Overview
I recently came across a message containing the following link:
hxxps://yandex[.]com/poll/PdZ7vgekGrNakuXZcpiB6b
At first, it didn’t look suspicious. It opened as a simple survey/poll page. But as I continued, the flow quickly shifted into a crypto reward scenario, claiming that I was eligible to receive a Bitcoin compensation payment.
And as expected with these kinds of lures, there’s a catch.
Before you can withdraw the funds, you’re asked to pay a small “commission” fee.
Full Scam Walkthrough (Video)
This gives a better idea of how smoothly the entire flow is designed to push the victim toward payment.
Infection / Lure flow
1. Initial Entry (Survey / Poll Page)
The flow starts with a Yandex poll link, which works as a kind of entry point.
This step likely serves multiple purposes. It helps make the interaction feel legitimate since it’s hosted on a known platform. It may also act as a basic filter to distinguish real users from automated systems. More importantly, it sets up the next stage of redirection.
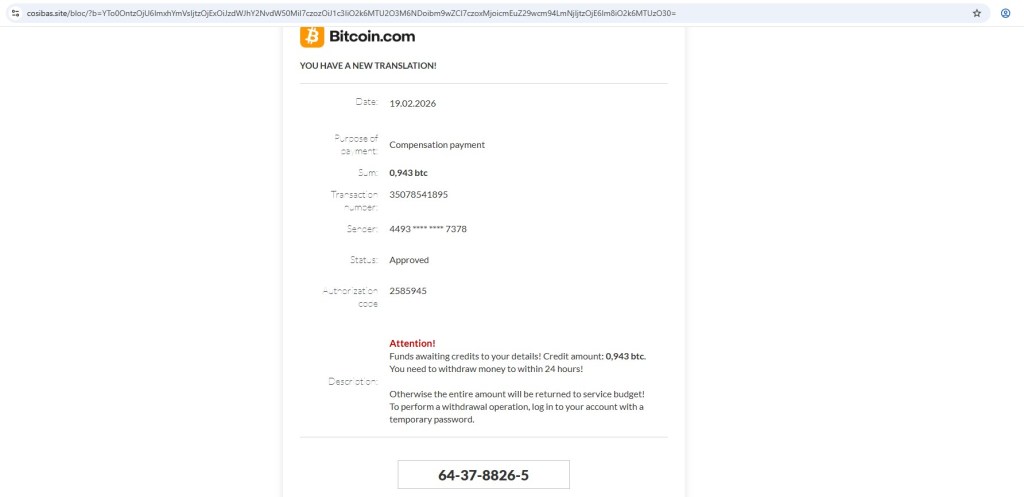
2. Fake Bitcoin Compensation Page
After interacting with the poll, I was redirected to a page that looks like it belongs to a Bitcoin related service.
The page presents a sense of urgency by claiming that a new transaction of 0.943 BTC has been created and already marked as approved. It then introduces pressure by warning the user to withdraw the funds within 24 hours, a tactic commonly used to rush victims into taking immediate action without verifying the legitimacy of the claim.
This is where the emotional hook kicks in. Seeing a large amount like 0.943 BTC immediately grabs attention.
