Overview
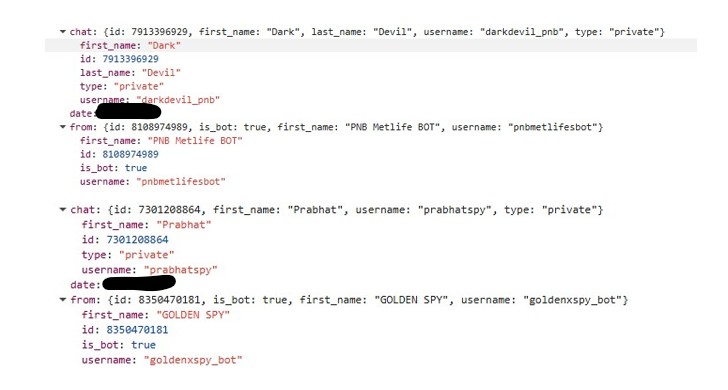
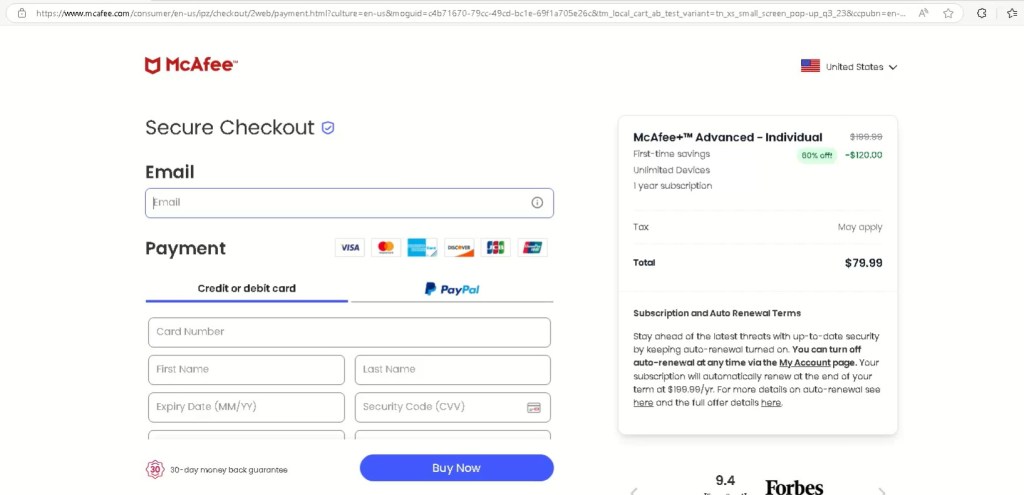
Over the past few weeks, I have been tracking a credential harvesting campaign that repeatedly abuses newly registered *.contractors domains to deliver Gmail and Microsoft 365/Outlook phishing pages.
While the social engineering lures vary including ICANN email verification, document sharing, and account security prompts. The underlying infrastructure, tooling, and execution flow remain consistent
Based on analysis of the phishing HTML, JavaScript, and runtime behavior, this activity can be attributed with high confidence to the Tycoon 2FA phishing kit, based on its distinctive MFA aware execution flow, client side obfuscation, and anti-analysis tradecraft.
This attribution is supported by distinctive Tycoon specific client side tradecraft, including MFA aware flows, advanced anti-analysis logic, and encrypted runtime loaders, as shown below.
Technical Evidence Supporting Tycoon 2FA Attribution
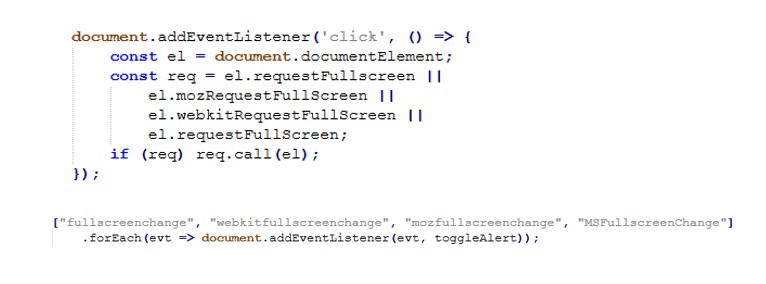
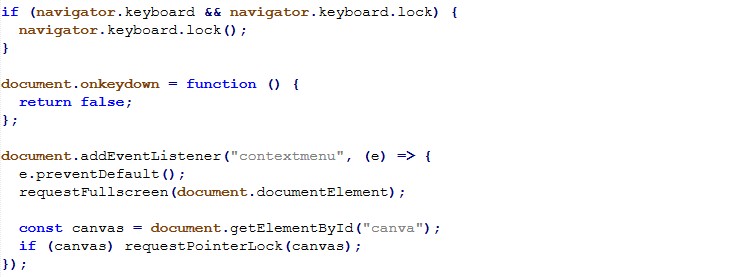
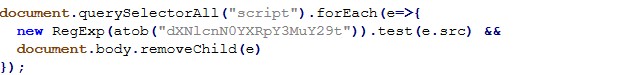
Analysis of the extracted HTML and JavaScript reveals multiple Tycoon 2FA specific behaviors that go beyond generic phishing kits.
