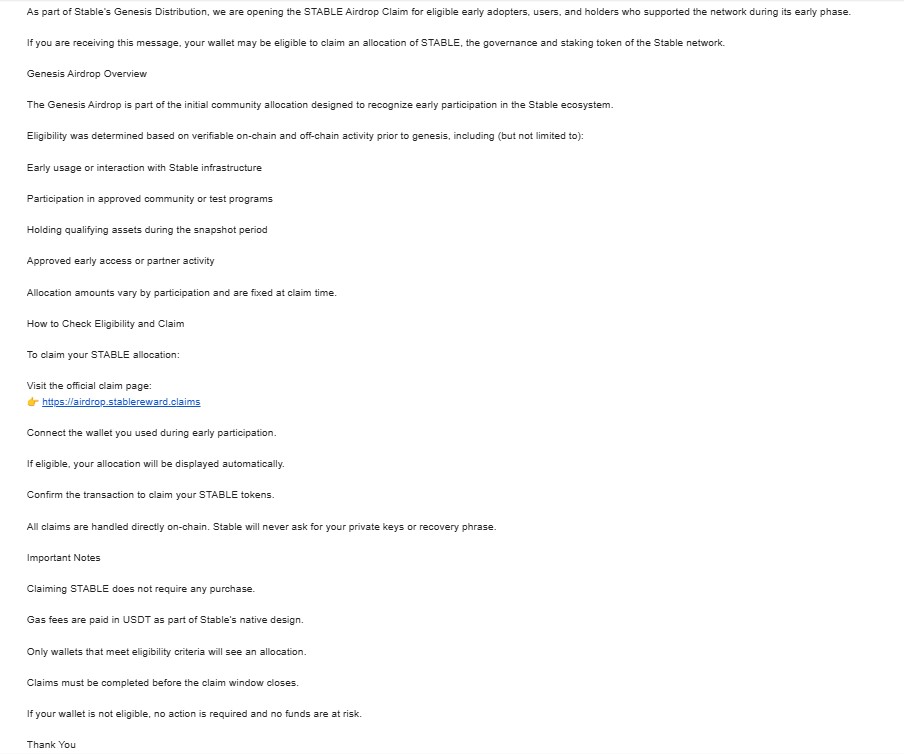
In this analysis, I investigated a suspicious email titled “Stable Genesis Airdrop: Claim for Eligible Wallets Now Open”, which redirected victims to the domain:
hxxps://airdrop.stablereward[.]claims
Through sandbox execution, traffic inspection, and UI analysis, the campaign was confirmed to be a high confidence cryptocurrency phishing operation designed to steal wallet recovery phrases and authorize malicious blockchain transactions.
The site impersonates a fictitious project named “Stable”, abuses Cloudflare protection to evade automated detection, and deploys a fake wallet connection workflow that escalates into seed phrase harvesting.
Key Red Flags in Email Body
- Claims gas fees are paid in USDT (technically incorrect for Ethereum)
- Vague “Stable network” with no whitepaper, GitHub, or official domain
- No verifiable project presence on CoinGecko or CoinMarketCap
- Redirects to a non-standard .claims TLD
Domain and Infrastructure Analysis
Newly registered domains + crypto airdrops = classic scam pattern
WHOIS records show that the domain stablereward[.]claims was registered very recently on December 8, 2025, with an update made on December 17, 2025. The domain uses Cloudflare name servers.
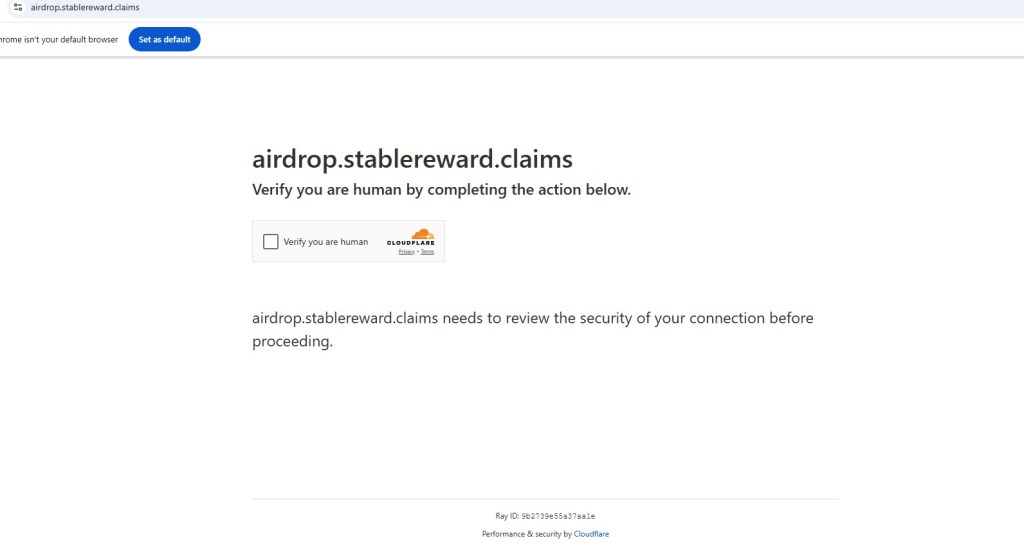
Initial Page
The presence of a Cloudflare “Verify you are human” gate indicates an intentional attempt to restrict automated access, as it effectively blocks crawlers and many security scanners from analyzing the site’s content. This technique is commonly used by malicious or suspicious sites to evade sandbox detection and fingerprinting, ensuring that payloads or scam pages are only served to real users while analysis environments are filtered out.