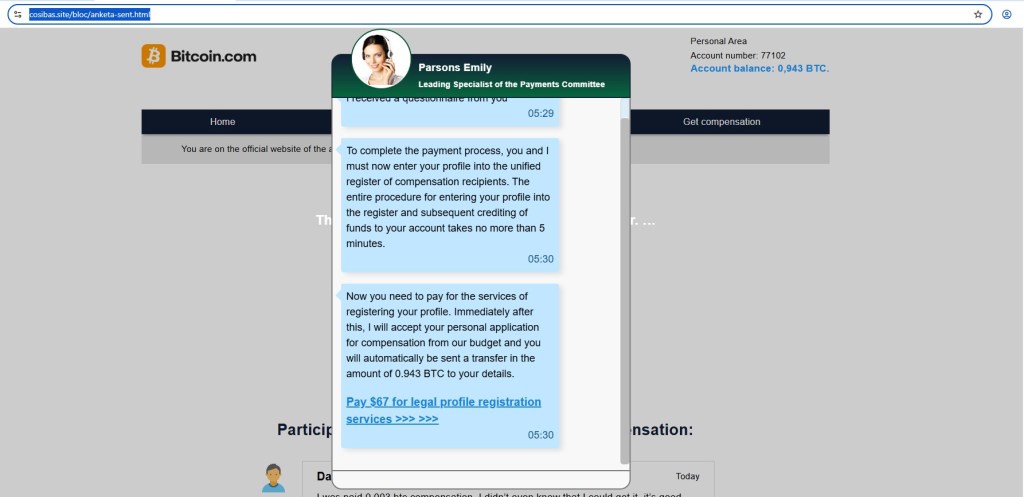
3. Social Engineering via Chat Assistant
Then a chat window appears, introducing a support agent.
The message explains that to complete the payment process, you need to register your profile in a compensation system. It sounds procedural and official, which is exactly the intention.
Shortly after, the real objective becomes clear.
You are asked to:
Pay $67 for legal profile registration services
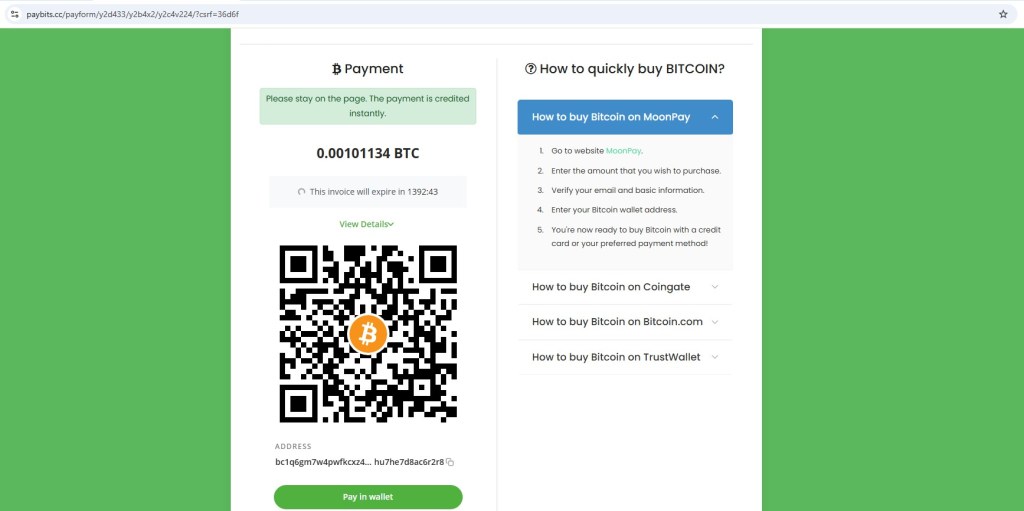
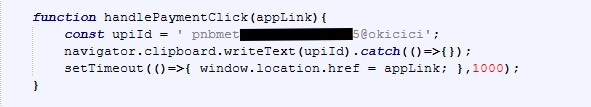
4. Payment Gateway
Clicking the payment link takes you to a dedicated payment page.
Here, everything is carefully designed to appear legitimate and trustworthy. The page shows a specific payment amount of $67, provides a Bitcoin payment option via a QR code, and displays a wallet address to reinforce authenticity. On top of that, a countdown timer indicating invoice expiry adds urgency, subtly pressuring the user to complete the transaction quickly without questioning its validity.
The design mimics real crypto payment processors, which helps reduce suspicion.
The flow is quite structured and intentional.
It starts by engaging the user through a trusted platform, which lowers initial suspicion. Then it introduces a high-value crypto reward, creating excitement. A chat assistant adds a layer of interaction, making the process feel guided and legitimate.
Finally, the user is asked to pay a relatively small fee to unlock a much larger reward.
This is essentially an advance fee scam, adapted to fit into a crypto themed narrative.