Anti-Analysis & Sandbox Evasion Logic
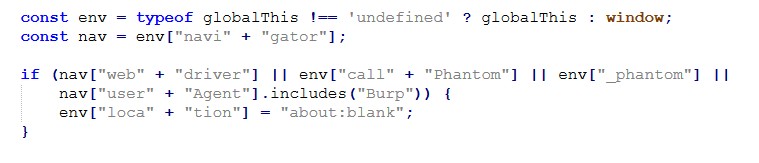
The phishing pages actively detect analysis environments and developer tools, immediately terminating execution or redirecting the user if detected:
Additional protections disable common inspection techniques:
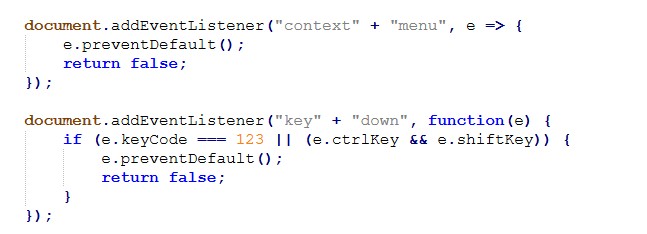
This multi-layered anti-analysis logic is a well known characteristic of Tycoon 2FA deployments, commonly observed across multiple campaigns leveraging this phishing-as-a-service (PhaaS) framework.
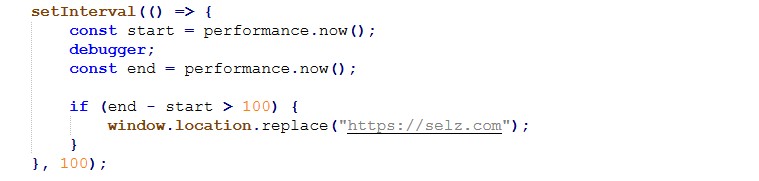
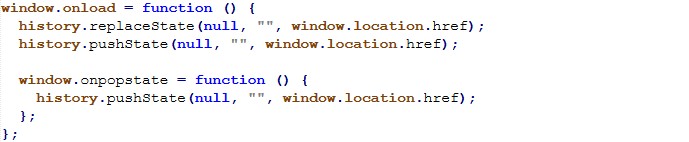
Runtime Debugger Detection & Forced Redirect
The kit also employs debugger timing detection to identify active inspection and force redirection:
This technique is specifically used by Tycoon based phishing frameworks to evade dynamic analysis and sandbox detonation.
