Analysis of a Suspicious “Eternl Desktop” MSI Installer Dropping LogMeIn Resolve
Overview
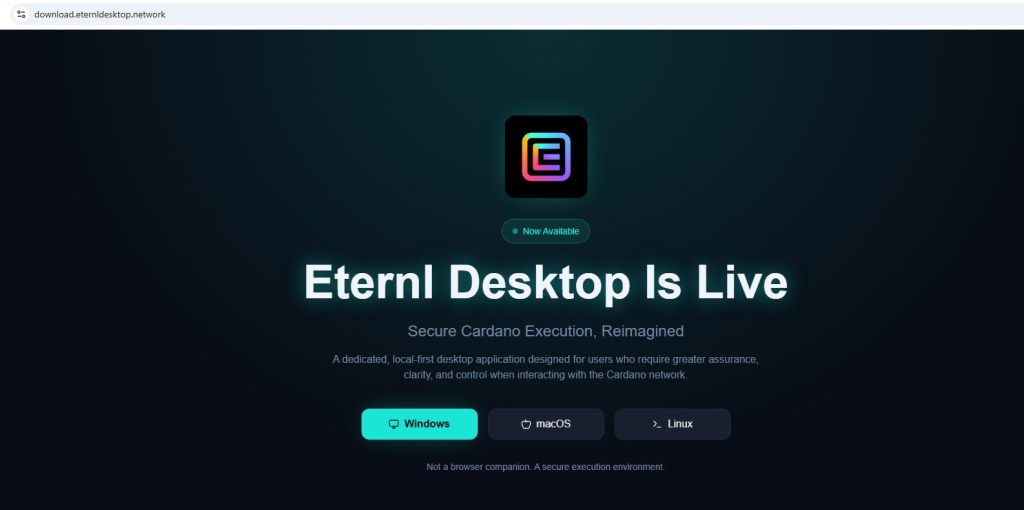
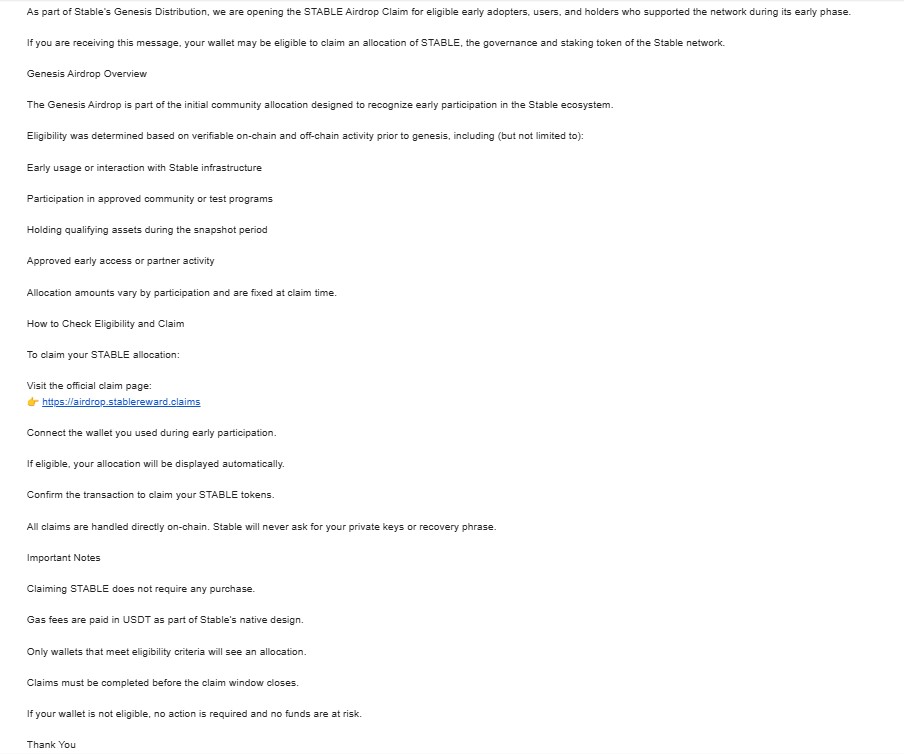
A professionally written announcement email titled “Eternl Desktop Is Live — Secure Execution for Atrium & Diffusion Participants” is currently circulating within the Cardano community.