Additional Variant Observed (Octa-Themed Flow)
While analyzing further, I encountered another link that follows the same backend scam logic, but with a different initial presentation.
The flow eventually leads to the same outcome, pay a commission to withdraw BTC.
Variant Walkthrough (Video)
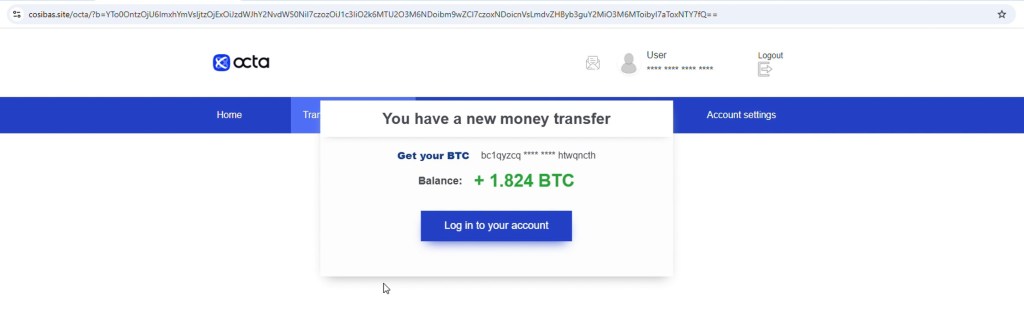
1. Fake Account / Transfer Notification
This version starts with a fake dashboard impersonating Octa.
The page further attempts to lure users by displaying a message stating “You have a new money transfer”, along with a balance of 1.824 BTC. This presentation is crafted to create excitement and curiosity, making it seem like the user has unexpectedly received funds, while subtly encouraging them to engage with the page and follow the next steps without questioning its authenticity.
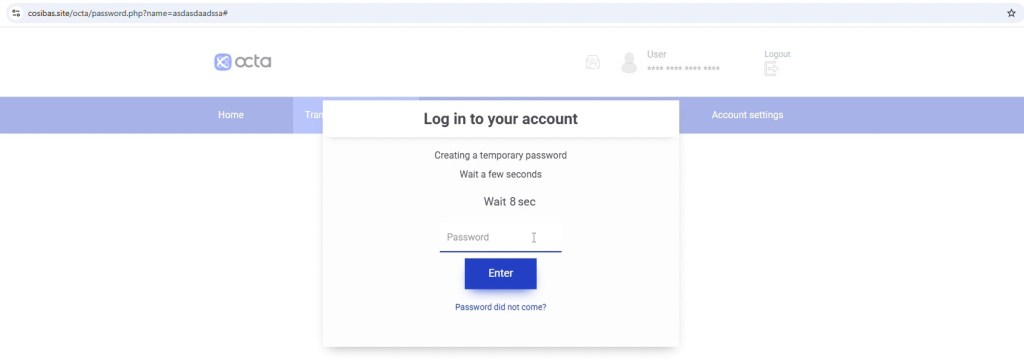
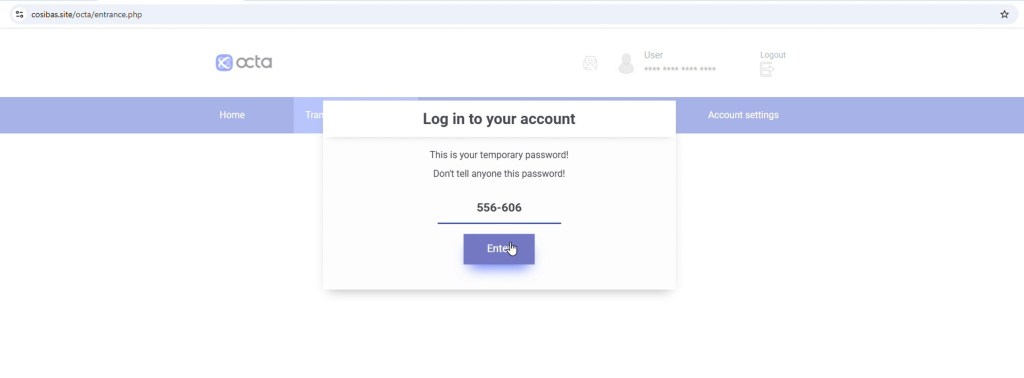
2. Fake Login & Temporary Password Flow
The user is asked to log in using a temporary password.