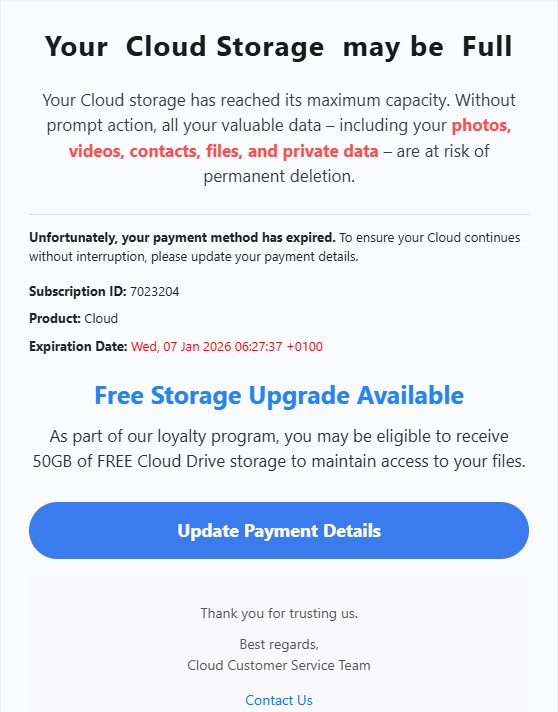
ICANN Email Verification Lure
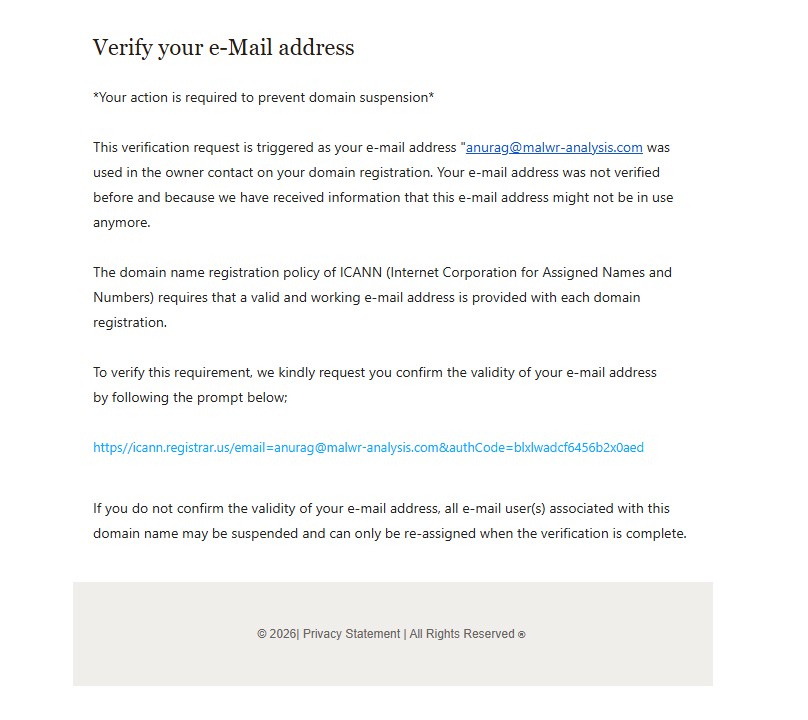
One of the more recent samples impersonates ICANN (Internet Corporation for Assigned Names and Numbers) and claims that the recipient’s email address must be verified to avoid domain-related disruption.
The email states that:
- The recipient’s email is listed as the owner contact for a domain
- The address is allegedly unverified or inactive
- Failure to verify may result in email suspension
A verification link is provided, styled to appear ICANN-related. However, hovering over the link reveals that it actually points to attacker controlled infrastructure hosted outside of any legitimate ICANN or registrar domain. In this case, the observed link resolved to
hxxps://recontact252.bluvias.de/572pectoral/$anurag@malwr-analysis.com