At first glance, the email appears legitimate and well aligned with Cardano’s governance narrative promoting security, decentralization, and staking incentives. However, deeper inspection of the download mechanism and installer behavior raises significant red flags.
Email Social Engineering Highlights
The email leverages high trust messaging and ecosystem specific incentives.
The email strategically references Atrium and the Diffusion Staking Basket to establish legitimacy within the Cardano ecosystem, while also making enticing claims of NIGHT and ATMA token rewards to drive user interest. It reinforces trust by emphasizing “local-first, non-browser signing,” positioning the application as a more secure alternative to browser based wallets. The overall messaging maintains a polished, professional tone with no visible spelling or grammatical issues, lending credibility to the communication. This is capped with a strong, authoritative call to action “Eternl Desktop is where Cardano decisions are finalized.” designed to create urgency and frame the software as an essential tool for serious Cardano participants.
Download Infrastructure Red Flags
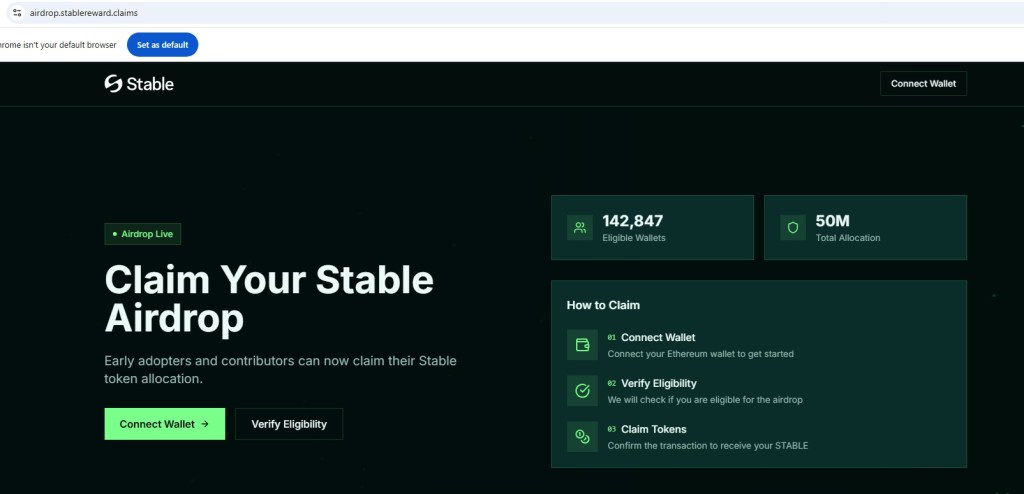
The provided download URL, hxxps://download[.]eternldesktop[.]network, raises immediate concerns, as the domain appears to be newly created and lacks any established historical reputation. There is no independent verification or announcement from official, well known Eternl communication channels to validate its legitimacy. Additionally, the software is distributed as a direct MSI installer without publicly available checksums, digital signature transparency, or formal release notes, preventing users from independently verifying the integrity and authenticity of the installer before execution.
New infrastructure + wallet software + MSI installer is a high-risk combination.
Domain Information
MSI Installer Analysis
File Name: Eternl.msi
File Size: 23.3MB
File Type: Windows Intaller (MSI)
Hash: 8fa4844e40669c1cb417d7cf923bf3e0
Title: LogMeIn Resolve Unattended
Comments: LogMeIn Resolve Unattended v1.30.0.636
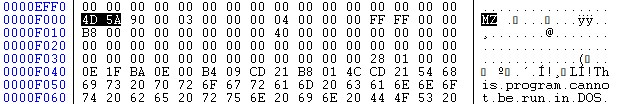
Using CFF Explorer, I identified an embedded executable within the MSI file. I then used LessMSI to extract the executable for further analysis.