This step closely mimics real authentication flows to build trust and credibility. It displays a temporary password, includes an OTP style input field, and reinforces legitimacy with messaging like “Do not share this password!”. These familiar elements are designed to make the process feel secure and authentic, lowering suspicion while guiding the user further into the flow.
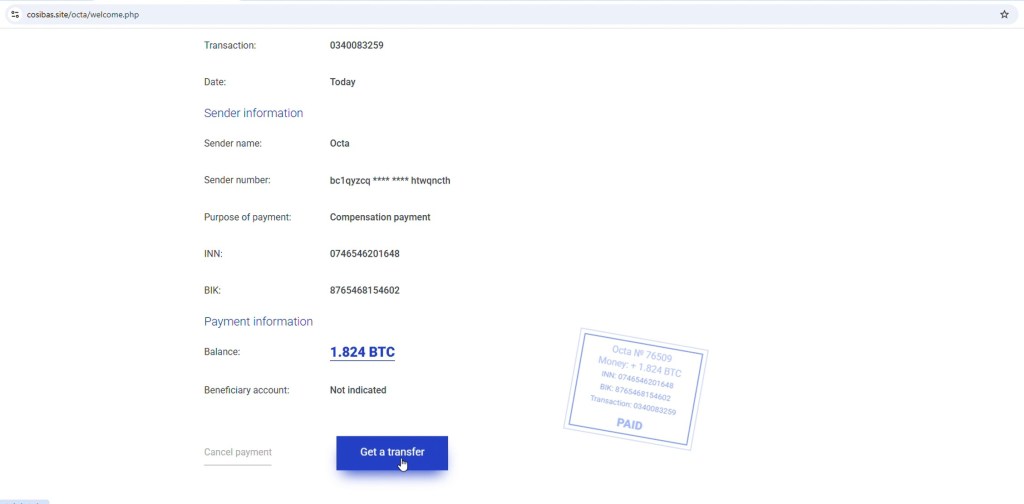
3. Transaction Dashboard
After logging in, the user is presented with a dashboard that appears highly convincing, displaying details such as the sender labeled as Octa, a balance of 1.824 BTC, and a status marked as paid. The layout, wording, and transaction details are all carefully crafted to create a sense of authenticity, making the entire interface look legitimate and encouraging the user to trust the process without suspicion.
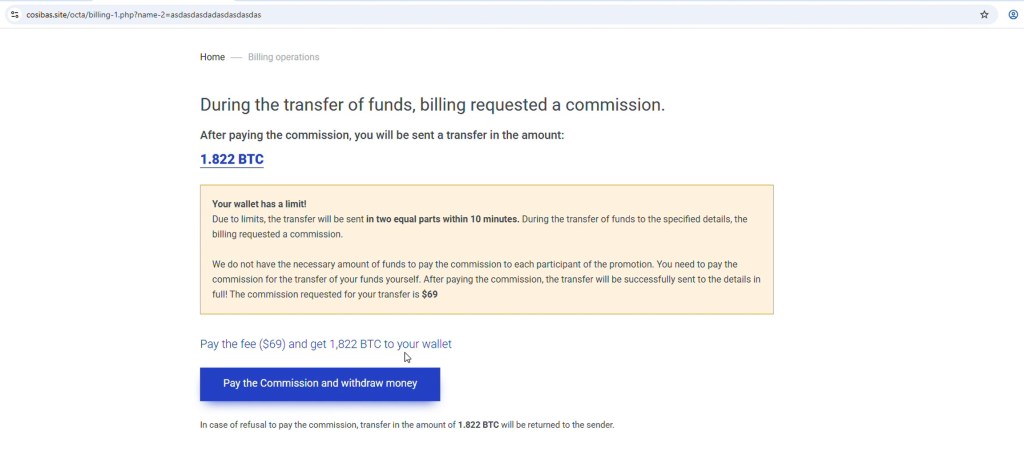
4. Commission Justification
Before allowing any withdrawal, the platform introduces an additional requirement in the form of a commission fee of around $69, accompanied by an explanation about wallet limits and transfer rules. This step is designed to appear reasonable and procedural, giving the impression that the fee is a standard part of the process while subtly nudging the user to make a payment in order to access the supposed funds.