The URL embeds the recipient’s email address directly in the path, a common personalization technique used in targeted phishing campaigns to increase credibility and successful credential submission.
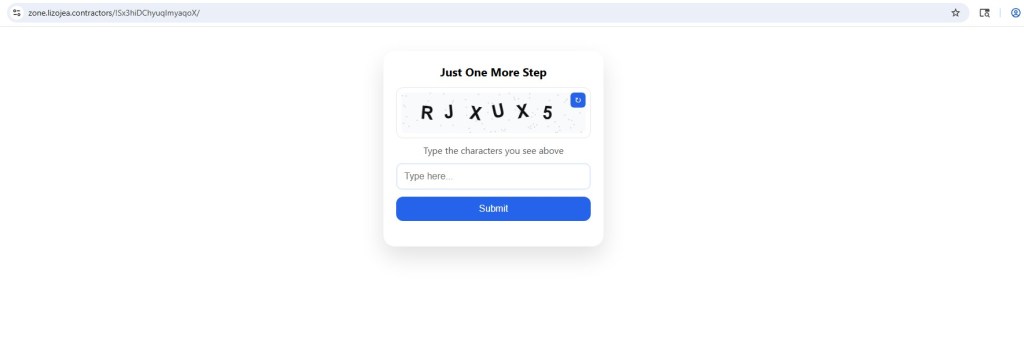
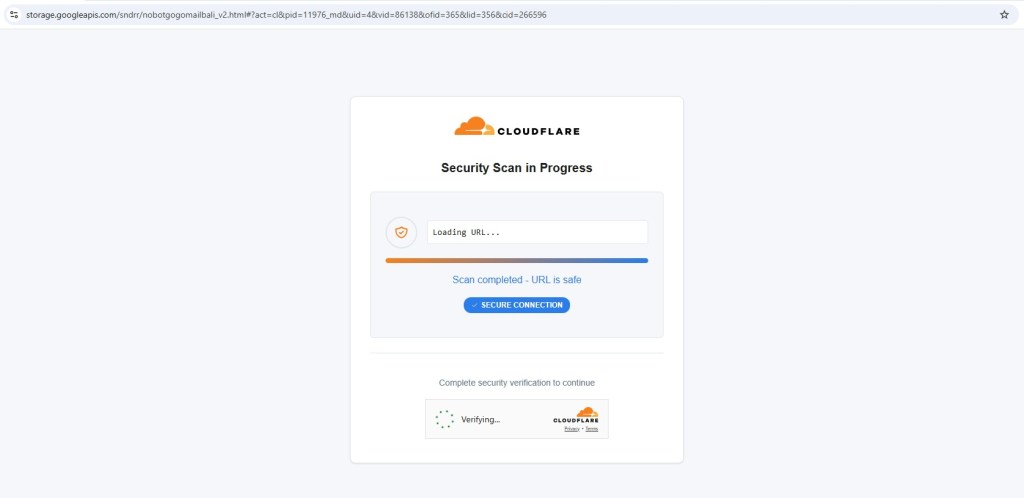
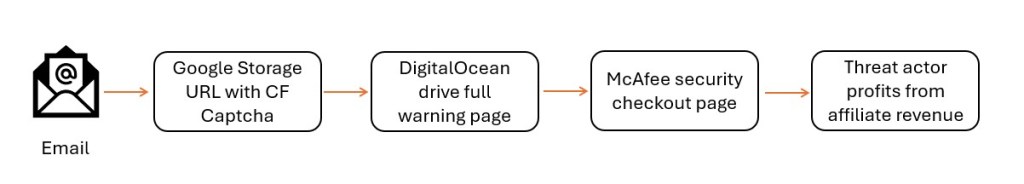
Redirection Flow: CAPTCHA as an Anti-Analysis Gate
Clicking the verification link does not immediately present a login page.
Instead, victims are routed through a fake CAPTCHA / “confirm you’re human” page, which serves as a deliberate execution delay.
This delay is important for two reasons:
- Automated sandbox services (e.g., URLScan) often complete scanning before the CAPTCHA stage is reached, meaning the actual phishing payload is never rendered during automated analysis.
- User interaction is required to proceed, filtering out non-human traffic and reducing detection rates.