Extracted Executable File
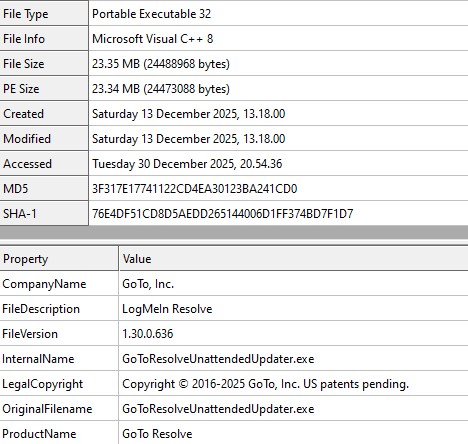
File Name: unattended-updater.exe
File Type: PE32
File Size: 23.35MB
Original File Name: GoToResolveUnattendedUpdater.exe
File Hash: 3f317e17741122cd4ea30123ba241cd0
File Description: LogMeIn Resolve
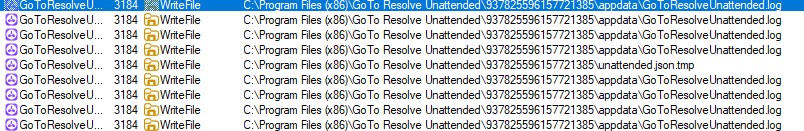
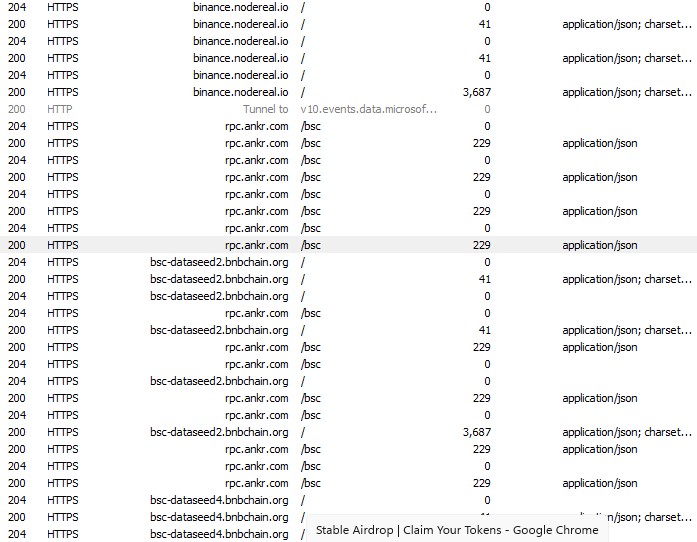
During dynamic analysis, the sample was observed writing log files and JSON artifacts to disk.
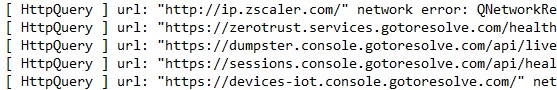
It also tried to connect to below domains.
- hxxt://ip.zscaler.com
- hxxt://zerotrust.services.gotoresolve.com
- hxxt://dumpster.console.gotoresolve.com/api/live
- hxxt://sessions.console.gotoresolve.com
- hxxt://devices-iot.console.gotoresolve.com/
- hxxps://devices.console.gotoresolve.com/properties
- hxxps://applet.console.gotoresolve.com
- hxxps://custombranding.console.gotoresolve.com
The executable is placed within a uniquely identified folder created under “C:\Program Files (x86)\GoTo Resolve Unattended“. All executables, along with JSON configuration files related to the RMM setup, are stored in this directory.
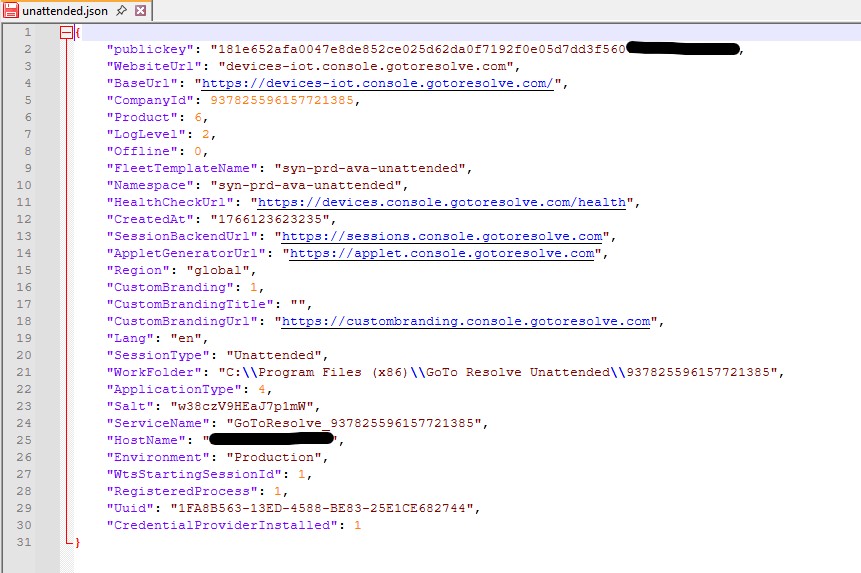
The unattended.json configuration file enables unattended access, allowing a technician to connect to the remote system without the end user being physically present.