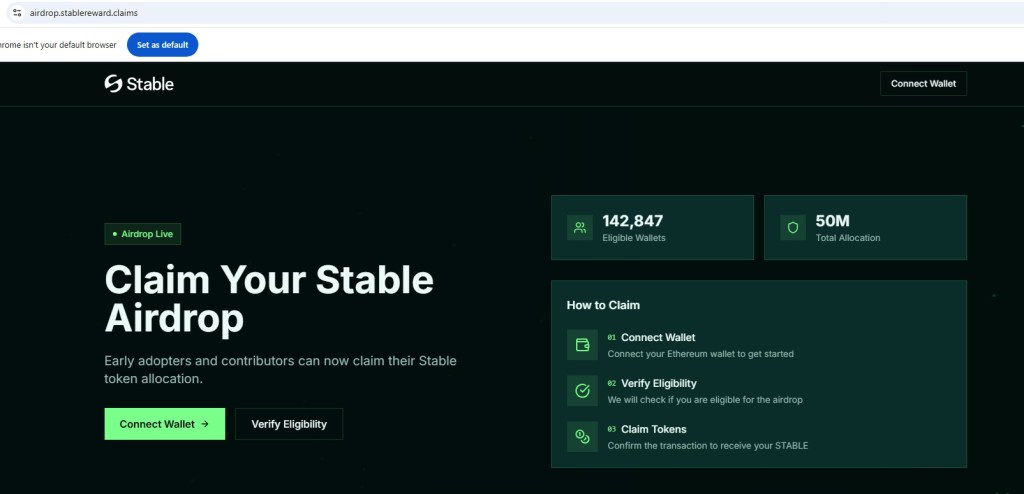
Main Landing Page
The site displays fabricated statistics such as 142,847 eligible wallets and a 50 million token allocation to create a false sense of scale and legitimacy. These exaggerated numbers are paired with a prominent “Connect Wallet” call-to-action designed to lure users into authorizing wallet access
Wallet Interaction And Credential Harvesting
It lists:
- MetaMask (recommended)
- Trust Wallet
- Coinbase Wallet
- Ledger
- Trezor
- Phantom
- OKX
- Rabby
- Uniswap Wallet
The most critical malicious behavior is observed when the site prompts users to “Import Wallet, Enter your 12-word recovery phrase” instead of invoking a legitimate wallet extension.
JavaScript Anti-Analysis Techniques
The observed JavaScript snippet is a deliberate anti-analysis technique used to disrupt inspection and automated execution. By invoking the debugger statement, the script forces execution to pause whenever browser developer tools are open, effectively halting code flow during analysis. This behavior can break automated sandboxes and dynamic analysis environments, compelling security analysts to manually bypass or modify the script before further investigation can continue.
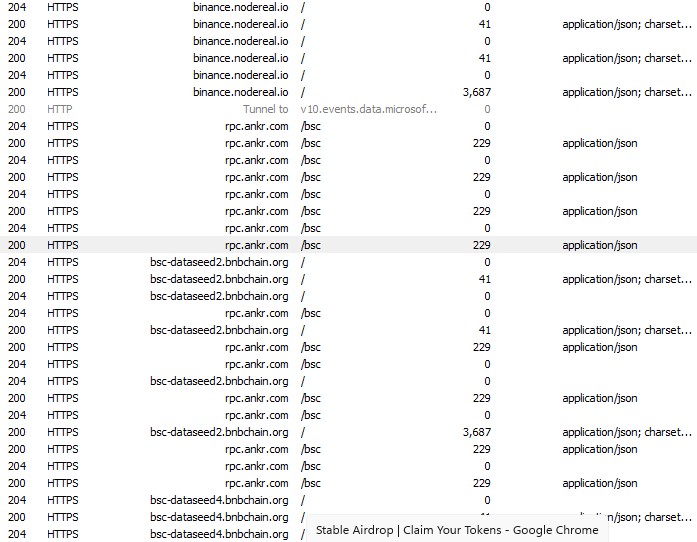
Network Traffic Analysis
The site silently connects to multiple blockchain RPCs:
- rpc.ankr[.]com/bsc
- bsc-dataseed*[.]bnbchain.org
- binance[.]nodereal[.]io
These indicators suggest that the operation is designed with multi-chain capability, targeting both Ethereum and Binance Smart Chain (BSC) users to maximize reach. Such setups typically perform wallet balance enumeration, NFT discovery, and malicious token approval requests that enable silent asset draining. The overall behavior closely matches well-known wallet drainer kits.
Attack Chain Summary
Confirmed Scam
All observed indicators clearly confirm malicious intent. The request for a wallet recovery phrase is explicitly malicious, the newly registered domain presents a high risk profile, and the so called project shows no verifiable legitimacy. On chain interaction analysis indicates RPC based draining behavior, while the presence of anti debugging JavaScript further reinforces deliberate evasion of analysis.
Indicators of Compromise – Domains
- airdrop.stablereward[.]claims
- stablereward[.]claims