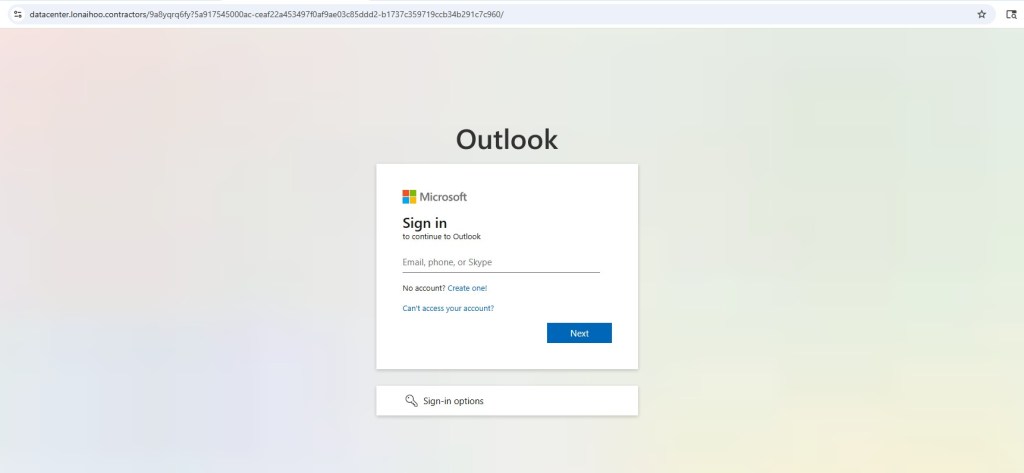
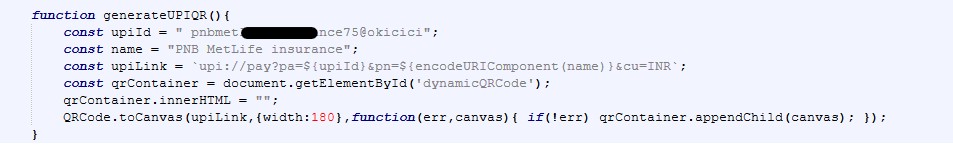
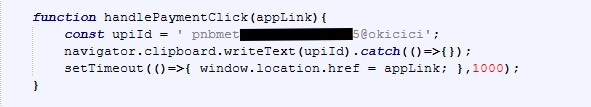
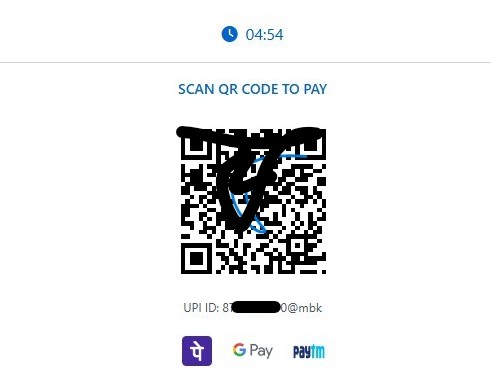
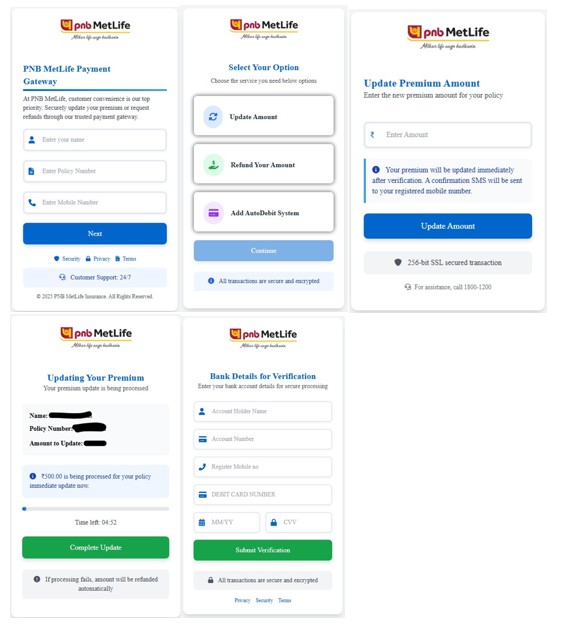
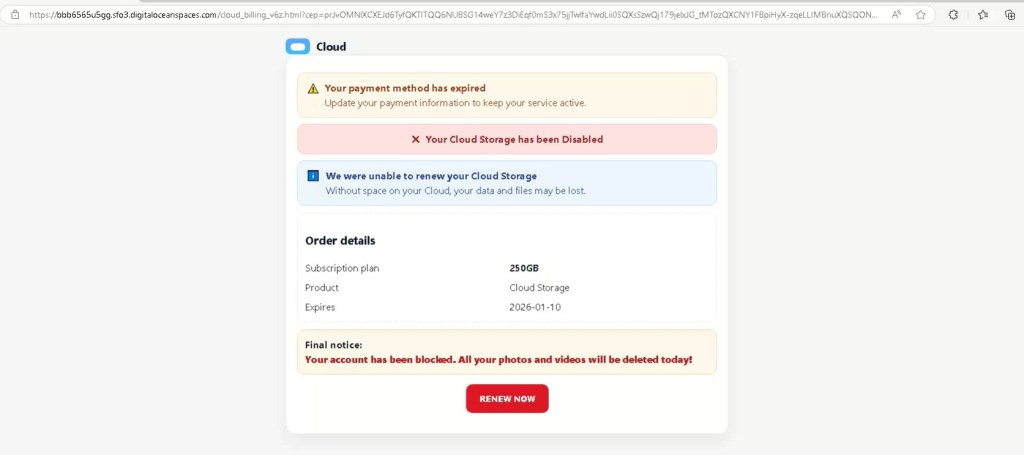
Final Payload: Gmail & Microsoft 365 Tycoon 2FA Lures
After CAPTCHA completion, victims are redirected to high-fidelity Gmail or Microsoft 365 / Outlook login pages, depending on the campaign variant.
Observed behaviors include:
- Accurate UI and branding replication
- Email address prefilled or dynamically referenced
- Transition into multi-step authentication flows
- MFA approval interception and credential capture
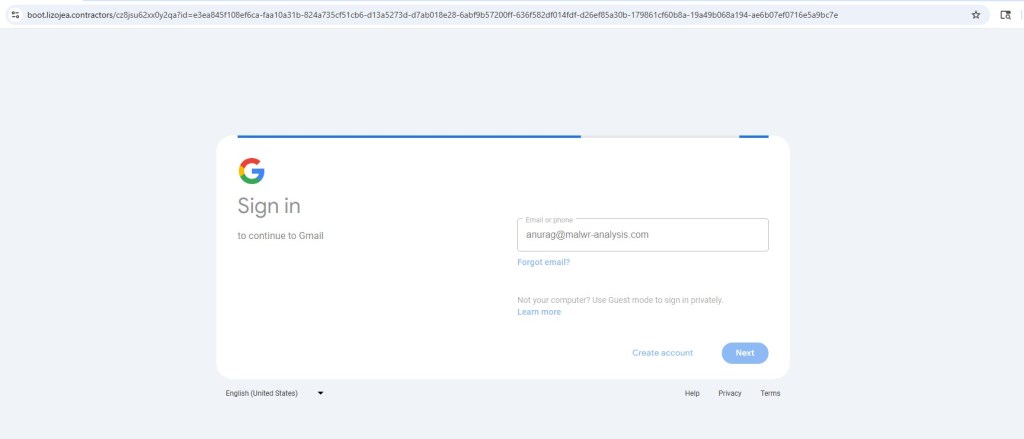
Despite branding differences, both lures share identical loader logic, obfuscation patterns, and runtime behavior, confirming they are part of the same Tycoon 2FA campaign.