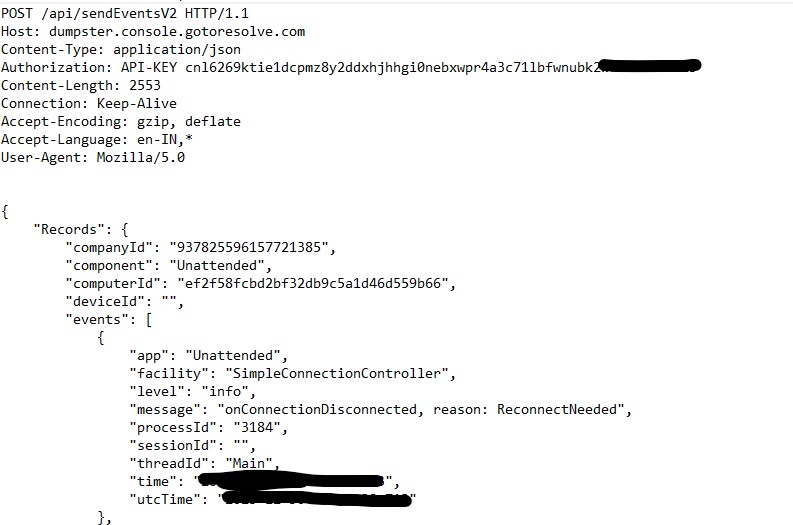
The application attempts to connect to hxxps://dumpster.console[.]gotoresolve[.]com/api/sendEventsV2 to transmit event information in JSON format. The connection fails, and the application retries the request multiple times.
Why This Is Concerning
This behavior is concerning because Remote Monitoring and Management (RMM) tools inherently provide powerful capabilities such as remote command execution, system monitoring, persistent access, and unattended control. While legitimate in enterprise environments, these features are frequently abused by threat actors during initial access operations, particularly in crypto themed malware campaigns and fake wallet or airdrop lures, where RMM software is leveraged to establish long-term post exploitation persistence on compromised systems.
While LogMeIn Resolve itself is a legitimate product, its silent delivery inside a wallet installer is not legitimate behavior.
Detection Summary
- Flagged as PUA / Riskware
- Behavioral indicators consistent with remote management agents
- Not a known component of any official Eternl wallet release
Threat Assessment
| Indicator | Risk |
| Newly registered download domain | High |
| MSI installer for wallet software | High |
| Drops RMM tool | Critical |
| PUA classification | Confirmed |
HIGHLY SUSPICIOUS – DO NOT INSTALL
This campaign exhibits multiple overlapping indicators consistent with supply-chain abuse and trojanized wallet distribution, combined with pre positioning techniques that leverage RMM tools to establish persistent access. Together, these behaviors suggest preparation for potential follow on activity, including future credential harvesting or cryptocurrency wallet compromise.
Indicators of Compromise (IOCs)
Domains:
- download[.]eternldesktop[.]network
Files
- etrnl.msi
- unattended-updater.exe
Product Identifiers
- LogMeIn Resolve
- GoTo Resolve
Hash
- 8fa4844e40669c1cb417d7cf923bf3e0
- 3f317e17741122cd4ea30123ba241cd0
This campaign demonstrates how crypto governance narratives are increasingly weaponized to distribute covert access tooling under the guise of professional software.