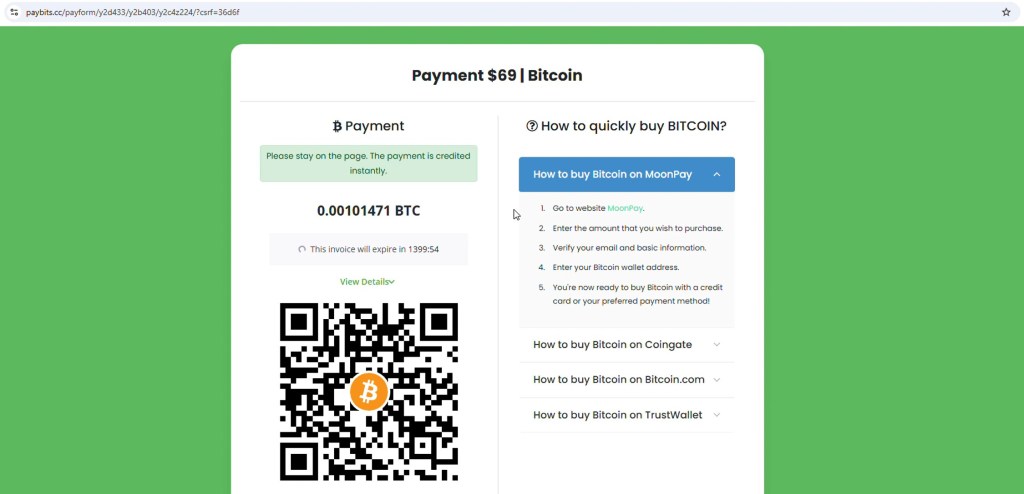
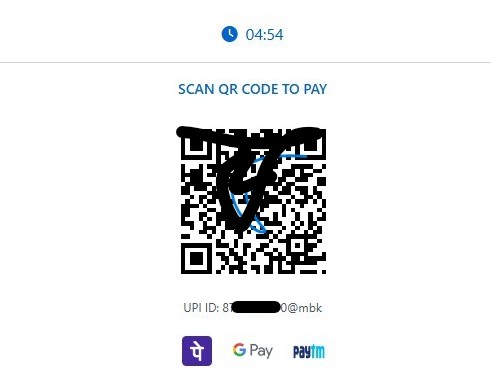
5. Payment Page
Just like the initial flow, the process ultimately leads to a familiar payment stage, presenting a Bitcoin payment request along with a QR code and a wallet address for convenience. An expiry timer is also displayed to create urgency, pressuring the user to act quickly and complete the payment without taking the time to question the legitimacy of the request.
What stands out is how the attackers reuse the same core scam but change the entry point.
I also looked into related activity on URLScan and found similar lures being actively scanned in the last couple of days, which indicates that this is not a one off campaign but something currently active and evolving.
Indicators of Compromise (IOCs)
URLs
Along with the observed infrastructure, I checked domain registration timelines, which further indicate that this campaign is relatively recent and actively being used.
- cosibas[.]site – Registered on 2026-01-30
- paybits[.]cc – Registered on 2026-02-02
hxxps://yandex[.]com/poll/PdZ7vgekGrNakuXZcpiB6b
hxxps://yandex[.]com/poll/GjSFvwyKcmEMXpzm6yDExc
hxxps://cosibas[.]site/bloc/anketa-sent.html
hxxps://cosibas[.]site/octa/
hxxps://paybits[.]cc/payment/