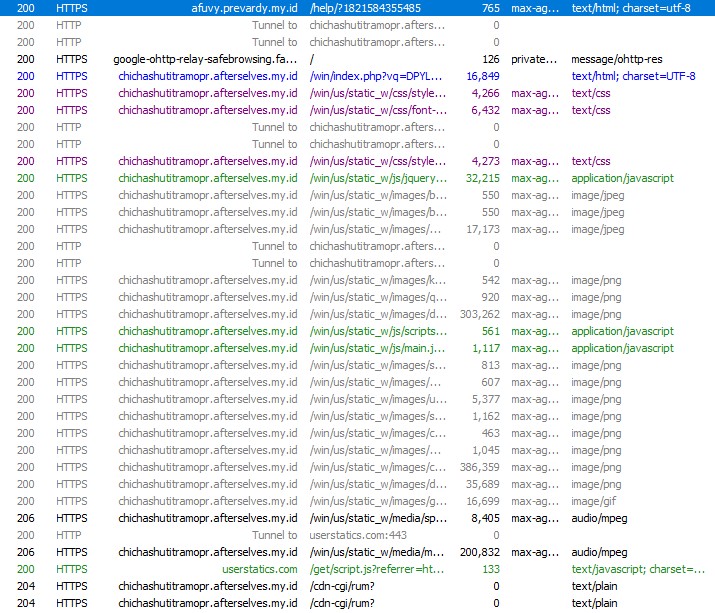
Infrastructure Reuse: *.contractors Domains
Across all observed samples, the campaign consistently abuses freshly registered .contractors domains, often using randomized subdomains and long URL paths.
Examples observed include:
Outlook
hxxps://datacenter.lonaihoo.contractors/i!2zDbFPEvdm/
hxxps://pytorch.hithomu.contractors/Hik3GWNtRtmoaf@Ul5FNuB3/$bmVzZS5ndW5lckBlZ29uemVobmRlci5jb20=
hxxps://bigbluebutton.seacrevea.contractors/nGPI9ensbX@Y/
hxxps://redoc.kaidaisoo.contractors/Yi@9yUWrVO/
hxxps://firewall.tiostemio.contractors/nu2ATGWco@GZ/
hxxps://pulumi.kaidaisoo.contractors/QBQG4CC@30W/
Gmail
hxxps://cdnedge.kirosoo.contractors/UyHX5Z5NJWj!i6VTZW5/
hxxps://bscscan.kirosoo.contractors/KQccgiv0@RRZ4xeCQMfRJbnT/
hxxps://copytrade.kirosoo.contractors/m8WqmrYb6lVk7C@9o1Yio/
hxxps://dist.draidatroo.contractors/4!OMtEFiKRQ/
hxxps://boot.lizojea.contractors
hxxps://hashid.draidatroo.contractors/ey!z5jV2w/
Benign Page
hxxps://ide.pishathi.contractors
hxxps://ide.niramio.contractors/
hxxps://js.hithomu.contractors/
hxxps://substack.wifupu.contractors/
hxxps://swap.lizojea.contractors/
hxxps://bandwidth.kioboumu.contractors/tO3v!7gw
hxxps://zip.lucadru.contractors/
Common characteristics observed across these campaigns include domains registered very recently, most notably on 07 January 2026 and 14 January 2026 along with randomized URL paths and identifiers designed to evade detection. Victim email addresses are embedded directly within the URLs to personalize lures and enable tracking.
Observed Evasion via Decoy Landing Pages
When analysis is detected or when execution fails, the infrastructure does not return an error page.
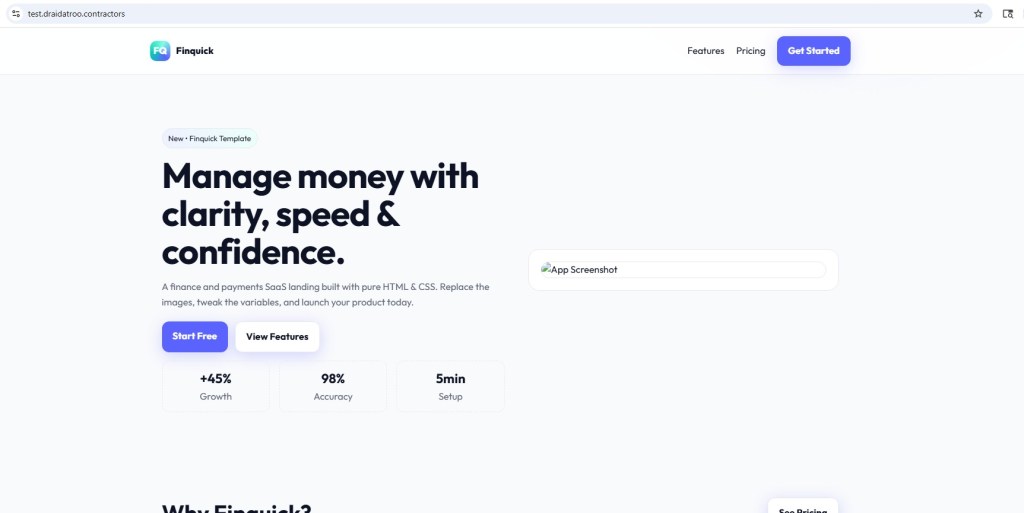
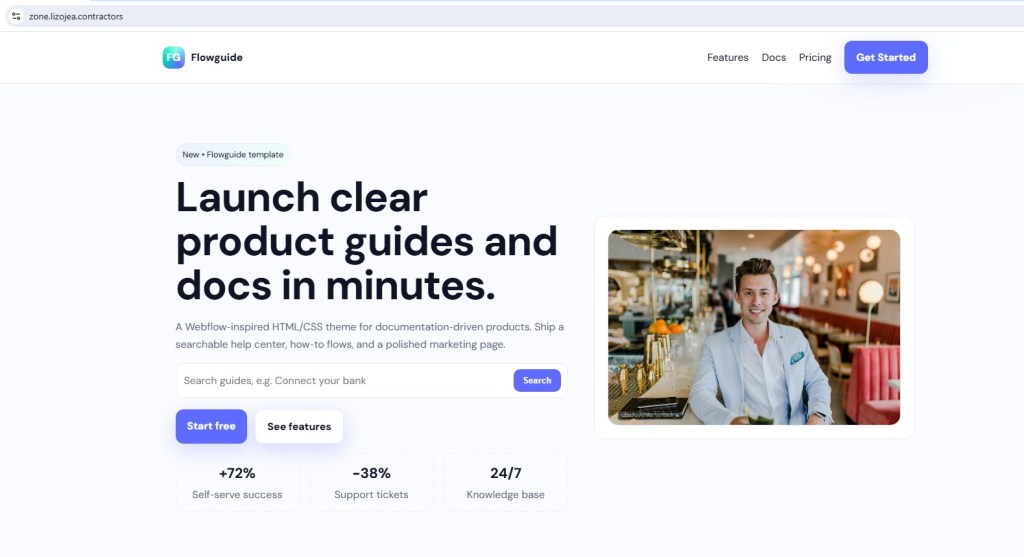
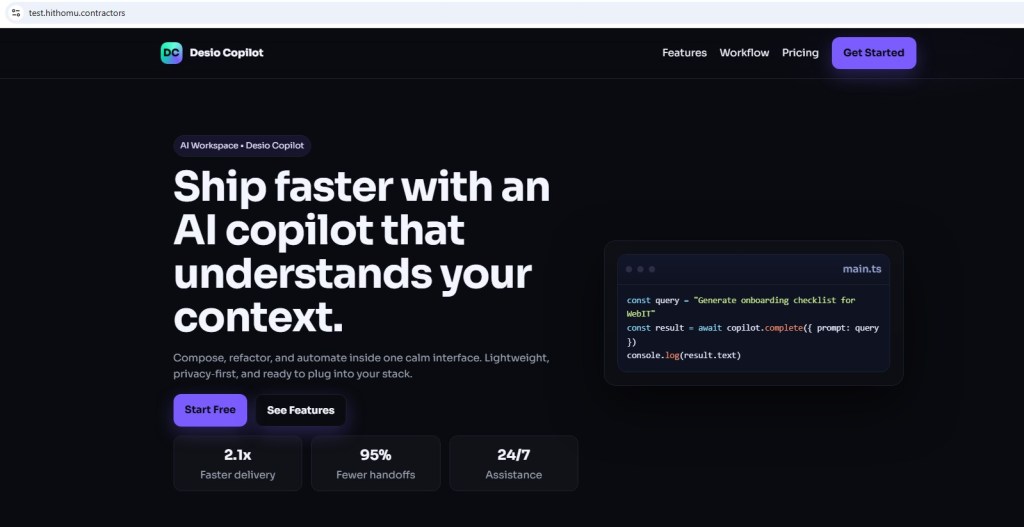
Instead, victims or scanners are redirected to to benign decoy landing page templates, including:
- Finquick
- Flowguide
- Desio Copilot
These templates act as decoy content, helping:
- Evade automated detection
- Reduce suspicion during manual review
- Prolong domain lifespan
This fallback behavior has been repeatedly observed in Tycoon-based phishing campaigns.
Campaign Scope: *.contractors Domains Observed on URLScan
During this investigation, I identified multiple .contractors domains associated with this campaign through URLScan submissions and pivoting.
A consolidated list of all observed .contractors domains, along with scan links and timestamps, will be provided below for reference and detection purposes.
https://urlscan.io/result/019c0245-d376-75f6-9cb1-61ea3d390d5b/
https://urlscan.io/result/019c03c8-00f8-718f-b45a-af4fd080112e/
https://urlscan.io/result/019c046b-012c-740e-b96a-cf111e169b0a/
https://urlscan.io/result/019bc8b1-63f4-765c-96a1-46d406426c1e/
https://urlscan.io/result/019bfa8b-127e-7718-abad-b1390d3c9e08/
https://urlscan.io/result/019bec78-0eaf-70c9-bbda-d839444f8120/
https://urlscan.io/result/019bfeea-9343-713f-8cf8-cd62c3f10a01
https://urlscan.io/result/019bd770-5232-7789-807b-127ca1422e2b
https://urlscan.io/result/019c0616-3df5-7178-a87a-f80358df27b0/
This activity represents a coordinated, MFA aware phishing campaign, not isolated incidents.
While this analysis identifies multiple .contractors domains and consistent infrastructure patterns, it is likely that additional domains and variants are in use beyond those documented here. The findings in this post are based on artifacts and infrastructure observed within the scope of URLScan, and the full extent of the campaign may be broader.
Additional Infrastructure Observed
During continued investigation, I identified additional, distinct domains serving the same Microsoft 365 / Outlook Tycoon 2FA lure, indicating broader infrastructure reuse beyond the initially observed .contractors clusters.
These domains exhibit the same execution flow, CAPTCHA gating, MFA-aware login sequence, and post-authentication behavior, confirming they are part of the same phishing operation, rather than unrelated or opportunistic reuse.
- hxxps://payroll.thaiciowea.ceo/xT5aq!K5d/
- hxxps://remny.gaistaicrai.digital/qIgia8Jr7LEa8W!/
- hxxps://uiux.founiofai.biz.id/9DVIPQ7ac0YOGnRqoI!yvk/
- hxxps://sharepoint.fadritou.digital/v5AcJPLFbVy0qjcQ02fBxc@T0/
- hxxps://nginxproxy.vathafro.my.id/mg81MII45!WSGyejanSUmrLuO/
- hxxps://sync.traipeapu.biz.id/wnqhpE0@HHSAsI9Fd98/
- hxxps://hoppscotch.soteafoo.help/@lZHMNWUTbLcUZL9/
- hxxps://bitbucket.yoohuyea.ru.com/8qjla77OTNK2V@8v6aqp0T/
- hxxps://firebase.leanegea.my.id/ISvY22wws0X@S21900cB2/
- hxxps://kotlin.lifricra.ceo/rankbaEl@ZKQoe8tS/
- hxxps://mongoose.toubeasea.5g.in/DceUas3sJx6hhSi8!fHBS/
- hxxps://metamask.chiochaishi.my.id/iPrDazXUE84OLAsqPm1@B/
- hxxps://get.treloostu.biz.pl/e3!1TWPrEIZ0uGEBhhyEU7Hy/
- hxxps://folder.cidoofo.digital/pAlbY@6wwJl1Wi7z/$
- hxxps://dao.treeformqackaging.com/4kxgSg5!NaGE/
- hxxps://textarea.zuboufoocrai.icu/MkHYM0@UoWDV/
- hxxps://hash.noustocu.business.in/@jQylPjuX/
Note on Campaign Scale
The domains and infrastructure documented above represent only a subset of the total activity observed during this investigation. While many additional domains and variants were identified, listing all of them would significantly expand the scope of this post.
For the purposes of this write-up, I will leave the analysis here, focusing on representative samples that clearly demonstrate the campaign’s tradecraft and attribution.